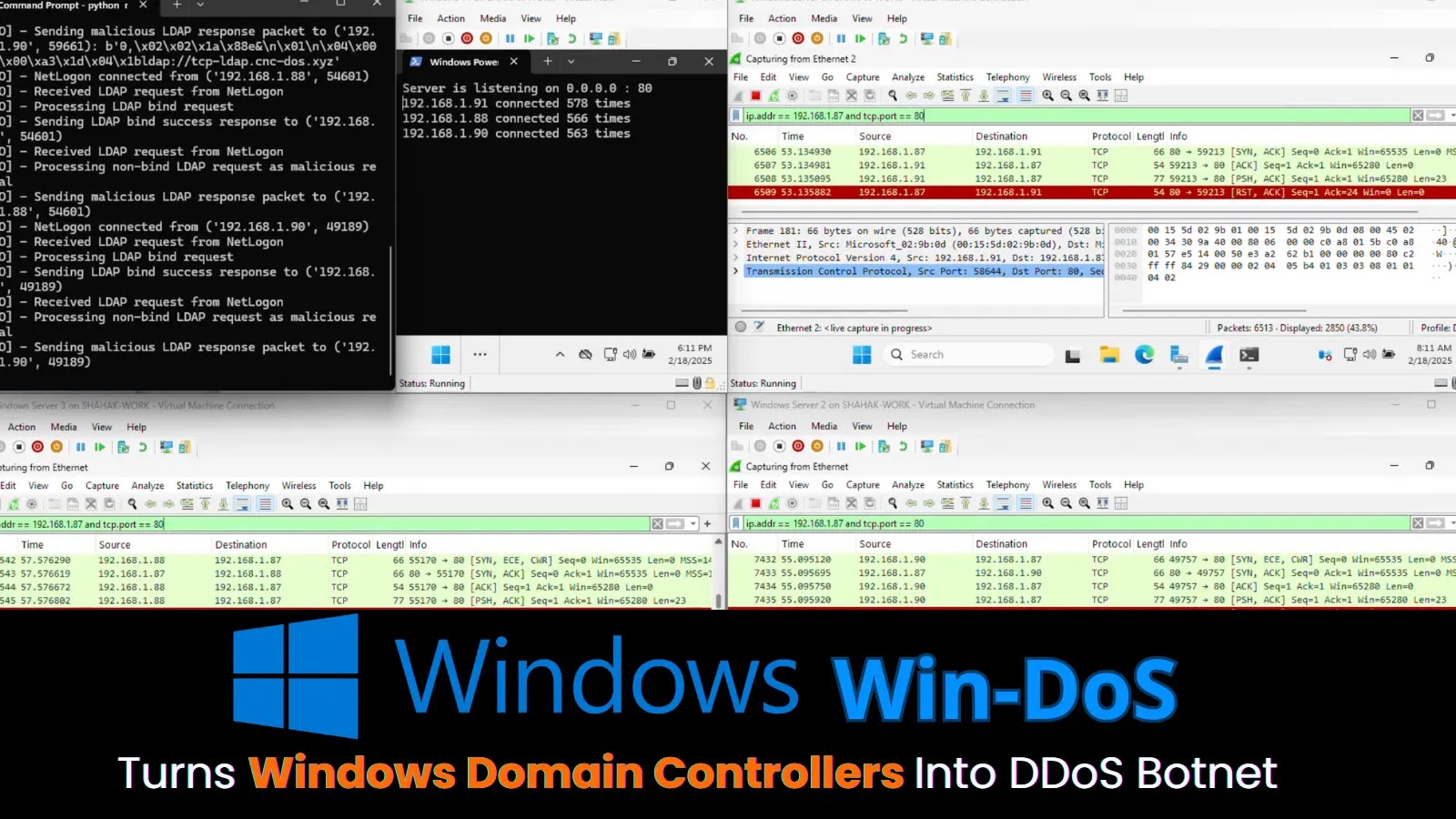
LAS VEGAS — On the DEF CON 33 safety convention, researchers Yair and Shahak Morag of SafeBreach Labs unveiled a brand new class of denial-of-service (DoS) assaults, dubbed the “Win-DoS Epidemic.”
