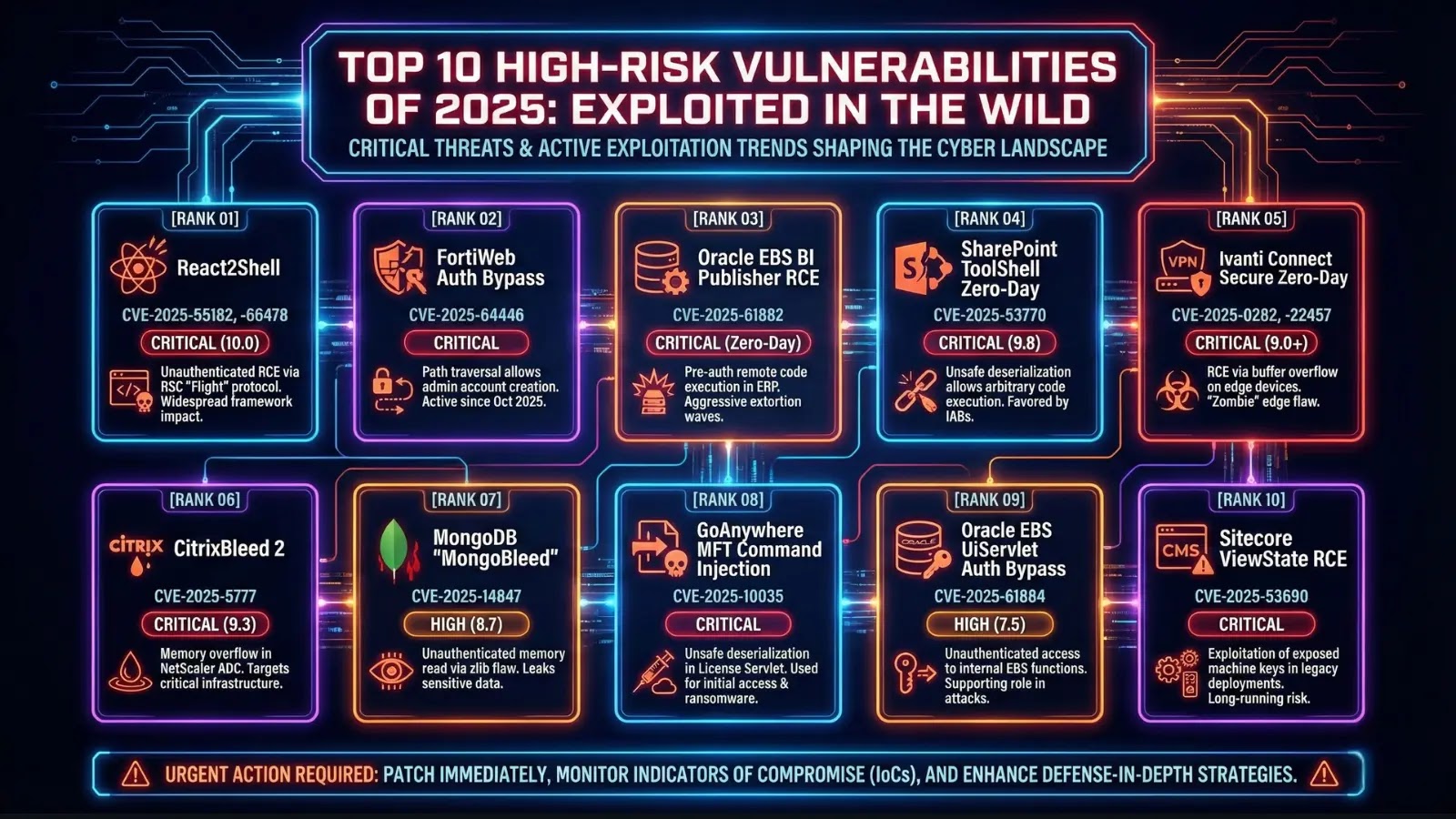
A classy new malware pressure focusing on Linux environments has emerged, demonstrating superior evasion capabilities that problem conventional endpoint detection and response methods.
RingReaper, recognized as a post-exploitation agent, leverages the Linux kernel’s trendy asynchronous I/O interface to conduct covert operations whereas sustaining minimal visibility to safety monitoring instruments.
The malware’s major innovation lies in its exploitation of io_uring, a comparatively current addition to the Linux kernel that permits high-performance asynchronous I/O operations.
By using this interface as an alternative of typical system calls, RingReaper successfully bypasses hook-based detection mechanisms that the majority EDR options depend upon for risk identification and mitigation.
PICUS Safety analysts have recognized RingReaper as a very regarding risk attributable to its systematic method to reconnaissance and knowledge assortment.
The malware demonstrates capabilities spanning a number of assault vectors, together with course of discovery, community enumeration, person identification, and privilege escalation, all whereas sustaining stealth by means of its novel evasion methods.
The affect of RingReaper extends past typical malware considerations, as its success represents a paradigm shift in how risk actors can evade trendy safety infrastructure.
Conventional monitoring options that depend upon system name interception discover themselves blind to actions performed by means of io_uring primitives, creating important gaps in organizational safety postures.
Superior Evasion By io_uring Implementation
RingReaper’s most refined function facilities on its implementation of io_uring primitives to exchange commonplace system calls usually monitored by safety instruments.
As an alternative of invoking typical features reminiscent of learn, write, recv, ship, or join, the malware employs asynchronous operations by means of io_uring_prep_* features.
This method proves notably efficient throughout reconnaissance phases. When performing course of discovery, RingReaper executes payloads like “$WORKDIR”/cmdMe and “$WORKDIR”/executePs to enumerate working processes and system info.
These operations question the /proc filesystem asynchronously, retrieving course of IDs, names, and possession particulars with out triggering commonplace course of monitoring alerts.
The malware’s community discovery capabilities exhibit comparable sophistication by means of the “$WORKDIR”/netstatConnections payload, which leverages io_uring to question kernel community tables and socket info.
This successfully replicates netstat performance whereas avoiding synchronous system calls, permitting complete community connection knowledge assortment with decreased detection likelihood.
Maybe most regarding is RingReaper’s self-preservation mechanism applied by means of the “$WORKDIR”/selfDestruct payload, which makes use of io_uring for asynchronous file deletion.
This allows the malware to take away its personal executables whereas avoiding commonplace file operation monitoring, making certain thorough artifact elimination and complicating forensic evaluation efforts considerably.
Enhance your SOC and assist your crew defend what you are promoting with free top-notch risk intelligence: Request TI Lookup Premium Trial.