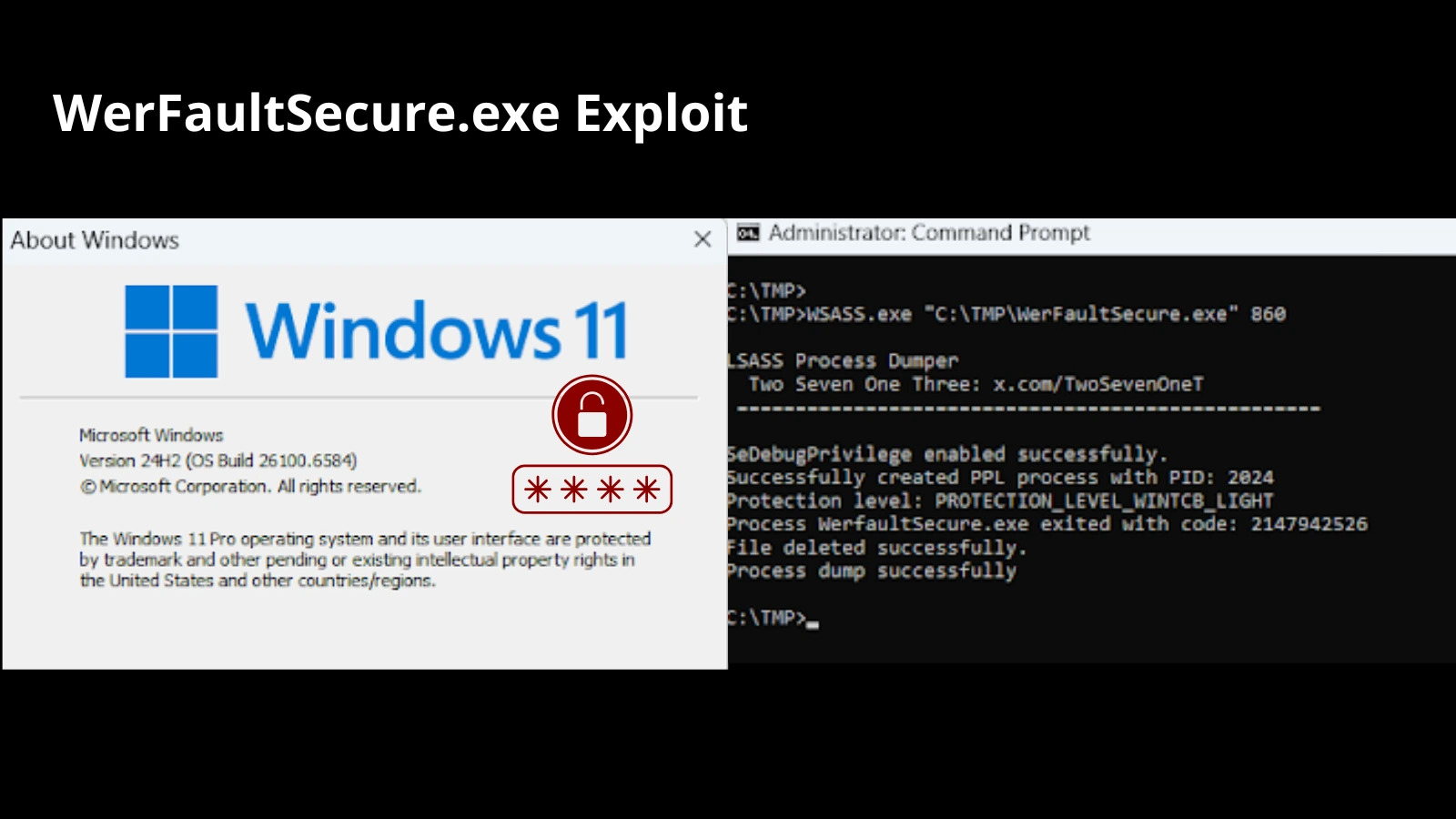
In early 2025, cybersecurity researchers noticed an unprecedented collaboration between two Russian APT teams concentrating on Ukrainian organizations.
Traditionally, Gamaredon has targeted on broad spear-phishing campaigns towards authorities and demanding infrastructure, whereas Turla has specialised in high-value cyberespionage utilizing subtle implants.
Their joint operations mark a big escalation: Gamaredon features preliminary entry utilizing its established toolkit, then Turla deploys its superior Kazuar backdoor to take care of stealthy long-term presence.
This alliance leverages Gamaredon’s noisy compromise strategies to ship Turla’s modular espionage implant on rigorously chosen machines, suggesting a strategic alignment throughout the FSB’s inside cyber-intelligence equipment.
Rising primarily by means of malicious LNK information and spear-phishing emails delivered through detachable media, the assault chain begins with Gamaredon’s PteroGraphin downloader.
As soon as on a sufferer system, PteroGraphin retrieves further payloads by means of encrypted Telegra.ph channels. On February 27, 2025, PteroGraphin, residing at %APPDATApercent86.ps1, fetched and decrypted a second-stage downloader, PteroOdd, utilizing a hardcoded 3DES key.
PteroGraphin token partially redacted (Supply – Welivesecurity)
PteroOdd then retrieved and executed Kazuar v3 in reminiscence by side-loading into legit processes, successfully evading typical defenses.
Welivesecurity analysts famous this dual-stage supply mechanism was crucial in restarting and deploying Kazuar implants after preliminary crashes or set up of endpoint safety merchandise.
The seamless handoff between Gamaredon instruments and Turla’s backdoor illustrates an evolution in Russian APT techniques, the place inter-group cooperation amplifies impression whereas limiting detection.
Regardless of Gamaredon’s tons of of noisy intrusions, Turla selectively installs Kazuar solely on machines deemed extremely invaluable.
This precision concentrating on reduces the implant’s publicity and minimizes forensic footprints.
Beautified JSON reply (Supply – Welivesecurity)
As soon as deployed, Kazuar v3 establishes encrypted command-and-control channels over WebSockets and Trade Internet Providers, supporting three distinct roles—KERNEL, BRIDGE, and WORKER—to modularize performance and preserve resilience towards takedown makes an attempt.
An infection Mechanism Deep Dive
The an infection mechanism of Kazuar facilities on subtle PowerShell loaders and side-loading methods that exploit legit Home windows processes. After PteroOdd retrieves the base64-encoded PowerShell payload, it executes a command much like:-
Begin-Course of -FilePath “C:Program FilesSomeAppvncutil64[.]exe” -ArgumentList “- EncodedCommand”,”[base64-encoded Kazuar loader]”
This strategy masks the backdoor as a part of a trusted software, stopping signature-based detection.
The loader writes a DLL named LaunchGFExperienceLOC[.]dll alongside LaunchGFExperience[.]exe, initiating Kazuar’s launch by means of DLL side-loading.
In reminiscence, two distinct KERNEL payloads seem, labeled AGN-RR-01 and AGN-XX-01, indicating redundant execution paths that improve implant robustness.
As soon as lively, Kazuar collects system metadata—laptop identify, quantity serial quantity, operating processes—and exfiltrates these through a Cloudflare Employees subdomain below Turla’s management.
Subsequent HTTP POSTs affirm profitable implant launch and supply bridge nodes with adaptive payloads. By leveraging dynamic loader scripts and dual-payload execution chains, Turla ensures steady entry even when one supply path fails or is detected.
This an infection mechanism underscores the sophistication of contemporary APT alliances: combining Gamaredon’s large attain with Turla’s stealth backdoor yields a flexible espionage functionality able to infiltrating high-value targets whereas minimizing detection threat.
Discover this Story Fascinating! Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates.