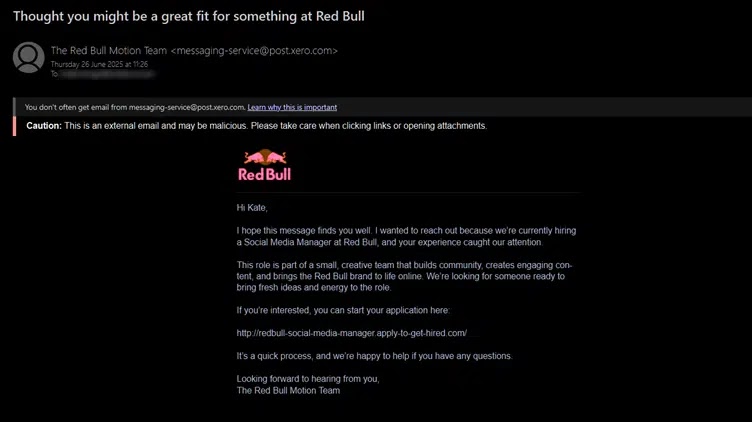
Chinese language menace actors working underneath the title Silver Fox are focusing on Indian organizations via subtle phishing campaigns that impersonate reliable revenue tax paperwork.
The assault marketing campaign makes use of authentic-looking Earnings Tax Division emails to trick customers into downloading a malicious executable disguised as a tax-related file.
As soon as clicked, victims are redirected to a command-and-control server, which initiates a posh an infection chain designed to bypass safety defenses and set up persistent entry to compromised methods.
The assault begins with a misleading electronic mail containing a PDF attachment bearing an Indian firm title. When opened, the PDF results in a malicious web site that downloads a file named “tax_affairs.exe”.
This preliminary payload serves as a loader for a number of phases of malware, every designed to cover its true function whereas sustaining deep entry to sufferer methods.
The menace demonstrates how attackers leverage socially engineered paperwork mixed with trusted file codecs to beat conventional safety controls.
Kill chain (Supply – CloudSEK)
CloudSEK analysts recognized the malware within the second paragraph of the investigation, revealing that the marketing campaign had beforehand been misattributed to different menace teams.
The invention highlights how correct menace attribution prevents organizations from deploying incorrect defensive measures towards the precise adversary.
Understanding the true supply of assaults permits safety groups to anticipate future techniques and implement focused countermeasures particular to Silver Fox’s operational patterns.
DLL hijacking
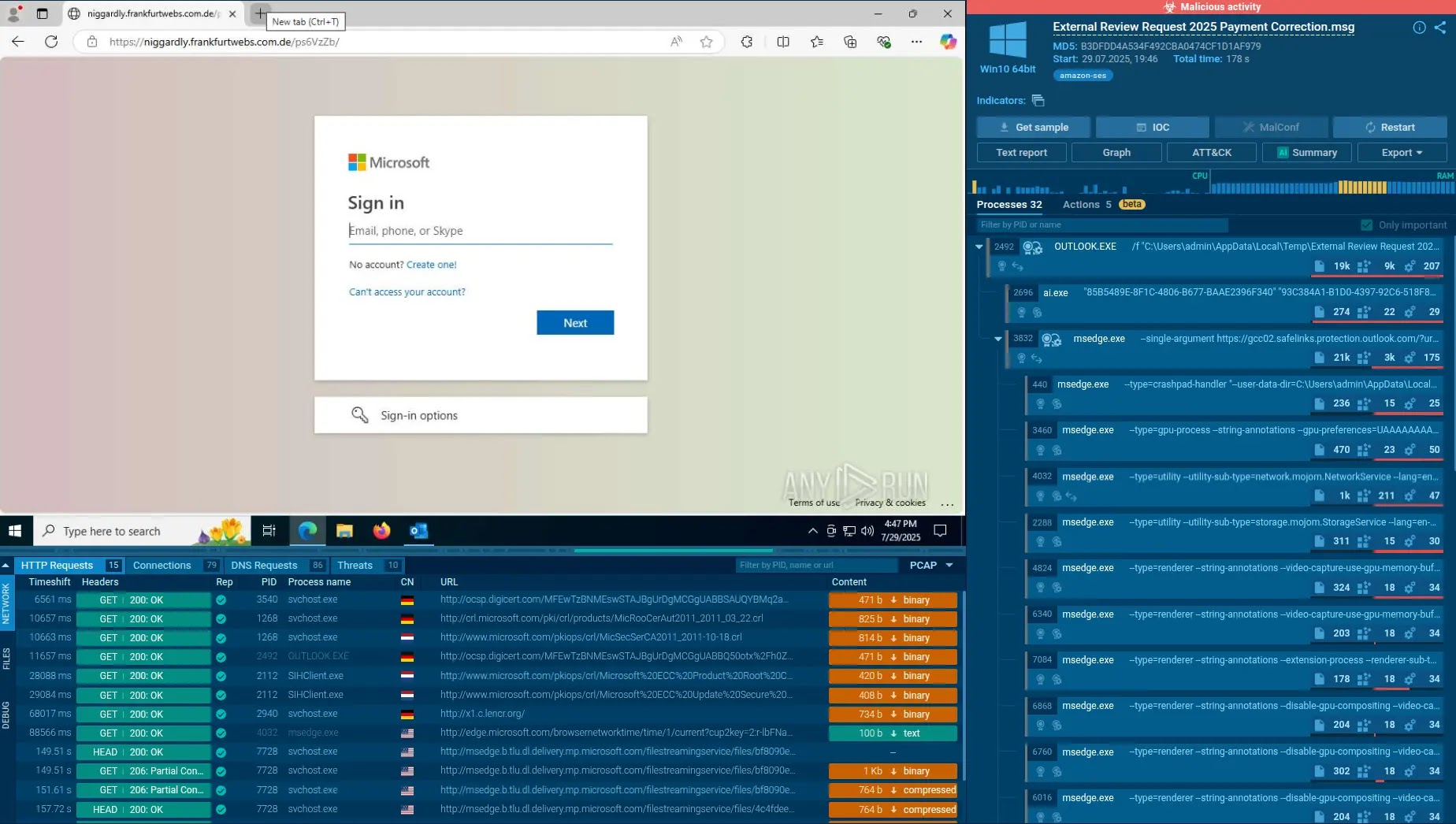
The an infection mechanism depends on a method referred to as DLL hijacking to activate the primary payload. The primary stage drops a reliable executable referred to as Thunder.exe, developed by the Chinese language software program firm Xunlei.
This signed binary is weaponized by inserting a malicious DLL file named libexpat.dll in the identical non permanent listing. When Thunder.exe runs, Home windows hundreds the faux DLL as an alternative of the real one as a result of default DLL search order, executing the attacker’s code whereas showing fully reliable.
