October 2025 marked a notable escalation in cyber threats, with phishing campaigns and ransomware variants exploiting trusted cloud companies to focus on company credentials and significant infrastructure.
Attackers more and more abused platforms like Google, Figma, and ClickUp for credential theft, whereas LockBit’s newest iteration prolonged its attain to virtualized environments.
These incidents, analyzed by cybersecurity corporations resembling ANY.RUN underscores the necessity for behavioral detection past static indicators.
Refined Phishing Leverages Reputable Platforms
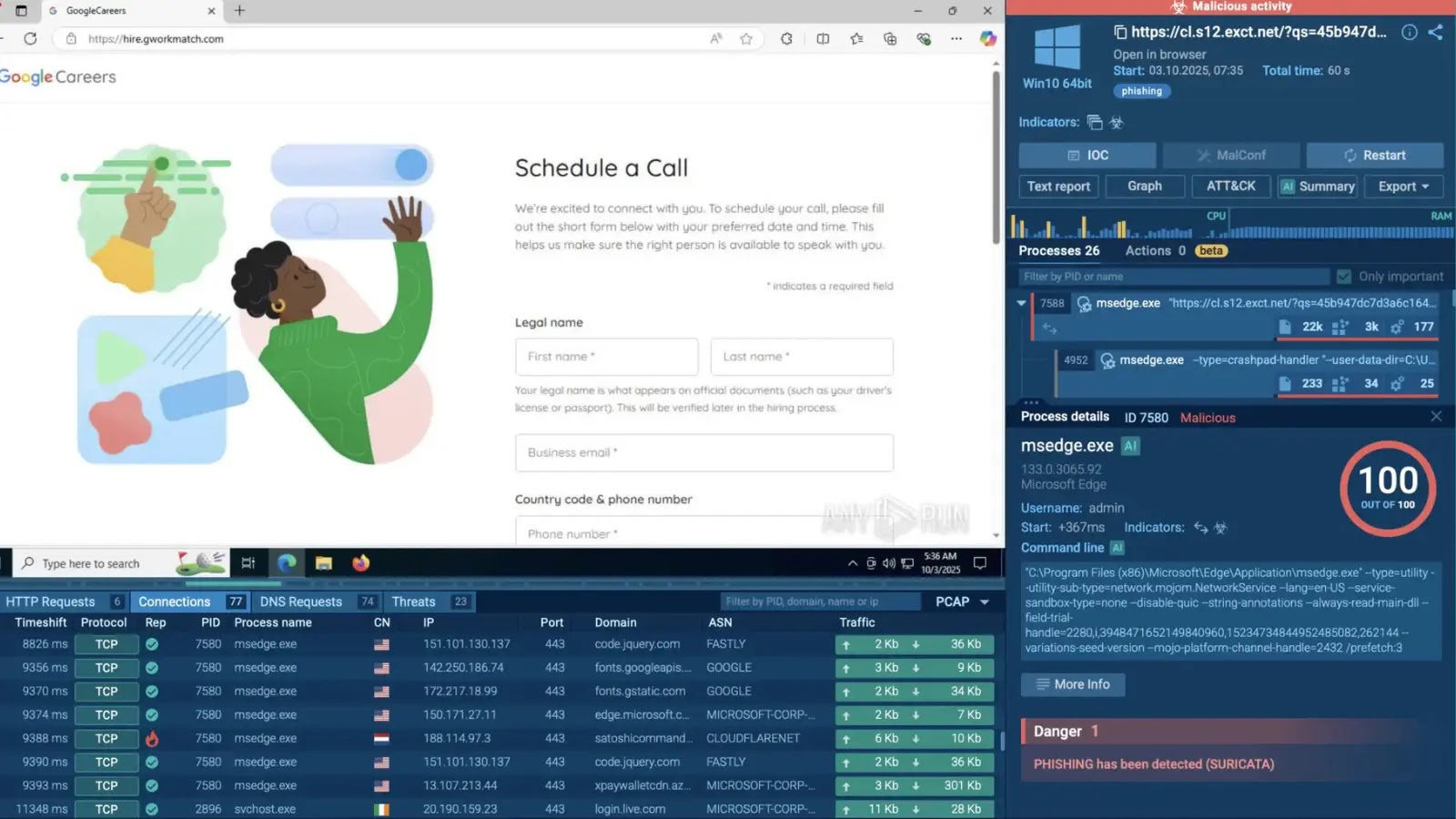
Phishing assaults in October closely relied on legit companies to evade conventional filters, beginning with a marketing campaign mimicking Google Careers job presents.
Emails lured victims with faux utility pages, routing by Salesforce redirects and Cloudflare Turnstile CAPTCHAs earlier than harvesting credentials through domains like satoshicommands.com.
This multi-step assault chain focused tech and consulting sectors, exploiting model belief to allow account takeovers and information exfiltration.
Equally, Figma’s public prototypes grew to become a vector for Microsoft-themed phishing, the place shared “doc” invitations led to faux login pages, right here is the assault evaluation.
Teams like Storm-1747 drove almost half of those assaults, utilizing Figma’s trusted area to embed interactive lures that bypassed e mail safety. Victims encountered CAPTCHAs and redirects to credential-stealing websites, usually linked to operators resembling Mamba.
ClickUp confronted abuse as a redirector, with phishing emails directing customers to doc.clickup.com, then hopping to Microsoft microdomains and Azure Blob Storage for last payload supply. This chain mimicked collaboration visitors, making it laborious for whitelists to flag, and resulted in widespread credential compromises.
A standout growth was TyKit, a reusable phishing equipment first noticed in Might 2025 however peaking in October. It hid obfuscated JavaScript in SVG information, utilizing eval capabilities and Base64 encoding to redirect customers to Microsoft 365 impersonators.
Affecting finance, authorities, and telecom throughout a number of areas, TyKit employed anti-debugging and staged C2 checks for evasion, resulting in a whole lot of account thefts through AitM strategies.
Ransomware Targets Various Working Methods
LockBit 5.0 emerged as a cross-platform risk on the ransomware entrance, celebrating the group’s sixth anniversary by increasing past Home windows to Linux and VMware ESXi.
The variant evaluation featured enhanced obfuscation, DLL reflection, and anti-analysis routines, permitting speedy encryption of digital machines and datastores.
This enabled associates to disrupt complete information facilities, with randomized extensions and log clearing complicating response efforts.
The ESXi construct was significantly alarming, concentrating on hypervisors to encrypt a number of VMs concurrently, whereas Linux and Home windows variations included region-based restrictions and repair terminations.
Assaults hit enterprises in Europe, North America, and Asia, amplifying downtime and monetary losses by shared infrastructure ways.
Safety groups should prioritize sandbox detonation for SVG and redirect evaluation, as static instruments miss these behaviors. Implementing phishing-resistant MFA, monitoring for suspicious domains like segy.zip or rent.gworkmatch.com, and integrating risk intelligence feeds can mitigate dangers.
Common backups, VPN-enforced entry, and behavioral monitoring in sandboxes like ANY.RUN’s cut back imply time to response, turning remoted indicators into proactive guidelines. As attackers refine cloud abuse, organizations ought to rehearse playbooks to counter the following surge.
Catch assaults early with on the spot IOC enrichment and interactive sandbox => Attempt Now