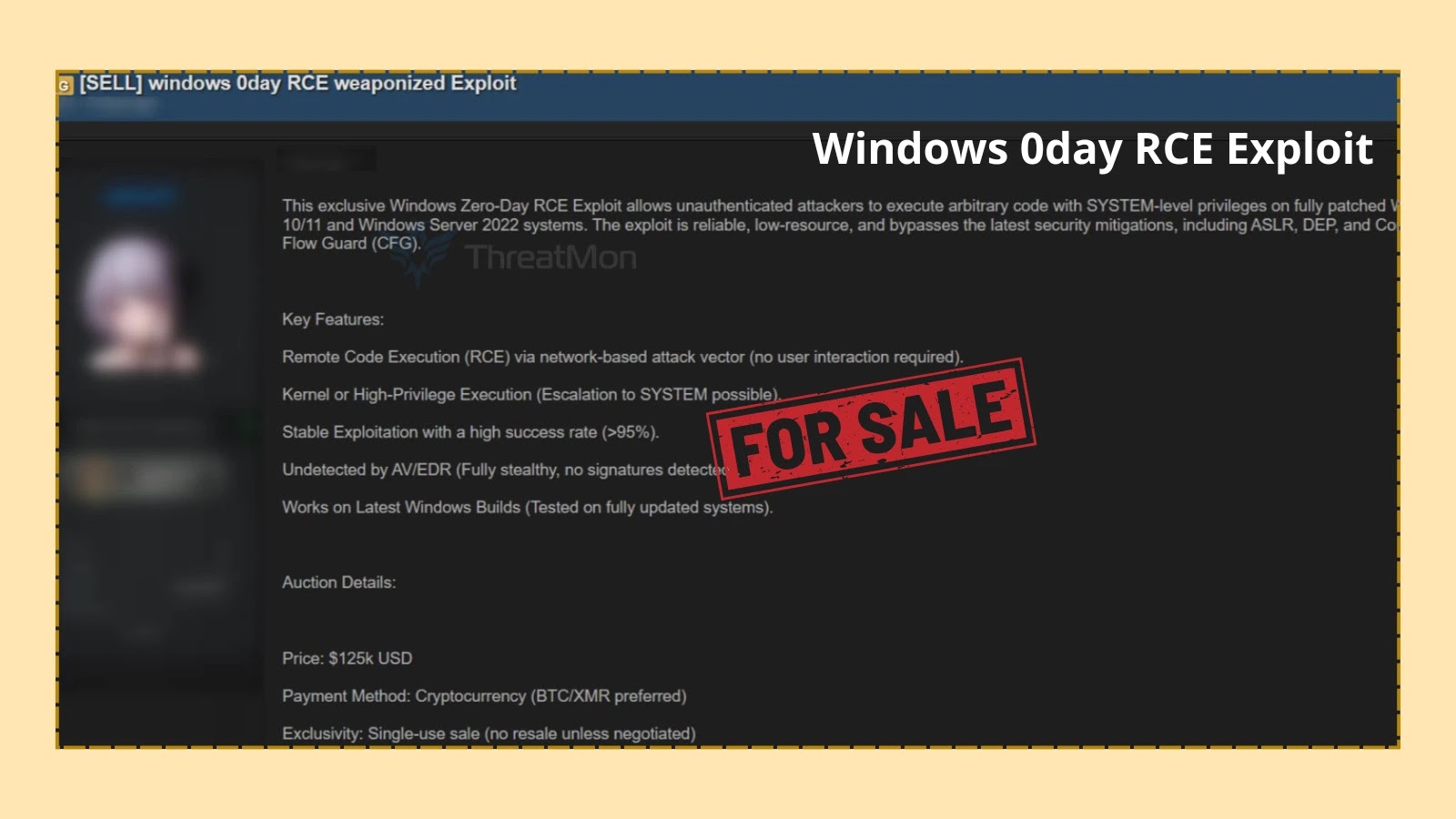
An alleged menace actor has listed a Home windows Zero-Day Distant Code Execution (RCE) exploit on the market, claiming it targets absolutely up to date Home windows 10, Home windows 11, and Home windows Server 2022 methods.
The posting reported by ThreatMon advertises weaponized exploit code purportedly able to granting SYSTEM-level privileges with no prior authentication or consumer interplay, bypassing intrinsic Home windows safety controls comparable to Deal with Area Format Randomization (ASLR), Information Execution Prevention (DEP), and Management Move Guard (CFG).
The vendor emphasizes the exploit’s technical capabilities, providing kernel-level code execution and privilege escalation on to SYSTEM—a essential concern for each enterprise and particular person methods.
Key Takeaways1. $125k Home windows zero-day RCE exploit targets patched Win10/11/Server2022 with SYSTEM privileges.2. Bypasses ASLR/DEP/CFG, evades AV/EDR detection.3. A network-based assault requires no consumer interplay.
The commercial claims that the exploit is undetected by main antivirus and endpoint detection and response (EDR) options, boasting a stealthy profile with “no signatures detected.”
With a purported success fee exceeding 95%, the exploit’s reliability makes it exceptionally engaging to superior persistent menace (APT) teams and ransomware operators.
Menace actor promoting Home windows Zero-Day (RCE) exploit
Technical Particulars of Zero-Day RCE Exploit
The exploit is designed for distant code execution (RCE) by way of a network-based assault vector, eliminating the necessity for any consumer interplay.
This tactic aligns with probably the most harmful classes of vulnerabilities, particularly these facilitating “unauthenticated distant assault floor” exploitation.
The exploit’s capability to raise privileges—usually from a normal consumer to SYSTEM, the best Home windows permission degree. Moreover, direct interplay and manipulation of the Home windows kernel bypasses typical user-mode restrictions.
Public sale particulars reveal an asking worth of USD 125,000, with cost most well-liked by way of cryptocurrency (BTC/XMR), reflecting the excessive market demand for strong, undetectable exploit code.
The sale situations emphasize exclusivity, prohibiting resale except explicitly negotiated, which is typical for premium exploits.
Organizations dealing with heightened menace landscapes ought to reinforce monitoring of anomalous kernel-level exercise, implement well timed patch administration, and deploy superior menace intelligence instruments able to detecting zero-day exploitation makes an attempt.
The incident underscores the persistent dangers related to unreported vulnerabilities and the continued evolution of cybercrime marketplaces.
It is strongly recommended to remain knowledgeable of rising menace intelligence feeds, apply obtainable mitigations, and report suspicious exercise related to zero-day vulnerabilities to related authorities and distributors.
Safely detonate suspicious information to uncover threats, enrich your investigations, and lower incident response time. Begin with an ANYRUN sandbox trial →