Scattered Spider’s phishing area patterns present actionable insights to proactively counter threats from the infamous cyber group accountable for latest airline assaults.
Scattered Spider, a complicated cyber risk group recognized for aggressive social engineering and focused phishing, is broadening its scope, notably focusing on aviation alongside enterprise environments.
Verify Level Analysis has uncovered particular phishing area indicators, serving to enterprises and aviation firms proactively defend in opposition to this rising risk.
Latest Aviation Assaults Linked to Scattered Spider
In a major escalation, latest media studies and intelligence advisories have linked Scattered Spider to cyberattacks on main airways, notably the July 2025 information breach affecting six million Qantas clients.
Cybersecurity analysts famous ways corresponding to MFA fatigue and voice phishing (vishing), intently matching Scattered Spider’s recognized strategies.
Comparable incidents involving Hawaiian Airways and WestJet have additional highlighted the urgency of addressing vulnerabilities in aviation-related third-party suppliers.
The FBI has issued warnings concerning the group’s increasing deal with the aviation sector, with a number of carriers reporting suspicious exercise.
Key Concentrating on Indicators and Phishing Domains
Verify Level Analysis has recognized a constant sample within the phishing infrastructure registered by Scattered Spider.
These domains intently mimic authentic company login portals and are designed to deceive workers into revealing their credentials.
Typical naming conventions embody:
victimname-sso.com
victimname-servicedesk.com
victimname-okta.com
Throughout a focused investigation, Verify Level researchers recognized roughly 500 domains that comply with Scattered Spider’s recognized naming conventions, indicating potential phishing infrastructure both in use or ready for future assaults.
Examples of noticed domains embody chipotle-sso[.]com, gemini-servicedesk[.]com, and hubspot-okta[.]com.
This cross-sector focusing on underscores the group’s opportunistic strategy, adapting to high-value vulnerabilities moderately than specializing in a selected vertical.
Publicly accessible intelligence outlines Scattered Spider as energetic since a minimum of 2022, composed primarily of younger people (ages 19–22) from the US and UK.
The group is financially pushed, focusing on ransomware, credential theft, and cloud infrastructure whereas using superior social engineering methods.
Full Scattered Spider Assault Methodology: 5-phase cyber assault course of with detailed instruments and methods
Refined Assault Arsenal
Scattered Spider employs a broad vary of subtle assault strategies to infiltrate targets and keep long-term entry.
Their social engineering strategies embody focused phishing, SIM swapping, multi-factor authentication (MFA) fatigue assaults, and telephone impersonation ways.
The group makes use of quite a few distant entry instruments, together with TeamViewer, AnyDesk, Splashtop, ScreenConnect, and Tailscale.
For credential theft, they make use of instruments like Mimikatz and ADExplorer, whereas their malware arsenal consists of WarZone RAT, Raccoon Stealer, and Vidar Stealer.
Most notably, Scattered Spider has been linked to BlackCat/ALPHV ransomware deployments, working underneath a Ransomware-as-a-Service mannequin.
Verify Level recommends tailor-made defensive methods for each enterprises and aviation organizations.
For enterprises, this consists of steady area monitoring, worker coaching targeted on MFA abuse and vishing, adaptive authentication options, and strong endpoint safety.
Aviation sector organizations ought to prioritize vendor danger administration, sturdy id verification for password resets, and sector-specific incident response playbooks.
The analysis underscores that no sector is immune to classy social engineering campaigns, making proactive protection measures important for all organizations.
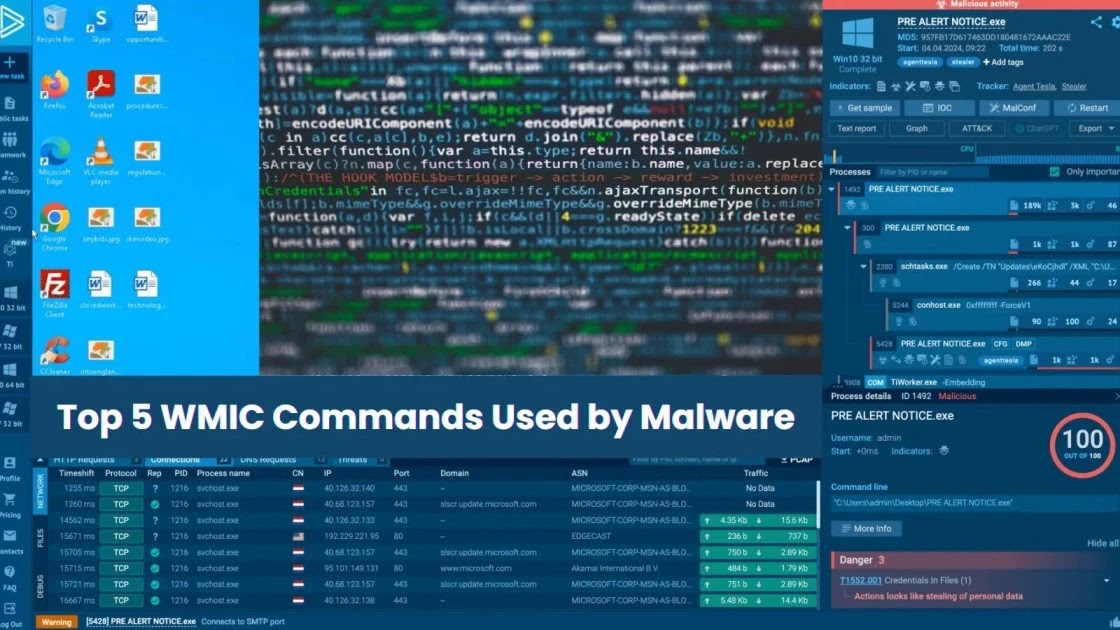
Examine reside malware habits, hint each step of an assault, and make sooner, smarter safety selections -> Strive ANY.RUN now