PDF Decoy (Supply – CloudSEK)
The malicious DLL implements intensive anti-analysis capabilities earlier than participating in precise an infection actions.
It scans operating processes to detect safety analysis instruments and sandboxes, then checks system assets to make sure the machine meets minimal necessities for an infection. If evaluation instruments are discovered, the malware terminates itself to keep away from detection.
As soon as the system passes these checks, the DLL disables Home windows Replace providers and hundreds an encrypted file referred to as field.ini from the non permanent listing.
Course of Injection (Supply – CloudSEK)
This encrypted payload is decrypted utilizing hardcoded cryptographic keys and executed as uncooked machine code instantly in system reminiscence, leaving minimal traces on the exhausting drive.
The ultimate payload is Valley RAT, a distant entry software that establishes a everlasting command and management infrastructure on contaminated methods.
Valley RAT makes use of a classy three-tier failover system to take care of contact with attacker servers, robotically switching between main, secondary, and tertiary command facilities if connections fail.
The malware shops its configuration within the Home windows registry as binary information, permitting attackers to replace command and management addresses with out reinstalling the malware.
It helps a number of communication protocols, together with HTTP, HTTPS, and uncooked TCP sockets, making it troublesome to dam utilizing easy community filtering.
As soon as put in, Valley RAT can execute attacker instructions, seize keyboard enter, harvest credentials, switch information, and deploy further malicious modules on demand.
The modular structure permits operators to customise every an infection with specialised capabilities tailor-made to the goal’s worth and function throughout the compromised group, making this a very harmful menace to Indian enterprises.
Comply with us on Google Information, LinkedIn, and X to Get Extra On the spot Updates, Set CSN as a Most well-liked Supply in Google.