A classy malware loader often called CastleLoader has emerged as a vital risk to US authorities companies and demanding infrastructure organizations.
First recognized in early 2025, this stealthy malware has been used because the preliminary entry level in coordinated assaults concentrating on a number of sectors together with federal companies, IT companies, logistics firms, and important infrastructure suppliers throughout North America and Europe.
Safety researchers have documented {that a} single CastleLoader marketing campaign impacted roughly 460 distinct organizations, with specific give attention to compromising authorities programs in the US.
CastleLoader operates as a multi-stage loader that delivers secondary payloads immediately into system reminiscence, making it exceptionally troublesome for conventional safety defenses to detect.
The malware’s major operate is to determine an preliminary foothold on compromised programs, after which it deploys extra harmful instruments together with info stealers and distant entry trojans that give attackers full management over contaminated networks.
The loader’s common nature and excessive an infection price have made it a most popular instrument amongst risk actors who search to compromise high-value targets whereas evading detection programs.
View evaluation
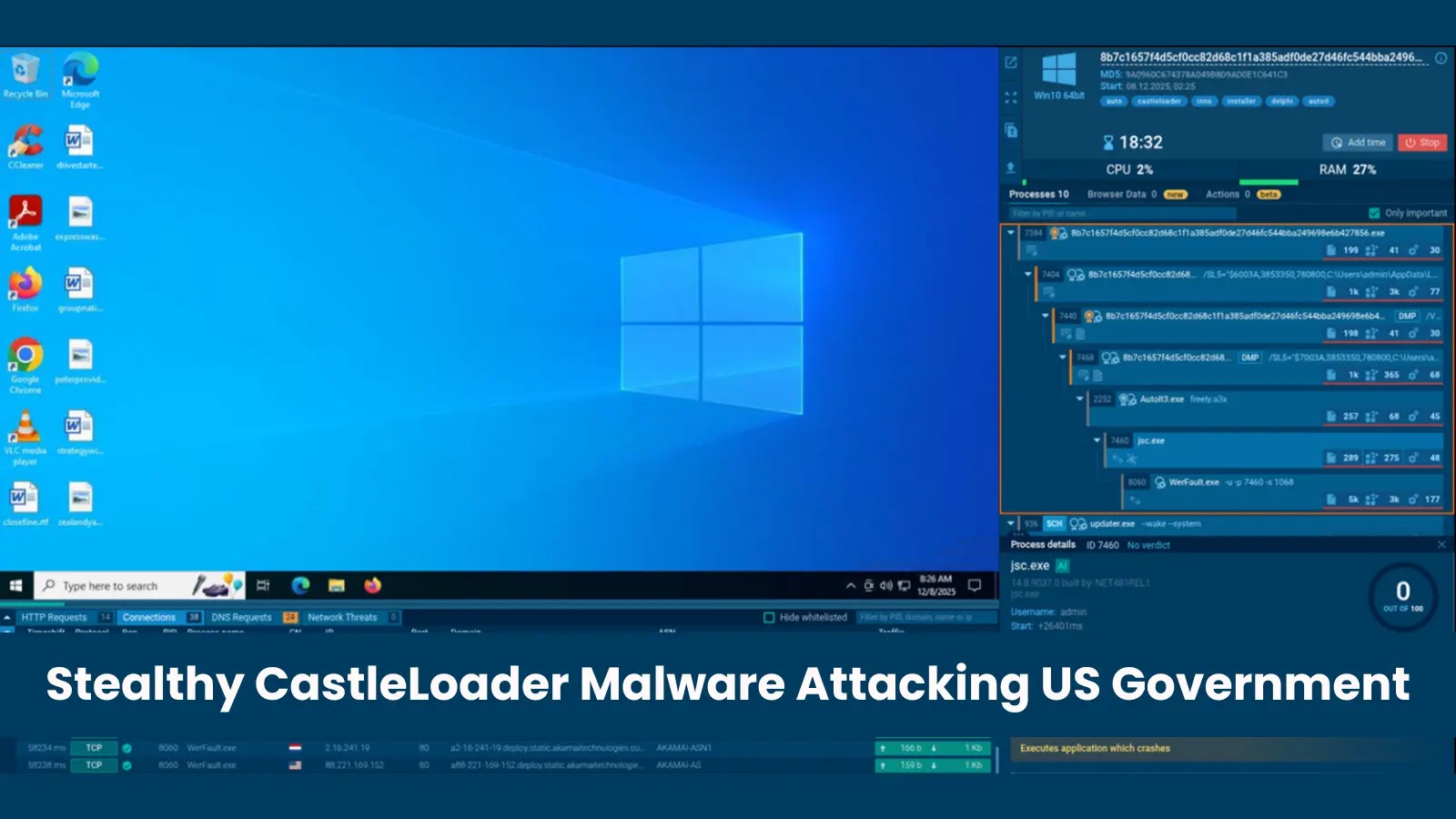
The launch of CastleLoader pattern exhibiting suspicious processes and community actions detected (Supply – Any.Run)
The assault vector for CastleLoader sometimes includes social engineering strategies often called ClickFix, the place victims are deceived by faux software program replace prompts or system verification messages.
