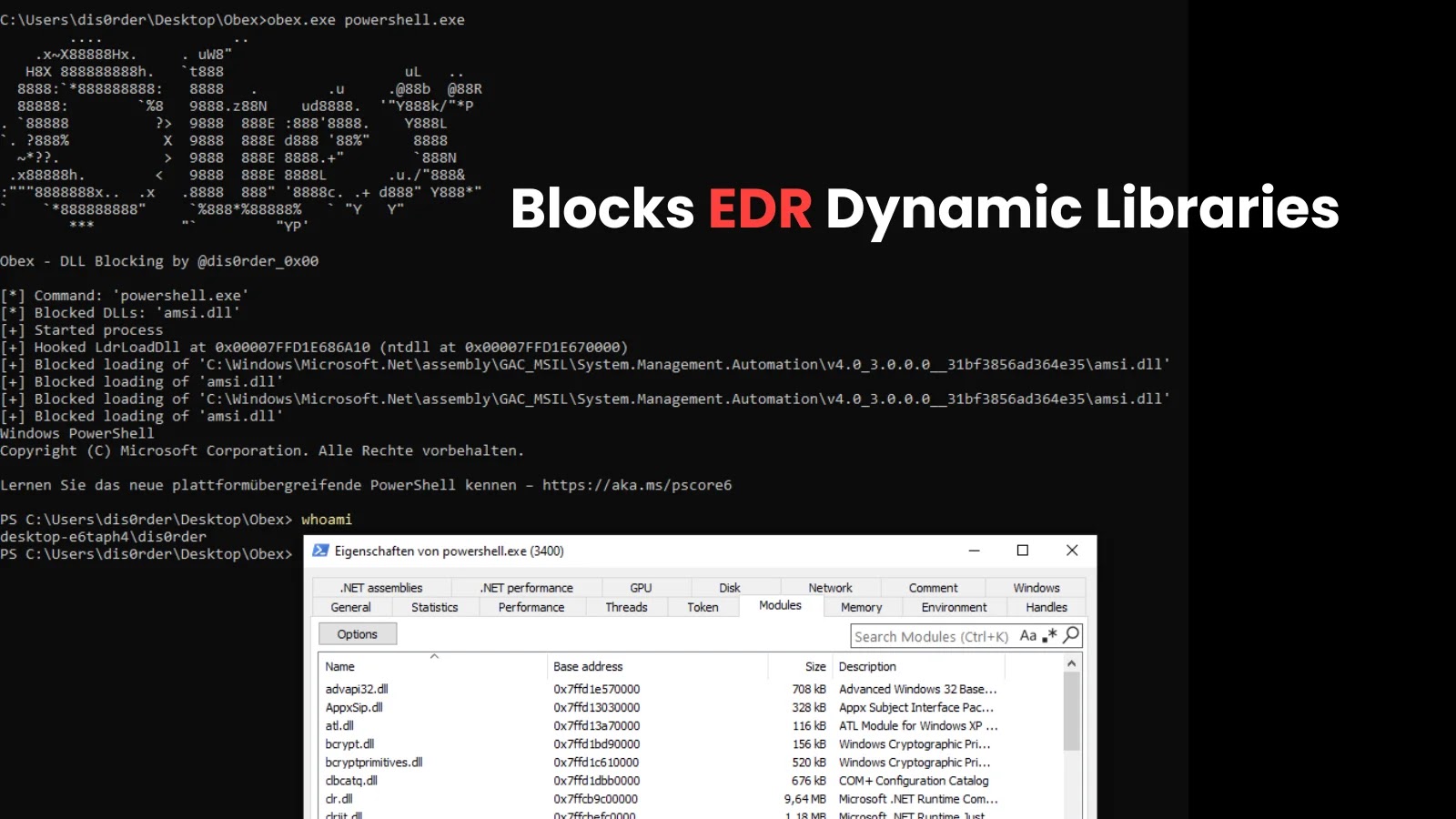
The nmapUnleashed tool, introduced by developer Sharkeonix in January 2026, offers significant advancements for network scanning and auditing. This open-source command-line interface (CLI) wrapper enhances the traditional Nmap tool, providing penetration testers with improved efficiency and ease of use.
Key Features of nmapUnleashed
nmapUnleashed, also known as ‘nu’, is designed to augment Nmap’s capabilities by introducing multithreading. By default, it enables up to four parallel scans, significantly expediting the scanning process across extensive networks. The tool maintains complete compatibility with Nmap, ensuring seamless integration into existing workflows.
An interactive dashboard is another notable addition, offering real-time tracking of scan progress. This dashboard includes features for monitoring active, queued, and completed scans, alongside network throughput alerts to prevent any potential bandwidth issues. Users can also benefit from automatic scan timeouts and manual abort functions, with outputs merged into easily accessible formats like scans.xml and scans.html.
Advanced Target Specification and Presets
nmapUnleashed excels in target specification, supporting a wide range of identifiers such as IPs, CIDRs, hostnames, and files. Users can employ syntax for per-target parameters, allowing for precise control over scan configurations. The tool also supports exclusions via the -ex flag to refine target scopes.
Presets (-ps) are another efficiency booster, enabling the loading of predefined scan profiles from configuration files. This feature is particularly useful for repetitive scanning tasks. For comprehensive port and version detection, users might utilize a ‘basic’ preset with options like ‘-d -p- -A’.
Installation and Usage
Installing nmapUnleashed on Linux systems, such as Kali, is straightforward. After ensuring the presence of necessary dependencies like nmap, xsltproc, and grep, users can install it via pipx. The tool’s usage closely mirrors Nmap’s, allowing for intuitive adoption by professionals.
For instance, executing ‘nu -d -p- -A scanme.nmap.org’ initiates an aggressive scan. More advanced commands, like ‘nu -th 8 -kt 120 -nwr 1000 -p- -sV scanme.nmap.org’, leverage multiple threads and include network warnings to optimize performance.
In the ever-evolving field of penetration testing, nmapUnleashed offers a substantial upgrade to the conventional Nmap tool. By blending familiarity with enhanced productivity features, it stands as a critical asset for cybersecurity professionals.