The favored textual content editor Notepad++ has addressed a extreme safety weak spot in its replace mechanism that would enable attackers to hijack community visitors and push malicious executables to customers below the guise of professional updates.
Safety researchers lately noticed suspicious visitors patterns involving WinGUp, the built-in updater utilized by Notepad++.
In response to their findings, replace requests had been, in some instances, being redirected to malicious servers. As an alternative of retrieving real Notepad++ installers, the updater downloaded compromised binaries, making a silent malware supply channel.
An inside assessment of the studies led to the invention of a flaw in the best way WinGUp validated the integrity and authenticity of downloaded replace information.
Below sure circumstances, if an attacker may intercept or manipulate community visitors between the Notepad++ updater shopper and the official replace infrastructure, this weak spot may very well be exploited to substitute the professional installer with a rogue binary.
In such a state of affairs, the updater may very well be tricked into downloading and executing malware, all whereas showing to carry out a routine software program replace. This sort of assault aligns with traditional man-in-the-middle or traffic-hijacking methods usually seen in supply-chain and update-channel compromises.
Safety Enhancements in Newest Launch
To mitigate the difficulty and handle the issues raised by researchers, the newest Notepad++ launch introduces stricter verification through the replace course of.
Each Notepad++ and WinGUp have now been hardened to confirm the digital signature and certificates of downloaded installers earlier than continuing.
If the signature or certificates examine fails, the replace course of is straight away aborted, stopping execution of untrusted code. Notepad++ builders have acknowledged that the investigation into the precise hijacking methodology stays ongoing, and customers will likely be knowledgeable as soon as concrete proof concerning the assault vector is established.
Individually, beginning with model 8.8.7, all Notepad++ binaries, together with the installer, are digitally signed utilizing a professional certificates issued by GlobalSign.
This modification removes the necessity for customers to put in a customized Notepad++ root certificates. The undertaking now recommends that any beforehand put in Notepad++ root certificates be eliminated to scale back pointless belief anchors.
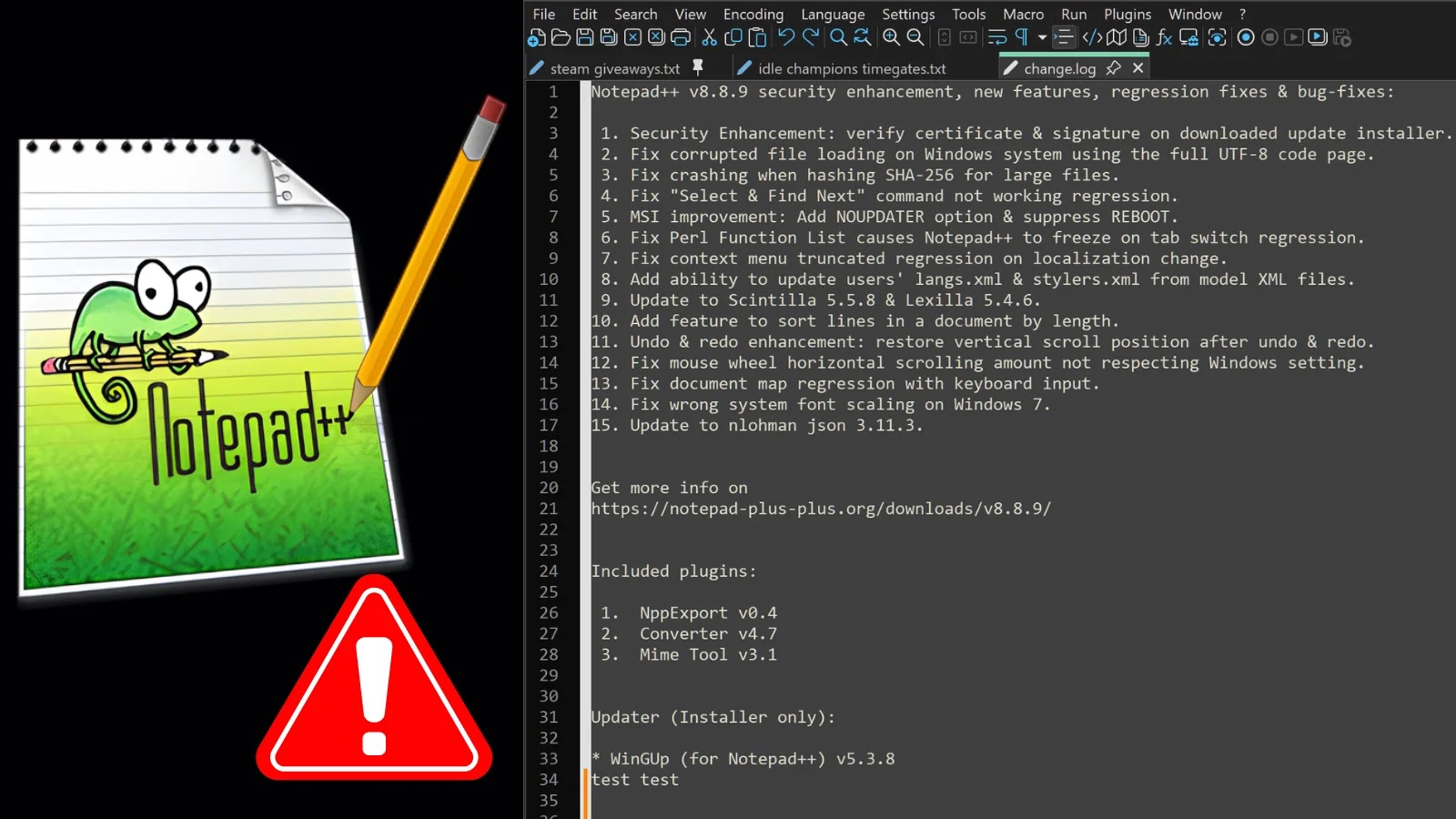
The brand new model 8.8.9 packages these safety enhancements alongside a number of bug fixes and extra enhancements. Customers are strongly suggested to improve to the newest launch and procure installers solely from the official Notepad++ web site, the place the complete changelog and obtain hyperlinks for model 8.8.9 can be found.
Observe us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to function your tales.