When customers adjust to these faux requests, they unknowingly execute malicious instructions that ship CastleLoader because the second stage of the assault chain.
This misleading method has confirmed remarkably efficient at bypassing consumer consciousness coaching and preliminary safety controls.
Any.Run analysts and researchers famous the malware’s subtle structure throughout their detailed investigation, figuring out a fastidiously orchestrated execution chain designed particularly to evade fashionable safety instruments.
The evaluation revealed that CastleLoader doesn’t function as a easy executable however as a substitute depends on a posh layered method that makes each stage seem comparatively benign on first inspection.
CastleLoader installer (Supply – Any.Run)
This technique permits the malware to distribute its malicious exercise throughout a number of legitimate-looking processes, successfully hiding in plain sight.
Stop assaults by tapping into 99% distinctive IOCs Combine TI Feeds for higher proactive protection Attain out for particulars
An infection Chain and Evasion Mechanisms
CastleLoader’s an infection mechanism represents a masterclass in stealth and obfuscation.
The malware arrives packaged as an Inno Setup installer file containing a number of elements, together with AutoIt3.exe and a compiled AutoIt script saved as freely.a3x.
Information extracted from Inno Setup installer (Supply – Any.Run)
When executed, the AutoIt script initiates the vital subsequent part: launching the jsc.exe course of (a reliable JScript.NET compiler) with the CREATE_SUSPENDED flag, which pauses the method instantly after creation.
Slightly than executing on this suspended state, the malware implements a refined course of hollowing method that injects a totally useful PE executable immediately into the jsc.exe reminiscence area.
The method follows this sequence: first, reminiscence is allotted throughout the goal course of utilizing VirtualAllocEX with PAGE_EXECUTE_READWRITE permissions, permitting code execution from the newly allotted space.
Equates desk (Supply – Any.Run)
Subsequent, the malicious PE picture is written into this reminiscence area utilizing WriteProcessMemory. The malware then extracts the PEB (Course of Atmosphere Block) deal with and overwrites the ImageBaseAddress subject, guaranteeing the injected code hundreds on the appropriate reminiscence location.
This method differs from conventional course of hollowing strategies, which usually use NtUnmapViewOfSection to take away the unique course of reminiscence.
Dynamic evaluation from ANY.RUN: Increase DR by 36%, reduce MTTR by 21 minutes – Contact for Demo
By skipping this step, CastleLoader avoids triggering detection mechanisms that monitor for this suspicious exercise sample. The ultimate levels contain SetThreadContext to redirect execution to the injected payload’s entry level, adopted by ResumeThread to start execution.
This complete sequence retains the malicious code confined to reminiscence with out creating suspicious artifacts on disk till initialization completes.
The result’s a totally useful malware module that exists solely within the goal course of’s reminiscence area after alteration, rendering conventional static signature-based detection ineffective.
A breakpoint at WriteProcessMemory (Supply – Any.Run)
Safety monitoring instruments that depend on course of conduct evaluation battle as a result of every particular person element seems reliable when examined individually.
Static file signatures, behavioral heuristics, and standard course of monitoring programs show unable to detect this subtle execution mannequin, making CastleLoader an exceptionally harmful risk to organizations missing fashionable memory-based detection capabilities and endpoint detection and response options.
Expertise how ANY.RUN’s options can energy your SOC: Begin 14-Day Trial