A newly found DLL hijacking vulnerability in Notepad++, the favored supply code editor, may enable attackers to execute arbitrary code on a sufferer’s machine.
Tracked as CVE-2025-56383, the flaw exists in model 8.8.3 and doubtlessly impacts all put in variations of the software program, placing hundreds of thousands of customers in danger.
The vulnerability permits a neighborhood attacker to realize code execution by planting a malicious DLL file in a location the place the appliance will load it. The sort of assault undermines the integrity of the appliance and can be utilized to ascertain persistence or escalate privileges on a compromised system.
PoC Exploit Launched
DLL (Dynamic Hyperlink Library) hijacking exploits the way in which Home windows purposes seek for and cargo required libraries. If an software searches for a DLL with out specifying a full path, it might look in a number of directories in a predefined order.
An attacker can place a malicious DLL with the identical identify as a reputable one in a listing that’s searched earlier than the precise library’s location. When the person launches the appliance, the malicious DLL is loaded and executed as a substitute of the meant one.
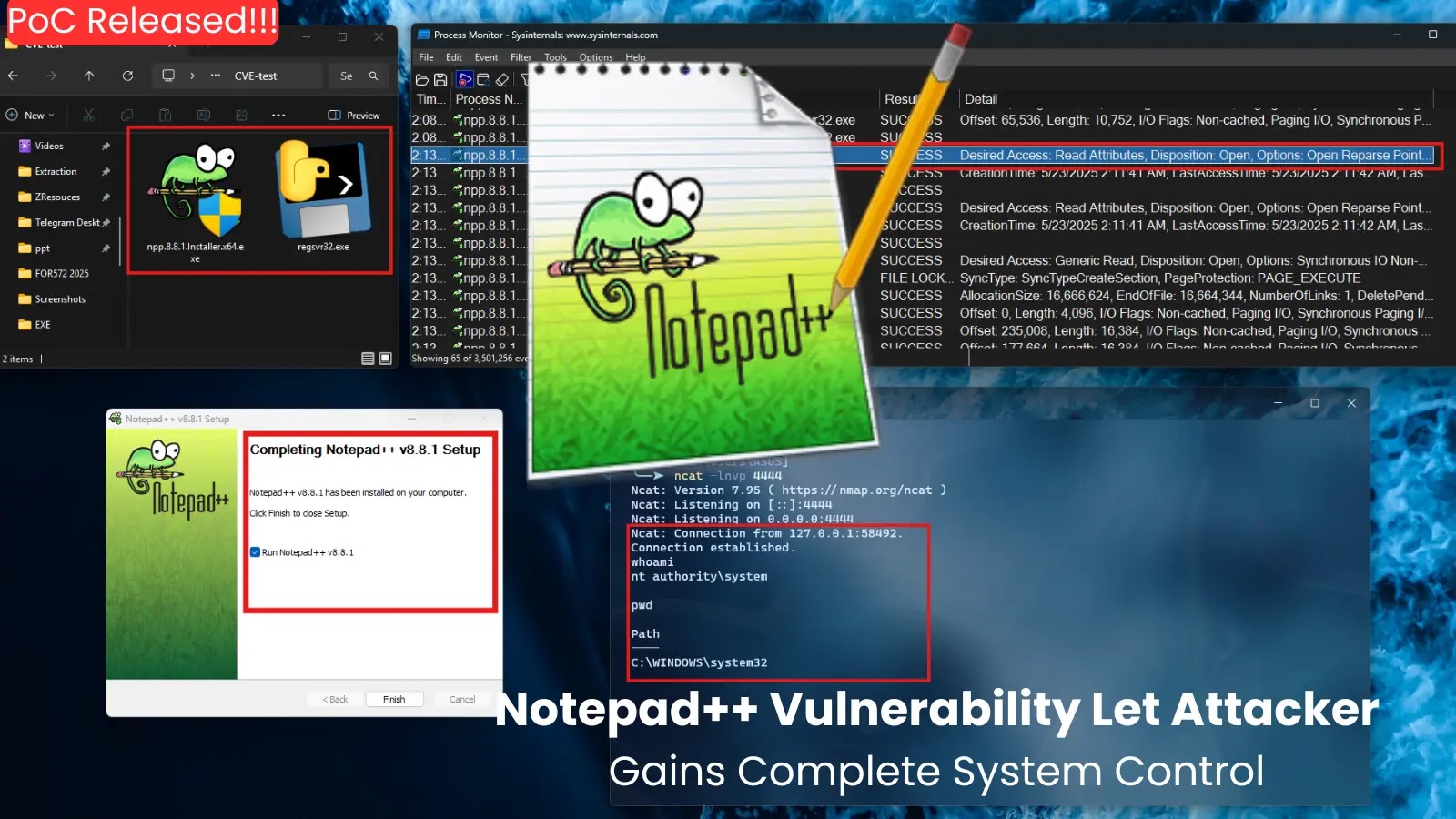
Within the case of Notepad++, the vulnerability will be exploited by concentrating on the DLLs related to its plugins. Based on the proof-of-concept, an attacker can exchange a plugin file, equivalent to NppExport.dll, situated within the Notepad++pluginsNppExport listing, with a custom-crafted malicious DLL.
To stay undetected and make sure the software continues to perform usually, the attacker can rename the unique DLL (e.g., to original-NppExport.dll) and have the malicious substitute ahead all reputable perform calls to it.
