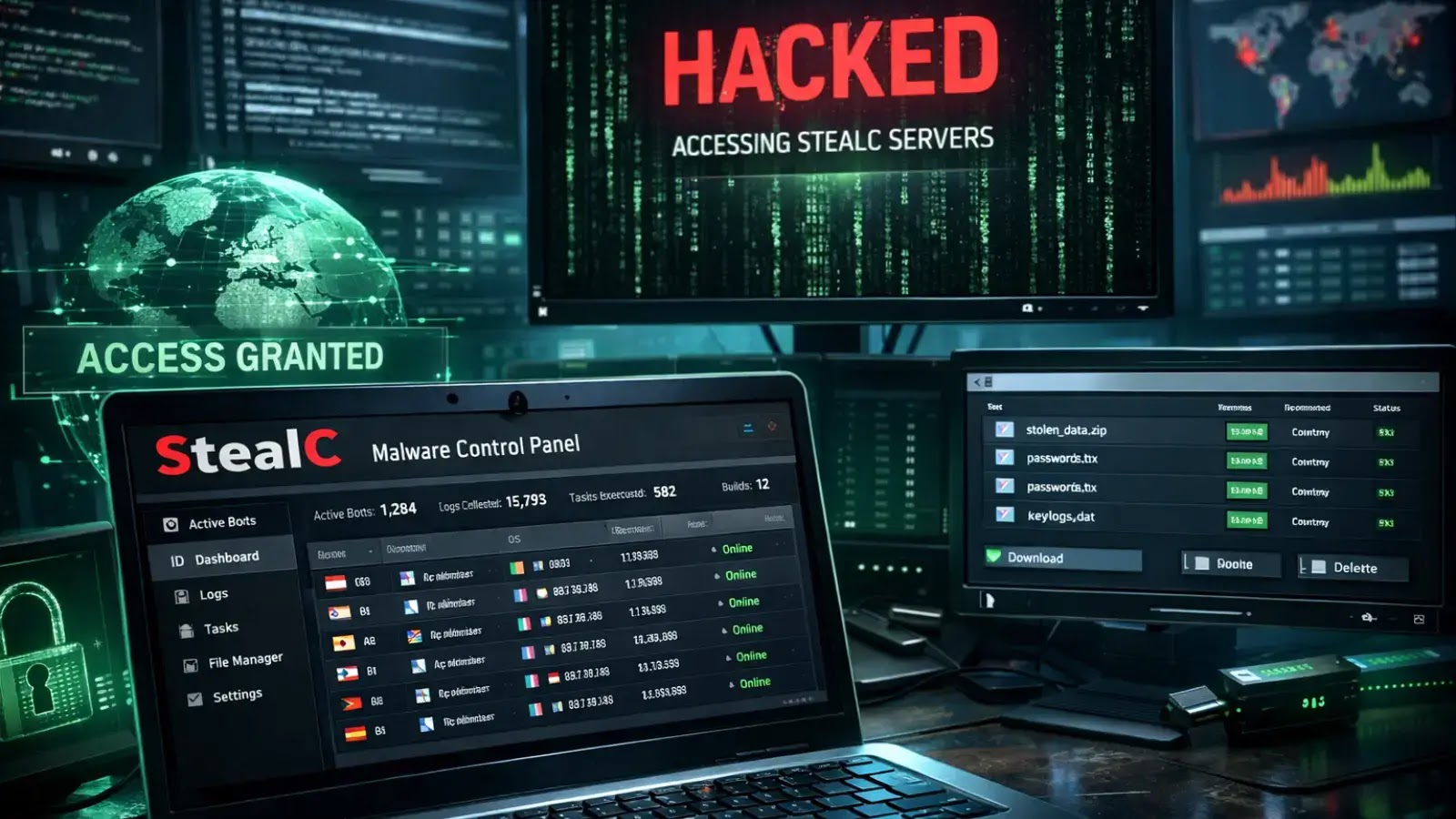
Safety researchers efficiently exploited vulnerabilities within the StealC malware infrastructure, having access to operator management panels and exposing a menace actor’s identification by means of their very own stolen session cookies.
The breach highlights essential safety failures in legal operations constructed round credential theft.
XSS Vulnerability Exposes StealC Operators
StealC, an information-stealing malware working below a Malware-as-a-Service mannequin since early 2023, confronted a big setback when researchers found a cross-site scripting (XSS) vulnerability in its net panel following a code leak in spring 2025.
StealC construct web page with instance construct referred to as “YouTubeNew”
By exploiting this flaw, CyberArk Labs collected system fingerprints, monitored energetic periods, and captured authentication cookies from the infrastructure designed to steal them.
The irony proved vital: operators specializing in cookie theft didn’t implement primary security measures, such because the httpOnly flag, that may have prevented cookie hijacking through XSS assaults.
YouTubeTA’s StealC net panel
Via panel entry, researchers tracked a single operator designated “YouTubeTA” (YouTube Menace Actor) who maintained over 5,000 an infection logs containing 390,000 stolen passwords and 30 million cookies.
Screenshots captured by the malware confirmed victims trying to find cracked variations of Adobe Photoshop and After Results on YouTube, suggesting that YouTubeTA compromised authentic YouTube channels with established subscriber bases to distribute StealC.
Seemingly clickfix web page used to put in StealC
The operator’s panel configuration included particular markers for studio.youtube.com credentials, indicating a technique to hijack content material creator accounts and increase malware distribution networks.
Panel fingerprinting recognized YouTubeTA as a single operator utilizing an Apple M3 processor, with constant {hardware} signatures throughout all periods, as reported by CyberArk Labs .
Language preferences confirmed assist for English and Russian, whereas timezone information indicated GMT+0300 (Japanese European Summer season Time).
A essential operational safety failure occurred when the operator briefly linked with out VPN safety, revealing an IP handle related to Ukrainian ISP TRK Cable TV.
This breach demonstrates how MaaS provide chain vulnerabilities expose each infrastructure weaknesses and operator identities to safety researchers.
Observe us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to characteristic your tales.