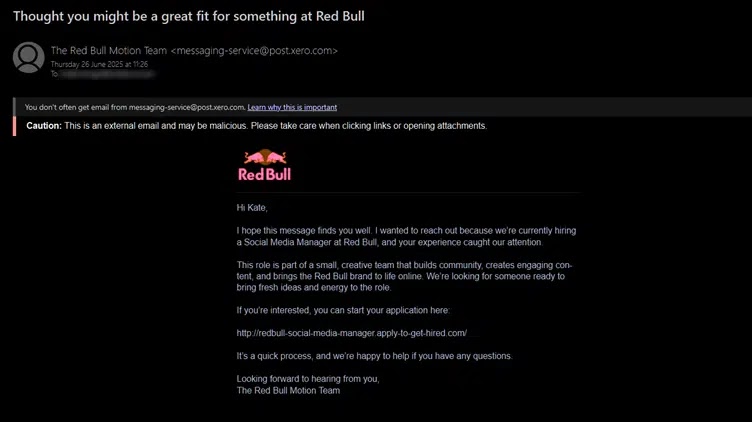
A brand new wave of phishing emails promising a “Social Media Supervisor” place at Crimson Bull has surfaced in company and private inboxes worldwide.
Disguised as customized invites, the messages originate from [email protected] and sail by way of SPF, DKIM and DMARC checks, giving conventional filters little purpose to mistrust them.
Faux e-mail (Supply – Evalian)
Their lure capitalizes on pandemic-driven remote-work appetites and the energy-drink large’s robust model recognition.
Recipients who click on the embedded hyperlink are funnelled to a reCAPTCHA gate after which to a sophisticated Glassdoor-style emptiness web page.
Glassdoor-style pretend job description (Supply – Evalian)
Evalian analysts famous that, whereas the façade appears to be like benign, the area redbull-social-media-manager.apply-to-get-hired.com is barely weeks previous and resolves to a VPS in AS-63023, a community infamous for short-lived malicious infrastructure.
After the fake job description, victims are redirected to a counterfeit Fb login the place credentials are siphoned through a POST to /login_job on 38.114.120.167.
These credentials by no means attain Fb; as a substitute they disappear right into a backend that always returns a 504 Gateway Timeout, a stalling manoeuvre that frustrates sandboxes and masks profitable exfiltration.
Evalian researchers recognized the identical TLS JARM fingerprint throughout sibling domains spoofing MrBeast and Meta, proving the marketing campaign is a rentable equipment quite than a lone one-off.
Detection evasion is the place the operation actually shines. The attackers abuse Mailgun’s high-reputation IP pool, letting them inherit Xero’s belief halo whereas hiding the true reply-to deal with [email protected].
They automate Let’s Encrypt issuance so each host presents a contemporary, legitimate certificates, erasing typical “self-signed” purple flags. Even the reCAPTCHA isn’t for the person; it throttles URL-scanning bots lengthy sufficient to drop them.
the place mail.sender_domain==”publish.xero.com”
and mail.reply_to matches “.*user0212-stripe.com”
and url.area endswith(“apply-to-get-hired.com”)
and community.jarm==”27d40d40d00040d00042d43d000000d2e61cae37a985f75ecafb81b33ca523″
The Kusto-style question above, tailored from Evalian’s SOC guidelines, triangulates sender fame, anomalous reply-to domains, malicious top-level infrastructure and the shared JARM signature, delivering high-fidelity alerts with out drowning analysts in noise.
Whereas job hunters stay the prime targets, organizations ought to block the listed IOCs, monitor outbound visitors for 38.114.120.167, and educate customers that even emails passing each authentication check should still be a wolf in well-forged clothes.
Examine dwell malware conduct, hint each step of an assault, and make sooner, smarter safety selections -> Strive ANY.RUN now