This method, generally known as proxying, makes the appliance’s conduct seem seamless to the person whereas the malicious payload executes within the background.
The supplied instance demonstrates this file substitute. The malicious NppExport.dll is considerably smaller than the original-NppExport.dll, indicating it incorporates completely different code.
Malicious File
Upon launching Notepad++.exe, the appliance masses the malicious DLL, resulting in the execution of the attacker’s code.
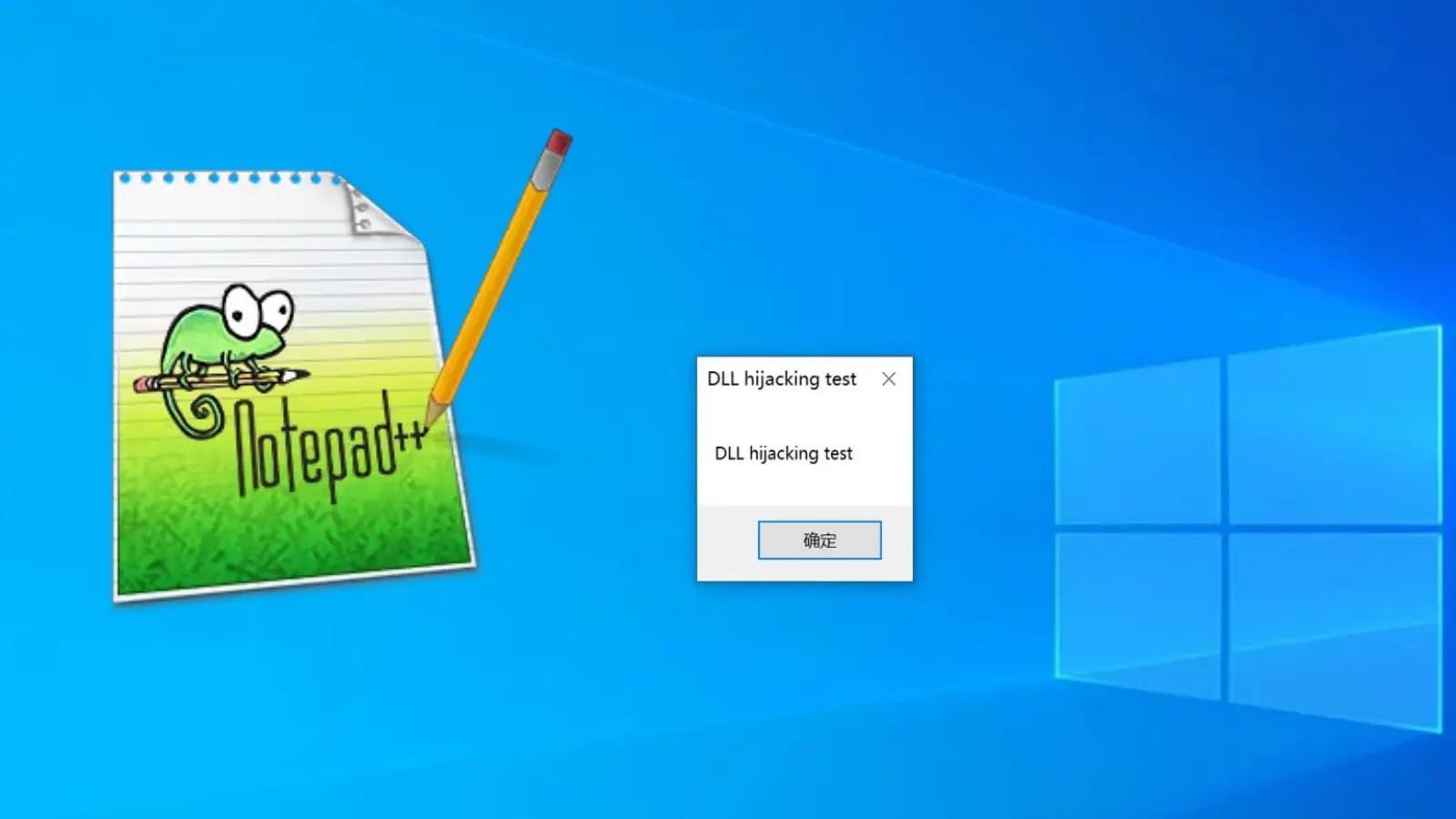
A profitable exploit was demonstrated by the looks of a check message field, confirming that the arbitrary code was executed with the identical permissions because the person operating Notepad++.
DLL Hijacking Check
Mitigations
The first menace from this vulnerability is native code execution. An attacker who has already gained preliminary entry to a system by way of malware, phishing, or different means can use this flaw to ascertain persistence.
By hijacking a DLL in a generally used software like Notepad++, the attacker’s code will run each time the person opens the editor, guaranteeing the malware survives system reboots.
Whereas the demonstration was carried out on Notepad++ v8.8.3 put in through the official npp.8.8.3.Installer.x64.exe, the underlying difficulty is prime to how the appliance masses its parts, suggesting that any put in model may very well be weak.
Presently, there isn’t a official patch from the Notepad++ builders to deal with CVE-2025-56383. Customers are suggested to train warning and guarantee their methods are free from prior infections
System directors ought to take into account implementing file integrity monitoring on software directories to detect unauthorized modifications.
Till a repair is launched, customers ought to solely obtain Notepad++ from official sources and be cautious of any sudden conduct from the appliance.
Observe us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to function your tales.