Cybersecurity researchers have uncovered a classy malware distribution marketing campaign using GitHub repositories disguised as legit software program initiatives.
The SmartLoader malware has been strategically deployed throughout a number of repositories, capitalizing on customers’ belief within the standard code-sharing platform to infiltrate methods worldwide.
The malicious marketing campaign targets customers looking for sport cheats, software program cracks, and automation instruments by positioning fraudulent repositories on the high of search outcomes.
SmartLoader distribution website being displayed on the high of Google search outcomes (Supply – ASEC)
These repositories seem genuine, full with professionally crafted README information, venture documentation, and reasonable file buildings that mirror legit open-source initiatives.
The menace actors behind this operation have demonstrated outstanding consideration to element, making their malicious repositories just about indistinguishable from real software program initiatives.
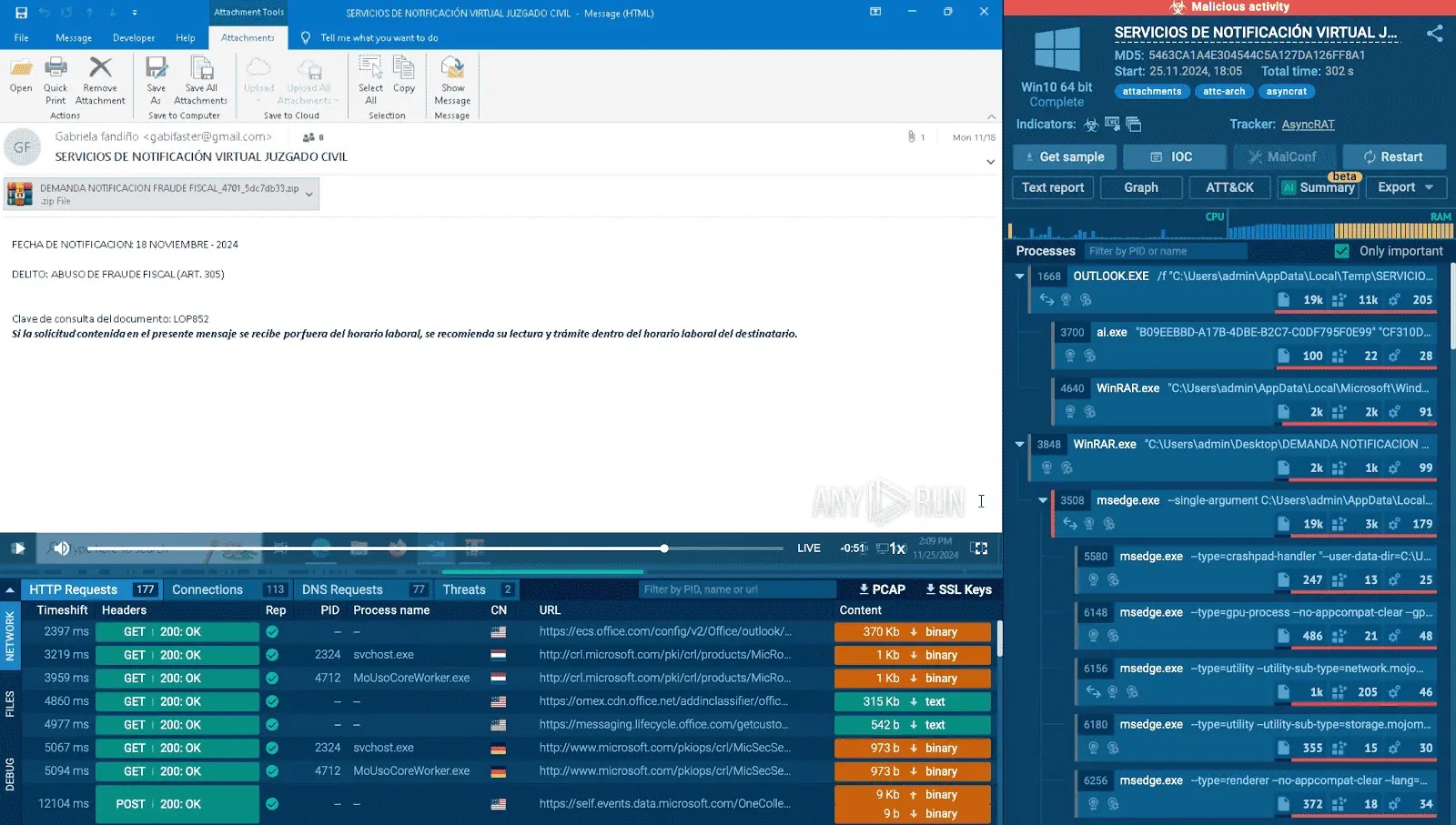
Every compromised repository comprises fastidiously constructed compressed information internet hosting the SmartLoader payload. When customers obtain and execute these information, they unknowingly provoke a multi-stage an infection course of that establishes persistent entry to their methods.
ASEC analysts recognized this widespread distribution methodology as significantly regarding as a consequence of its exploitation of developer and gaming communities’ belief in GitHub as a dependable supply for software program instruments.
Technical An infection Mechanism and Payload Deployment
The SmartLoader an infection course of begins when customers execute the Launcher.cmd file, which serves because the preliminary assault vector.
This malicious batch file masses an obfuscated Lua script by way of luajit.exe, a legit Lua interpreter that has been weaponized for malicious functions.
Recordsdata contained in the compressed file (Supply – ASEC)
The malware bundle consists of 4 core parts: java.exe (the legit Lua loader), Launcher.cmd (malicious batch file), lua51.dll (Luajit runtime interpreter), and module.class (obfuscated Lua script).
As soon as activated, SmartLoader establishes persistence by copying important information to the %AppDatapercentODE3 listing and registering itself within the Home windows Process Scheduler as “SecurityHealthService_ODE3”.
The malware instantly captures screenshots and system data, transmitting this information to command-and-control servers by way of Base64-encoded communications.
The malware’s most harmful functionality lies in its position as a loader for added payloads.
Evaluation revealed that SmartLoader downloads and executes secondary malware together with Rhadamanthys infostealer, which targets delicate data from e-mail shoppers, FTP functions, and on-line banking providers.
The malware performs course of injection into legit Home windows processes corresponding to openwith.exe, dialer.exe, and dllhost.exe to evade detection.
Communication with C2 servers happens by way of encrypted channels, with the malware receiving JSON-formatted instructions containing configuration parameters and job lists.
This infrastructure permits menace actors to dynamically replace malware conduct and deploy further payloads primarily based on the contaminated system’s traits.
This marketing campaign highlights the crucial significance of verifying software program sources and analyzing repository credibility, commit historical past, and writer authenticity earlier than downloading any GitHub-hosted functions, significantly these associated to sport modifications or software program cracks.
Increase your SOC and assist your crew shield your enterprise with free top-notch menace intelligence: Request TI Lookup Premium Trial.