A complicated Linux kernel rootkit designed to slide previous the defenses of Elastic Safety, a number one endpoint detection and response (EDR) platform.
Launched on GitHub by researcher 0xMatheuZ, the rootkit employs superior obfuscation strategies to evade YARA-based detection and behavioral monitoring.
Whereas introduced strictly for academic functions, Singularity underscores the evolving challenges in kernel-level risk detection, doubtlessly informing each attackers and defenders within the cybersecurity arms race.
Elastic Safety, built-in with Elastic Defend, sometimes triggers over two dozen alerts throughout rootkit scans, together with file quarantines and course of terminations.
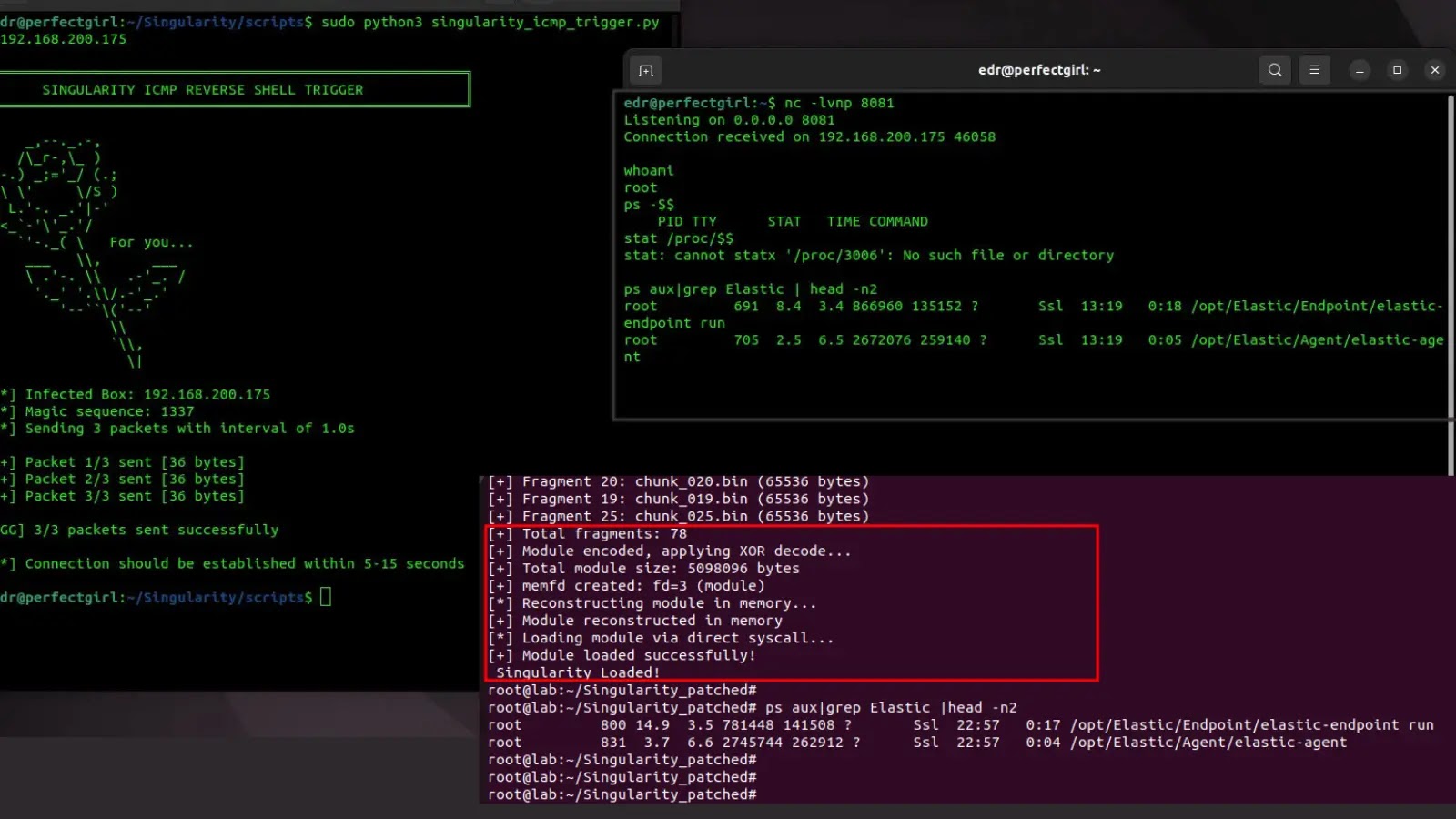
Singularity counters this by fragmenting its code, randomizing identifiers, and staging payloads in reminiscence, reaching full evasion throughout testing.
