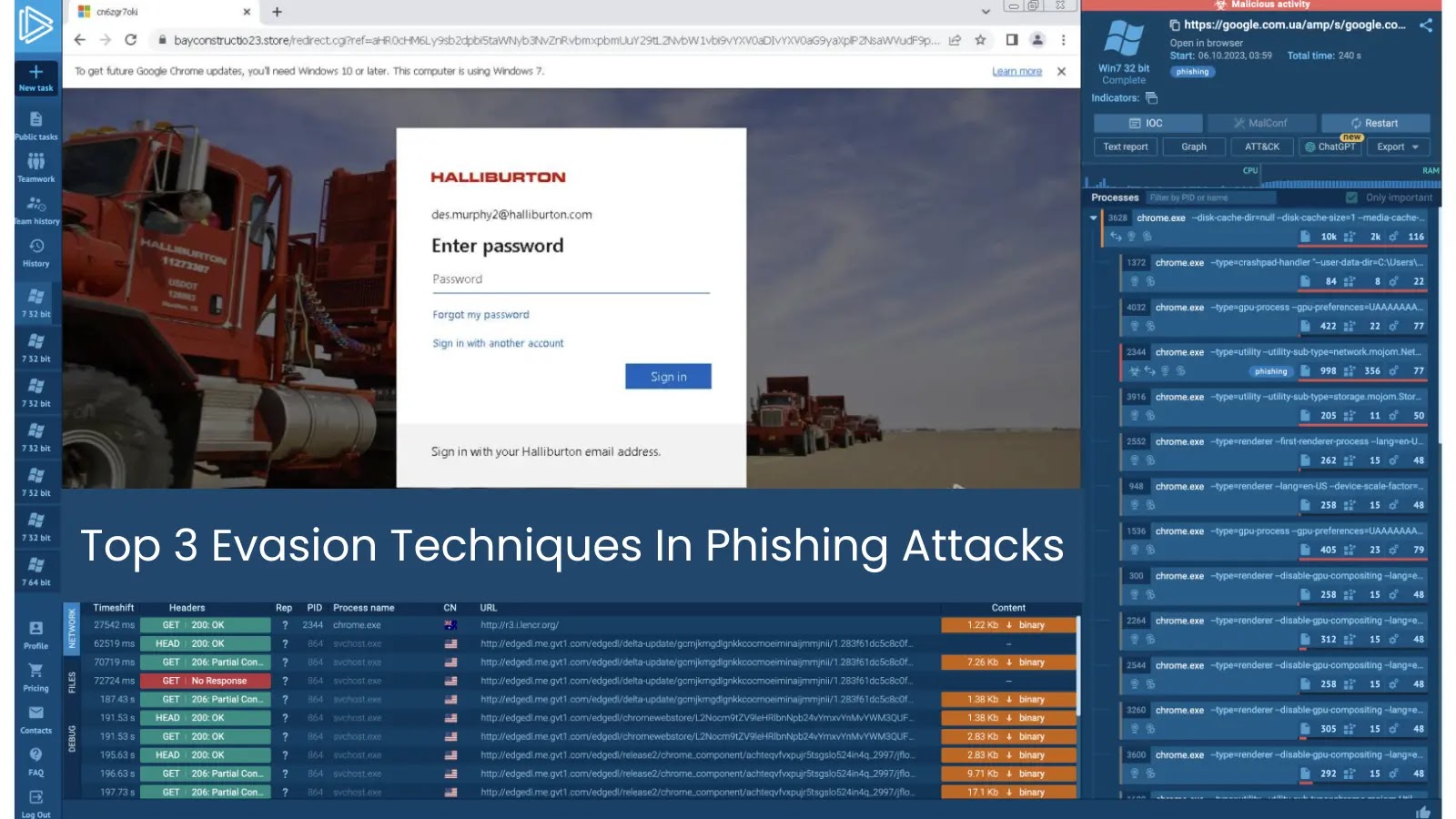
The most recent wave of credential-phishing campaigns has revealed an unexpectedly handy ally for menace actors: the very e-mail safety suites meant to guard customers.