The duo offered their findings, which embrace 4 new Home windows DoS vulnerabilities and one zero-click distributed denial-of-service (DDoS) flaw.
The found flaws, all of that are categorized as “uncontrolled useful resource consumption,” embrace:
CVE-2025-26673 (CVSS 7.5): A high-severity DoS vulnerability in Home windows LDAP.
CVE-2025-32724 (CVSS 7.5): A high-severity DoS vulnerability in Home windows LSASS.
CVE-2025-49716 (CVSS 7.5): A high-severity DoS vulnerability in Home windows Netlogon.
CVE-2025-49722 (CVSS 5.7): A medium-severity DoS vulnerability within the Home windows Print Spooler, which requires an authenticated attacker on an adjoining community.
The analysis demonstrates how attackers can crash any Home windows endpoint or server, together with important Area Controllers (DCs), and even weaponize public DCs to create an enormous DDoS botnet.
“We current “Win-DoS Epidemic” – DoS instruments exploiting 4 new Win-DoS and one Win-DDoS zero-click vulns! Crash any Home windows endpoint/server, together with DCs, or launch a botnet utilizing public DCs for DDoS. The epidemic has begun” Researchers stated.
The Risks of DoS on Area Controllers
Area Controllers are the spine of most organizational networks, dealing with authentication and centralizing consumer and useful resource administration.
A profitable DoS assault in opposition to a DC can paralyze a whole group, making it unimaginable for customers to log in, entry assets, or carry out each day operations.
The researchers’ work builds on their earlier discovery, the LdapNightmare vulnerability (CVE-2024-49113), which was the primary public DoS exploit for a Home windows DC. The brand new findings develop this menace considerably, transferring past simply LDAP to abuse different core Home windows companies.
A New Botnet Harnessing Public Infrastructure
Probably the most alarming discovery is a novel DDoS approach, which the researchers have named Win-DDoS. This assault leverages a flaw within the Home windows LDAP consumer’s referral course of.
In a traditional operation, an LDAP referral directs a consumer to a distinct server to meet a request. Yair and Morag found that by manipulating this course of, they may redirect DCs to a sufferer server, and crucially, they discovered a strategy to make the DCs relentlessly repeat this redirection.
This habits permits an attacker to harness the immense energy of tens of hundreds of public DCs worldwide, turning them into an enormous, free, and untraceable DDoS botnet.
The assault requires no particular infrastructure and leaves no forensic path, because the malicious exercise originates from the compromised DCs, not the attacker’s machine.
This method represents a major shift in DDoS assaults, because it permits for high-bandwidth, high-volume assaults with out the everyday prices or dangers related to organising and sustaining a botnet.
Abusing RPC for System Crashes
Along with the DDoS botnet, the researchers targeted on the Distant Process Name (RPC) protocol, which is a elementary part of Home windows for inter-process communication.
RPC servers are ubiquitous within the Home windows surroundings and sometimes have broad assault surfaces, particularly those who don’t require authentication.
The SafeBreach group discovered that by abusing safety gaps in RPC bindings, they may repeatedly hit the identical RPC server from a single system, successfully bypassing customary concurrency limits.
This technique allowed them to find three new zero-click, unauthenticated DoS vulnerabilities that may crash any Home windows system—servers and endpoints alike.
In addition they discovered one other DoS flaw that may be exploited by any authenticated consumer on the community.
These vulnerabilities break frequent assumptions that inside techniques are secure from abuse with no full compromise, demonstrating that even a minimal presence on a community can be utilized to trigger widespread operational failure.
The researchers have launched a set of instruments, collectively known as “Win-DoS Epidemic,” that exploit these 5 new vulnerabilities. The instruments can be utilized to crash any unpatched Home windows endpoint or server remotely, or to orchestrate a Win-DDoS botnet utilizing public DCs.
These findings underscore the important want for organizations to reassess their menace fashions and safety postures, notably relating to inside techniques and companies like DCs.
Microsoft has since launched patches for the LdapNightmare vulnerability, however the brand new discoveries spotlight the continued want for vigilance and steady safety validation.
Discover this Information Fascinating! Comply with us on Google Information, LinkedIn, and X to Get Prompt Updates!