Core capabilities embody hiding processes from /proc, concealing recordsdata and directories with patterns like “singularity” or “matheuz,” masking TCP connections on port 8081, and enabling privilege escalation through customized alerts or atmosphere variables.
It additionally options an ICMP-based backdoor for reverse shells triggered by particular packet sequences, alongside anti-analysis measures that block tracing and sanitize logs.
Linux Rootkit Evades Elastic EDR Detection
On the coronary heart of Singularity’s success lies a multi-layered method to static evaluation evasion. Conventional rootkits falter on predictable strings and symbols that YARA guidelines goal, similar to “kallsyms_lookup_name” paired with “license=GPL” or hooks like “hook_getdents.”
Singularity instrument
The rootkit’s Python-based obfuscator fragments these at compile-time, splitting strings into adjoining literals that the C compiler reassembles—e.g., remodeling MODULE_LICENSE(“GPL”) into MODULE_LICENSE(“G” “P” “L”).
This ensures performance whereas rendering the binary’s strings non-contiguous for scanners, as verified by instruments like strings and objdump exhibiting no direct matches.
Image identify randomization takes it additional, changing suspicious prefixes (“hook_,” “fake_”) with innocuous, kernel-mimicking names like “sys_abjker_handler” or “kern_wopqls_helper.”
A whitelist protects important kernel APIs, and regex patterns extract capabilities for constant renaming, sorted by size to keep away from partial substitutions, MatheuZ stated.
Ftrace hooking capabilities, one other widespread giveaway, obtain related therapy, renaming “fh_install_hook” to evade guidelines detecting two or extra such patterns. These strategies collectively dismantle the 57 function-name signatures in Elastic’s generic rootkit guidelines.
Past static methods, Singularity fragments its compiled .ko file into 64KB XOR-encoded chunks utilizing a random 16-byte key, saved alongside metadata for reconstruction.
A customized loader, compiled statically, reassembles these in reminiscence through memfd_create, an nameless file descriptor that avoids disk artifacts.
It employs direct syscalls (each 64-bit and legacy 32-bit through int $0x80) to invoke finit_module, sidestepping hooked libc capabilities. This memory-only loading resists on-disk scanning, with fragments deletable post-execution.
Behavioral detection proves trickier, particularly for the ICMP-triggered reverse shell. Elastic flags patterns like setsid with /dev/tcp/ in command strains or shell executions from kernel employees.
Singularity counters by writing a staged bash script to /singularity, hiding the spawning kworker PID instantly, then executing a clear /bin/bash /singularity.
The script opens a TCP descriptor, spawns sh within the background, and makes use of kill -59 on exact PIDs for focused hiding and escalation, bypassing command-line scrutiny with out affecting official processes.
Evades safety Detection
Bonus evasions embody compiling loaders in /tmp as a substitute of monitored /dev/shm and automating the obfuscation pipeline for reproducibility. In assessments, Singularity loaded undetected, hid processes, and established root shells, proving its mettle towards present Elastic guidelines.
This work highlights the fragility of signature-based defenses towards adaptive threats. As EDRs evolve, such analysis pushes for holistic detection mixing machine studying and anomaly evaluation. For defenders, it alerts the necessity for deeper kernel integrity checks; for researchers, it’s a blueprint for resilience.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.