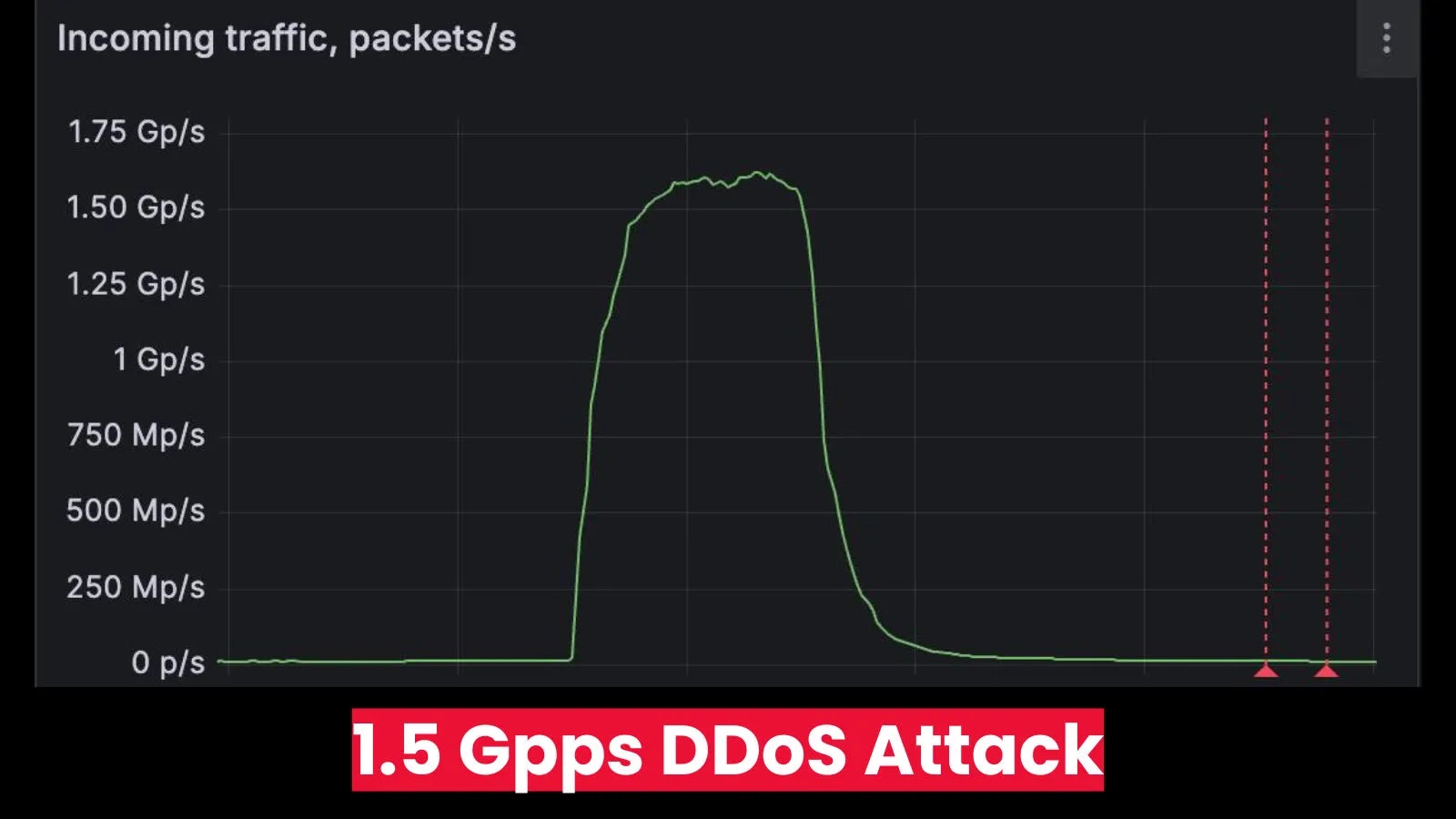
A classy cyberattack has compromised Purple Hat Consulting’s infrastructure, probably exposing delicate knowledge from over 5,000 enterprise clients worldwide.
The breach, executed by the extortion group Crimson Collective, has raised critical issues in regards to the safety of important enterprise documentation and supply code belonging to main firms, together with Vodafone, HSBC, American Specific, and Walmart.
Purple Hat, the enterprise Linux and cloud computing large, confirmed the safety incident after Crimson Collective publicly disclosed the breach on their Telegram channel.
The risk actors declare to have exfiltrated an in depth trove of knowledge containing 32 million information throughout 370,852 directories, together with extremely delicate Consultancy Engagement Experiences (CERs), proprietary supply code, and personal certificates.
LAPSUS$ Connection Emerges
Safety researcher Kevin Beaumont have recognized crashing similarities between this assault and former LAPSUS$ operations, notably by technical artifacts and behavioral patterns.
The breach reveals attribute LAPSUS$ signatures, together with particular file naming conventions, HTML remark buildings containing informal references, and the focusing on of organizations beforehand victimized by the group.
Purple Hat Listed on LAPSUS$ Hunters Portal
Most notably, investigators found that “Miku,” allegedly the Telegram deal with utilized by Crimson Collective, corresponds to Thalha Jubair, a UK teenager related to LAPSUS$ who was lately charged by the Nationwide Crime Company for the Transport for London cyberattack.
The timeline signifies the Purple Hat compromise occurred on September 13, 2025, previous to Jubair’s arrest, elevating questions on operational safety inside custody preparations.
Technical evaluation of the stolen knowledge reveals issues in regards to the publicity of important infrastructure parts.
Kevin Beaumont acknowledged that the breach contains .pfx certificates information from main monetary establishments and airways, which comprise non-public keys that ought to by no means be publicly accessible.
These certificates, as soon as compromised, can allow man-in-the-middle assaults, area spoofing, and unauthorized system entry throughout affected organizations.
The scope of compromised organizations spans a number of important sectors, together with monetary companies, healthcare, telecommunications, and transportation.
Pattern knowledge launched by the attackers contains documentation from Atos Group (managing NHS Scotland methods), Financial institution of China, Delta Airways, and ING Financial institution, highlighting the breach’s potential affect on important companies and delicate buyer knowledge.
Delta Airways, and ING Financial institution Information Launched
Purple Hat Consulting’s position as a trusted methods integrator for advanced enterprise environments amplifies the safety implications.
The stolen documentation doubtless comprises community architectures, authentication credentials, API keys, and implementation particulars that might facilitate secondary assaults in opposition to consumer organizations.
Safety specialists suggest instant remediation measures, together with certificates rotation, credential updates, and complete safety assessments.
Organizations ought to function below the idea that every one documented info will ultimately turn out to be public, as stolen knowledge sometimes circulates inside cybercriminal networks earlier than widespread disclosure.
The incident underscores the rising sophistication of provide chain assaults focusing on managed service suppliers and consulting corporations that keep privileged entry to a number of enterprise environments concurrently.
Cyber Consciousness Month Supply: Upskill With 100+ Premium Cybersecurity Programs From EHA’s Diamond Membership: Be a part of Right now