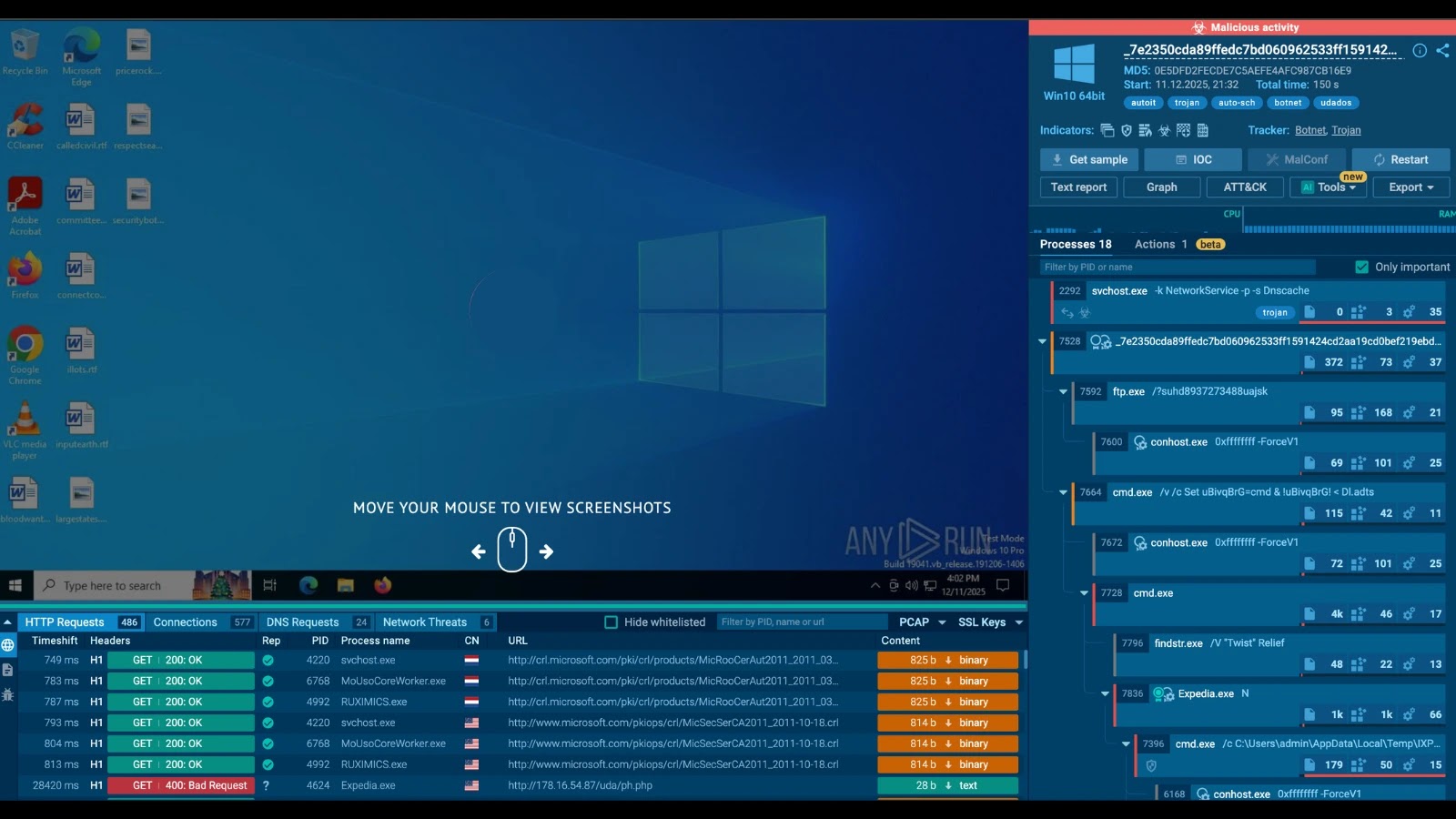
A newly recognized botnet malware household, dubbed “Udados,” has emerged as a big risk to the Expertise and Telecommunications sectors, orchestrating high-volume HTTP flood Distributed Denial-of-Service (DDoS) assaults.
In accordance with ANY.RUN sandbox evaluation, the botnet leverages contaminated hosts to execute sustained denial-of-service campaigns designed to disrupt enterprise continuity by overwhelming goal servers with legitimate-looking visitors.
The Udados malware operates by establishing communication with a Command and Management (C2) server to obtain assault directions.
Contaminated hosts ship structured JSON knowledge to the C2, together with detailed system metadata: person ID (Uid), process execution standing (St), bot model (Bv), and privilege degree (Priv). This telemetry permits the operator to handle the botnet’s assets successfully.
Upon check-in, the C2 server responds with particular assault instructions. The first directive noticed is !httppost, which triggers the DDoS module. This command contains parameters for the assault length (e.g., 888 seconds), the variety of concurrent threads (e.g., 88), and a Base64-encoded payload containing random knowledge.
Udados Botnet
Using HTTP POST requests permits the assault visitors to mix seamlessly with professional internet visitors, making detection and mitigation considerably tougher for community defenders.
Infrastructure and Community Indicators
The botnet’s infrastructure is hosted inside Autonomous System AS214943, also called RAILNET. This community has not too long ago gained a status as a haven for malicious exercise; latest intelligence studies point out that RAILNET has hosted infrastructure for over 30 distinct malware households in late 2025, together with main threats like Remcos and Amadey.
The precise C2 server recognized on this marketing campaign is positioned at IP handle 178.16.54[.]87.
The malware communicates by way of the URI /uda/ph.php, which serves as a important indicator for community monitoring. Defenders can detect potential infections by inspecting outbound HTTP visitors for this particular path and the attribute JSON parameters (uid, st, msg, tid) within the request physique.
Organizations are suggested to behave quick and block visitors to the recognized C2 infrastructure and monitor for the next indicators:
TypeValueSHA2567e2350cda89ffedc7bd060962533ff1591424cd2aa19cd0bef219ebd576566bbSHA256770d78f34395c72191c8b865c08b08908dff6ac572ade06396d175530b0403b8 IPv4178.16.54[.]87 (Hosted on RAILNET)Domainryxuz[.]com URI Path/uda/ph.php
Community directors also needs to examine short-term spikes in outbound HTTP visitors from particular person hosts, as this habits typically precedes the high-volume flood orchestrated by the C2.
Establish cyber threats early to behave quick With Interactive Sandbox => Strive Now