Cybercriminals are more and more exploiting generative synthetic intelligence platforms to orchestrate refined phishing campaigns that pose unprecedented challenges to conventional safety detection mechanisms.
The speedy proliferation of GenAI companies has created a fertile ecosystem for risk actors who leverage these platforms to generate convincing phishing content material, clone trusted manufacturers, and automate large-scale malicious deployments with minimal technical experience required.
The emergence of web-based AI companies providing capabilities corresponding to automated web site creation, pure language technology, and chatbot interplay has essentially remodeled the risk panorama.
These platforms allow attackers to supply professional-looking phishing websites inside seconds, using AI-generated photos and textual content that carefully mimic respectable organizations.
The accessibility of those instruments has lowered the barrier to entry for cybercriminals, permitting even technically unsophisticated actors to launch convincing social engineering assaults.
Distribution of classes of AI companies misused for phishing assaults (Supply – Palo Alto Networks)
Current telemetry information reveals a dramatic surge in GenAI adoption throughout industries, with utilization greater than doubling inside six months.
Palo Alto Networks researchers recognized that the high-tech sector dominates AI utilization, accounting for over 70% of whole GenAI software utilization.
This widespread adoption has inadvertently created new assault vectors as risk actors exploit the identical platforms respectable customers rely on for productiveness enhancement.
Evaluation of phishing campaigns reveals that web site mills symbolize essentially the most exploited AI service class, comprising roughly 40% of malicious GenAI misuse.
Writing assistants observe at 30%, whereas chatbots account for practically 11% of noticed assaults. These statistics underscore the varied vary of AI platforms being weaponized for malicious functions.
AI-Powered Web site Technology: The Main Assault Vector
The misuse of AI-powered web site builders represents essentially the most important risk vector on this evolving panorama.
A quick description of our firm in a immediate from the AI-assisted web site builder (Supply – Palo Alto Networks)
Researchers documented real-world examples of phishing websites created utilizing well-liked AI web site technology platforms able to producing purposeful web sites inside seconds.
The improved immediate from the AI-assisted web site builder (Supply – Palo Alto Networks)
These platforms usually require minimal verification, usually accepting any legitimate e-mail tackle with out cellphone quantity affirmation or identification verification.
The assault methodology entails risk actors inputting temporary firm descriptions into AI prompts, which routinely generate complete web site content material together with skilled imagery, convincing company narratives, and detailed service descriptions.
Throughout testing, researchers demonstrated how a easy immediate describing a cybersecurity firm resulted in a completely purposeful web site full with risk intelligence companies pages and next-generation firewall descriptions that appeared respectable to informal observers.
Webpage for discounted reward playing cards generated on one other well-liked AI-powered web site builder (Supply – Palo Alto Networks)
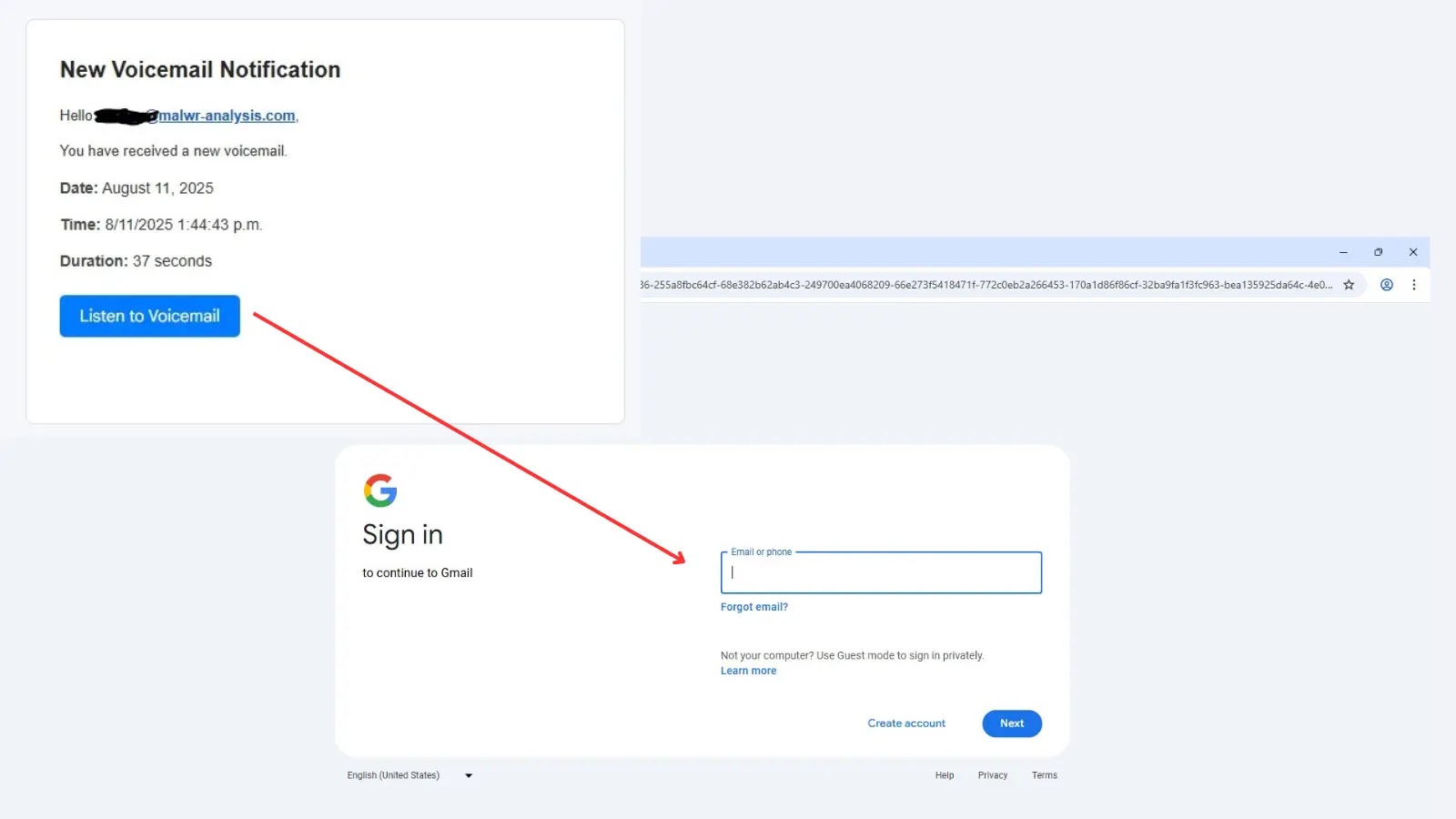
The generated phishing websites usually make use of a two-stage assault mechanism. Preliminary touchdown pages show generic messages corresponding to “You’ve got new paperwork” with outstanding call-to-action buttons.
When victims work together with these parts, they’re redirected to secondary credential-harvesting websites designed to seize login credentials for well-liked companies like Microsoft platforms.
Presently noticed assaults seem comparatively rudimentary, however safety specialists anticipate important sophistication enhancements as AI web site builders evolve.
The mix of automated content material technology, minimal platform verification necessities, and quickly enhancing AI capabilities creates a regarding trajectory for future phishing effectiveness.
Increase your SOC and assist your workforce defend your small business with free top-notch risk intelligence: Request TI Lookup Premium Trial.