Cybersecurity specialists are sounding the alarm a few subtle malware marketing campaign that leverages malicious ads focusing on system directors via weaponized PuTTY downloads.
This rising risk represents a major shift in assault vectors, with malicious ads now surpassing conventional phishing strategies as the first supply mechanism for malware infections.
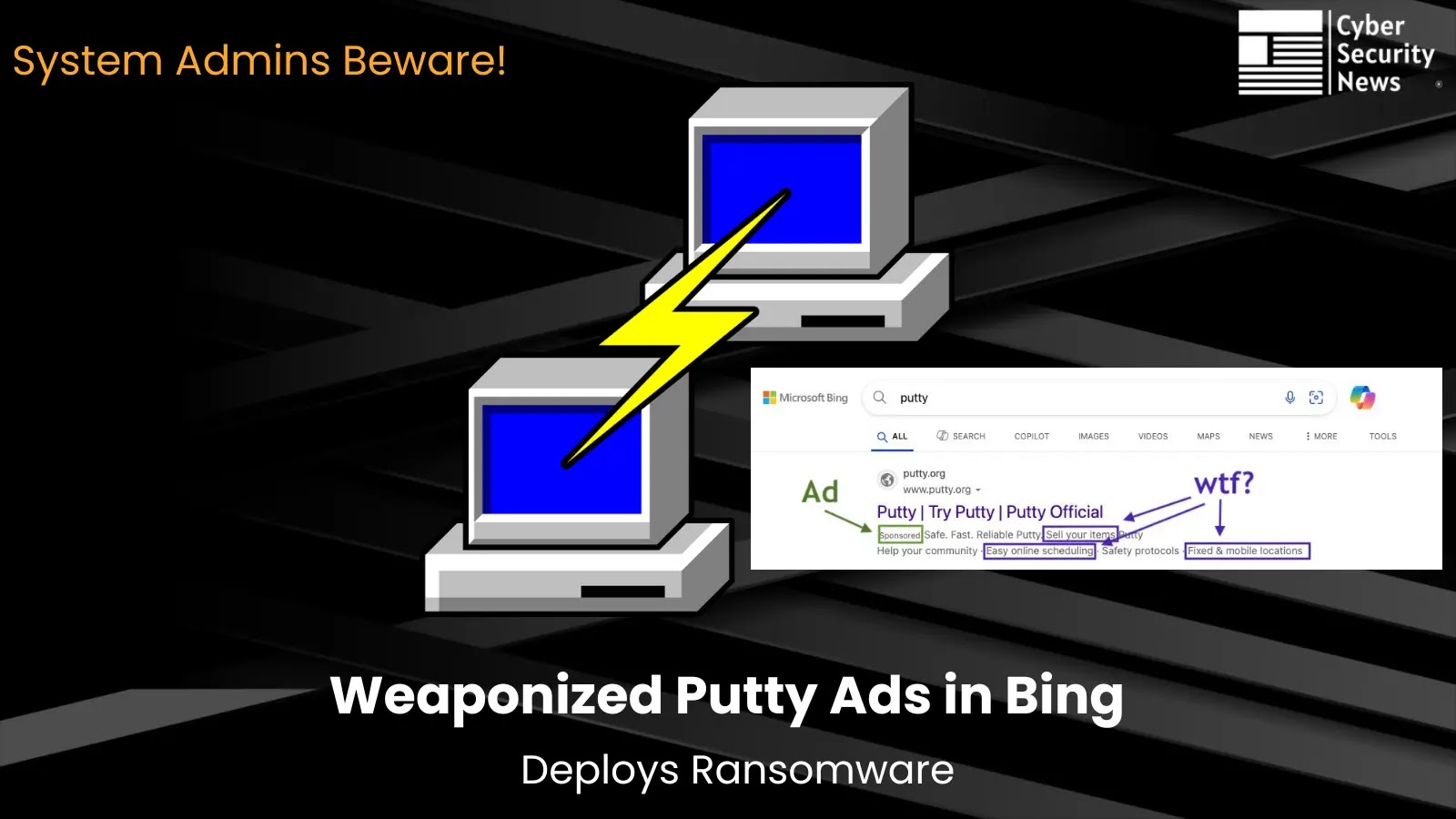
The present marketing campaign uncovered by ExpelSecurity particularly targets customers trying to find PuTTY, the broadly used SSH and telnet consumer important for system administration duties.
In line with risk intelligence analysts at Expel, attackers have strategically positioned malicious ads on the prime of Bing search outcomes, displaying what seems to be the authentic PuTTY area whereas secretly redirecting guests to attacker-controlled web sites.
This misleading method exploits the belief that system directors place in acquainted instruments and search engine outcomes.
When unsuspecting customers click on on these fraudulent ads, they unknowingly obtain compromised software program that seems authentic however incorporates harmful payloads.
A present malware marketing campaign is utilizing advertisements for PuTTY. The advert shows the authentic area however pushes the customer to the attacker-controlled web site.If downloaded & run, it masses a distant entry software often known as Oyster/Broomstick, which is understood for use by the Rhysida ransomware.— Expel (@ExpelSecurity) June 17, 2025
Refined Assault Chain Results in Ransomware
As soon as downloaded and executed, the malicious PuTTY installer deploys Oyster/Broomstick, a distant entry software with established connections to the infamous Rhysida ransomware group.
This multi-stage assault demonstrates the rising sophistication of cybercriminal operations, combining social engineering techniques with superior technical capabilities.
The malware establishes persistence on contaminated techniques by making a scheduled job named “Safety Updater” that operates from the consumer’s AppData listing.
This naming conference cleverly mimics authentic system upkeep processes, making detection tougher for each customers and safety software program.
The monetary assets behind this marketing campaign spotlight the professionalization of cybercrime.
Menace researchers report that attackers have invested a number of thousand {dollars} in latest weeks to buy authentic code-signing certificates, including a further layer of obvious authenticity to their malicious software program.
These certificates, obtained from entities together with “GALVIN & ASSOCIATES LLC,” “Shanxi Jiusheng Tongtai Buying and selling Co., Ltd.,” and “THE COMB REIVERS LIMITED,” assist the malware bypass safety controls that usually flag unsigned executables.
Technical Indicators
ExpelSecurity shared safety indicators for community defenders.
The pretend PuTTY installer IoCs
Pretend PuTTY MD5: f42dae36a47882391da920ce56f497b8, Signed by “GALVIN & ASSOCIATES LLC”
Persistence: MD5: 18b77f4f10e0a17341fdfb2371e88fb2, Signed by “Shanxi Jiusheng Tongtai Buying and selling Co., Ltd.”
Persistence: MD5: 90f0412fa7e5f3cd5f84cb80f951d539, Signed by “THE COMB REIVERS LIMITED”
Domains: fmwyd[.]com, put[.]mxcue[.]com, mvmmoving[.]com, putty[.]run
Cybersecurity specialists suggest implementing advert blockers as a primary line of protection in opposition to malicious ads.
Organizations also needs to improve their detection capabilities to shortly establish and reply to suspicious actions, notably specializing in scheduled duties and processes operating from consumer directories.
System directors ought to completely obtain software program from official vendor web sites and confirm digital signatures earlier than set up.
Energy up early risk detection, escalation, and mitigation with ANY.RUN’s Menace Intelligence Lookup. Get 50 trial searches.