A extreme privilege escalation vulnerability has been found in Notepad++ model 8.8.1, probably exposing thousands and thousands of customers worldwide to finish system compromise.
The flaw, designated CVE-2025-49144, permits attackers to realize SYSTEM-level privileges by way of a way generally known as binary planting, with a proof-of-concept demonstration now publicly accessible.
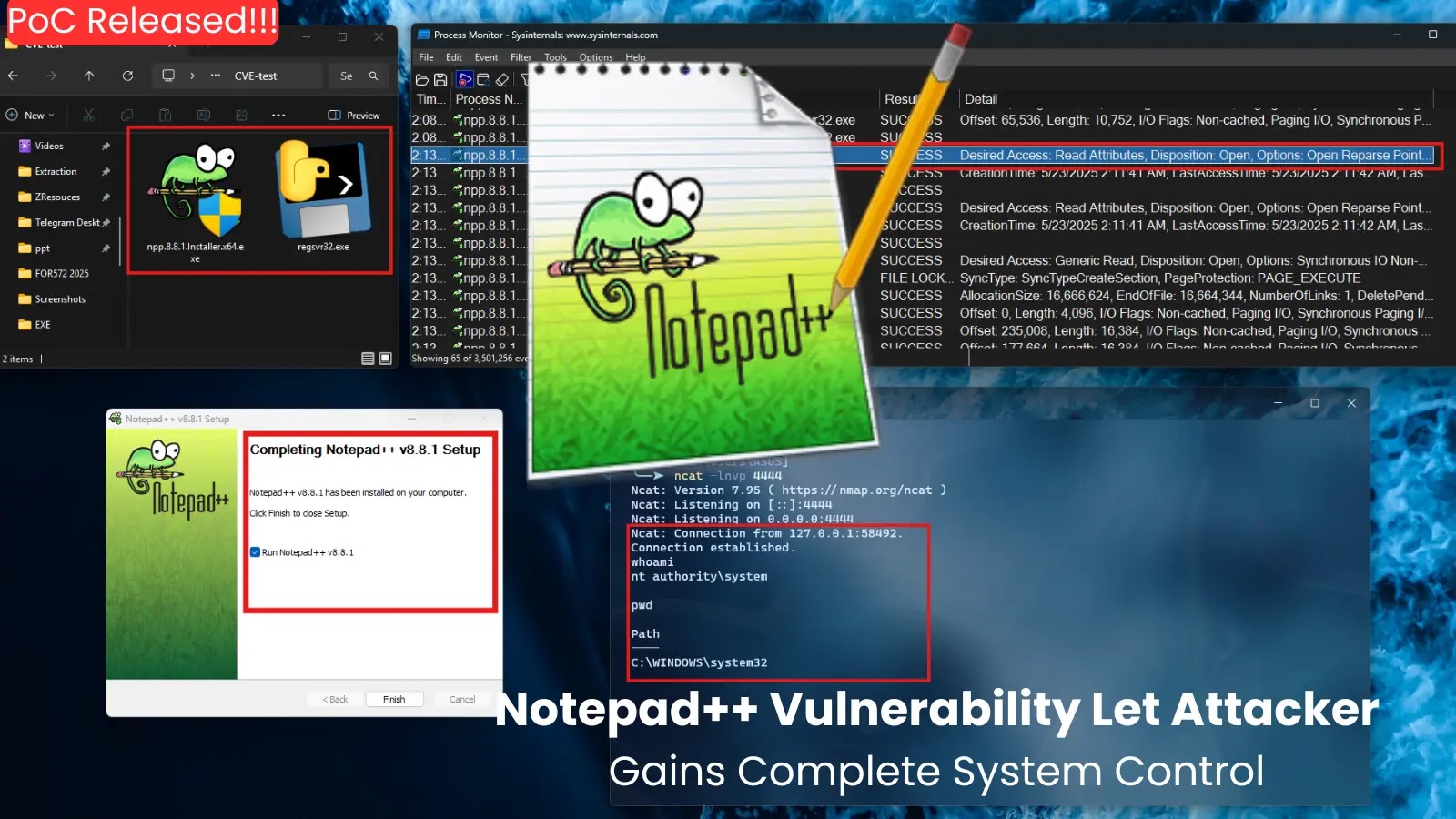
The vulnerability impacts the Notepad++ v8.8.1 installer launched on Could 5, 2025, exploiting an uncontrolled executable search path that allows native privilege escalation assaults.
Safety researchers have recognized that the installer searches for executable dependencies within the present working listing with out correct verification, making a harmful alternative for malicious code injection.
This safety flaw represents a big threat as a result of minimal person interplay required for exploitation. The assault vector leverages the usual Home windows DLL search order mechanism, permitting attackers to position malicious executables which can be robotically loaded with elevated privileges throughout the set up course of.
Assault Methodology and Proof of Idea
The exploitation course of is easy and demonstrates the harmful simplicity of binary planting assaults. Attackers can place a malicious executable, resembling a compromised regsvr32.exe, in the identical listing because the Notepad++ installer.
When unsuspecting customers run the installer, the system robotically hundreds the malicious file with SYSTEM privileges, granting attackers full management over the goal machine.
Course of Monitor logs offered within the proof-of-concept supplies clearly show the installer’s vulnerability by displaying its seek for executables within the present listing. The publicly launched demonstration contains video proof confirming profitable exploitation, elevating critical considerations about potential widespread abuse.
Notepad++ maintains a considerable person base globally, with the software program’s official web site receiving over 1.6 million month-to-month visits as of June 2025. The textual content editor holds roughly 1.33% market share within the IDEs and textual content editors class, translating to lots of of hundreds of doubtless weak installations worldwide.
The vulnerability poses significantly extreme dangers given Notepad++’s recognition amongst builders, IT professionals, and common customers throughout varied industries.
The software program’s widespread adoption in company environments considerably amplifies the potential impression of profitable assaults, probably resulting in knowledge breaches, lateral motion inside networks, and full system compromise.
This incident represents a part of a rising sample of installer vulnerabilities affecting fashionable software program functions. Earlier Notepad++ variations have confronted comparable safety challenges, together with CVE-2023-6401 and CVE-2023-47452, which additionally concerned DLL hijacking and privilege escalation vulnerabilities.
The vulnerability aligns with present cybersecurity menace developments, the place attackers more and more goal trusted software program distribution mechanisms.
Based on the 2025 World Cybersecurity Outlook, provide chain assaults and software program installer vulnerabilities symbolize crucial rising threats within the present safety panorama.
Mitigation and Response
Notepad++ builders have responded swiftly by releasing model 8.8.2 to deal with this crucial vulnerability. The patch implements safe library loading practices and absolute path verification for executable dependencies, following Microsoft’s safe loading steerage. Customers are strongly suggested to replace instantly to the patched model to get rid of the safety threat.
Safety consultants advocate implementing extra protecting measures, together with working installers from safe, remoted directories and sustaining up to date endpoint safety options able to detecting binary planting assaults. Organizations must also contemplate implementing software whitelisting and enhanced monitoring of set up processes.
The incident underscores the crucial significance of safe software program improvement practices, significantly relating to installer design and dependency loading mechanisms in trusted functions.
As cyber threats proceed to evolve, the safety group emphasizes the necessity for proactive vulnerability administration and fast response to rising threats affecting extensively used software program platforms.
Are you from SOC/DFIR Groups! – Work together with malware within the sandbox and discover associated IOCs. – Request 14-day free trial