First noticed in late July 2025, a number of phishing clusters started embedding malicious URLs contained in the official link-wrapping providers of Proofpoint’s Shield platform ( and Intermedia’s LinkSafe (
As a result of company filters already belief these domains, the wrapped hyperlinks traverse mail gateways uninspected, touchdown instantly in customers’ inboxes.
The assault chain is deceptively easy. Victims obtain invoices, DocuSign requests, or transport notices whose call-to-action buttons level to a wrapped URL.
When clicked, Proofpoint or Intermedia first decodes after which silently forwards the browser to an attacker-controlled web site that imitates Microsoft 365 or Okta single-sign-on pages.
Cloudflare researchers famous that the intermediate “trusted” hop neuters most sandbox detonations as a result of the ultimate vacation spot is resolved solely contained in the person’s session, successfully short-circuiting heuristic URL repute checks.
Marketing campaign telemetry collected by open redirect sensors exhibits greater than 180,000 messages since August 1 concentrating on monetary providers, authorized companies, and better training.
Phishing electronic mail posing as a voicemail notification containing a wrapped hyperlink (Supply – Cloudflare)
In a number of incidents, compromised mailboxes have been weaponized inside minutes to propagate the lure additional, amplifying inside unfold whereas masquerading as official reply-threads.
Phishing electronic mail posing as a Microsoft Groups Doc (Supply – Cloudflare)
The abuse underscores the paradox by which safety controls—when insufficiently scoped—grow to be high-fidelity cloaks for adversaries.
Detection Evasion by way of Opportunistic URL Rewriting
In contrast to conventional phishing that depends on freshly registered typo-domains, these campaigns exploit conditional URL decision.
Proofpoint’s wrapper shops the goal in a base64-encoded u= parameter, whereas an HMAC signature in ok= assures integrity.
Safety merchandise sometimes confirm solely the HMAC earlier than classifying the hyperlink as protected; they don’t dereference the payload throughout scanning as a result of doing so would destroy the wrapper’s anti-tampering seal.
Microsoft phishing web page designed to reap credentials (Supply – Cloudflare)
Attackers merely generate a legitimate hyperlink by letting Proofpoint create the wrapper on a benign web site, then enhancing the base64 payload with out updating the signature—Proofpoint nonetheless masses the URL however can’t assure authenticity, inflicting a silent ahead.
The next Python fragment replicates the tampering step and highlights why static scanners miss it:-
import base64, urllib.parse, re
wrapped = (”
“u=aHR0cHM6Ly93d3cuZXhhbXBsZS5jb20vP3Byb2Quaj0x&ok=abcd1234″)
payload = re.search(r”u=([^&]+)”, wrapped).group(1)
decoded = base64.urlsafe_b64decode(payload + “==”).decode()
print(‘Unique goal:’, decoded)
new_target = ”
new_payload = base64.urlsafe_b64encode(new_target.encode()).decode().rstrip(“=”)
tampered = re.sub(r”u=[^&]+”, f”u={urllib.parse.quote(new_payload)}”, wrapped)
print(‘Tampered wrapper:’, tampered)
As a result of the ok= signature isn’t re-computed, Proofpoint flags the hyperlink as “modified” however nonetheless performs the ahead—a usability concession attackers now exploit.
Intermedia’s LinkSafe exhibits a similar weak spot, missing any integrity token in any respect.
Till Proofpoint and Intermedia revise their validation logic to dam or at the least visibly warn on signature mismatches, defenders should depend on full URL detonation and on-endpoint heuristics.
Community groups are suggested to strip or rewrite wrapped hyperlinks on the secure-gateway layer, whereas SOCs ought to hunt for base64 strings inside u= parameters that decode to exterior domains.
At its core, the episode is a cautionary story: safety layers that achieve isolation can, when chained collectively with out holistic menace modeling, open a friction-free freeway straight to the attacker’s payload.
Combine ANY.RUN TI Lookup together with your SIEM or SOAR To Analyses Superior Threats -> Attempt 50 Free Trial Searches