Cybercriminals have shifted their focus to a extremely worthwhile goal: the trucking and logistics business.
Over the previous a number of months, a coordinated risk cluster has been actively compromising freight firms by way of deliberate assault chains designed to facilitate multi-million-dollar cargo theft operations.
The emergence of this marketing campaign represents a disturbing intersection of bodily crime and digital exploitation, the place cyber capabilities allow the theft of actual items starting from electronics to vitality drinks.
The concentrating on technique employed by these risk actors demonstrates subtle understanding of provide chain operations.
Quite than attacking particular firms, the criminals function opportunistically, intercepting communications and compromising accounts throughout the transportation sector.
Their major goal includes gaining unauthorized entry to provider techniques, which allows them to bid on official shipments and orchestrate their interception and resale on underground markets or by way of worldwide channels.
Proofpoint researchers recognized this risk cluster after detecting a big uptick in campaigns starting as early as January 2025, with intensified exercise accelerating by way of mid-2025.
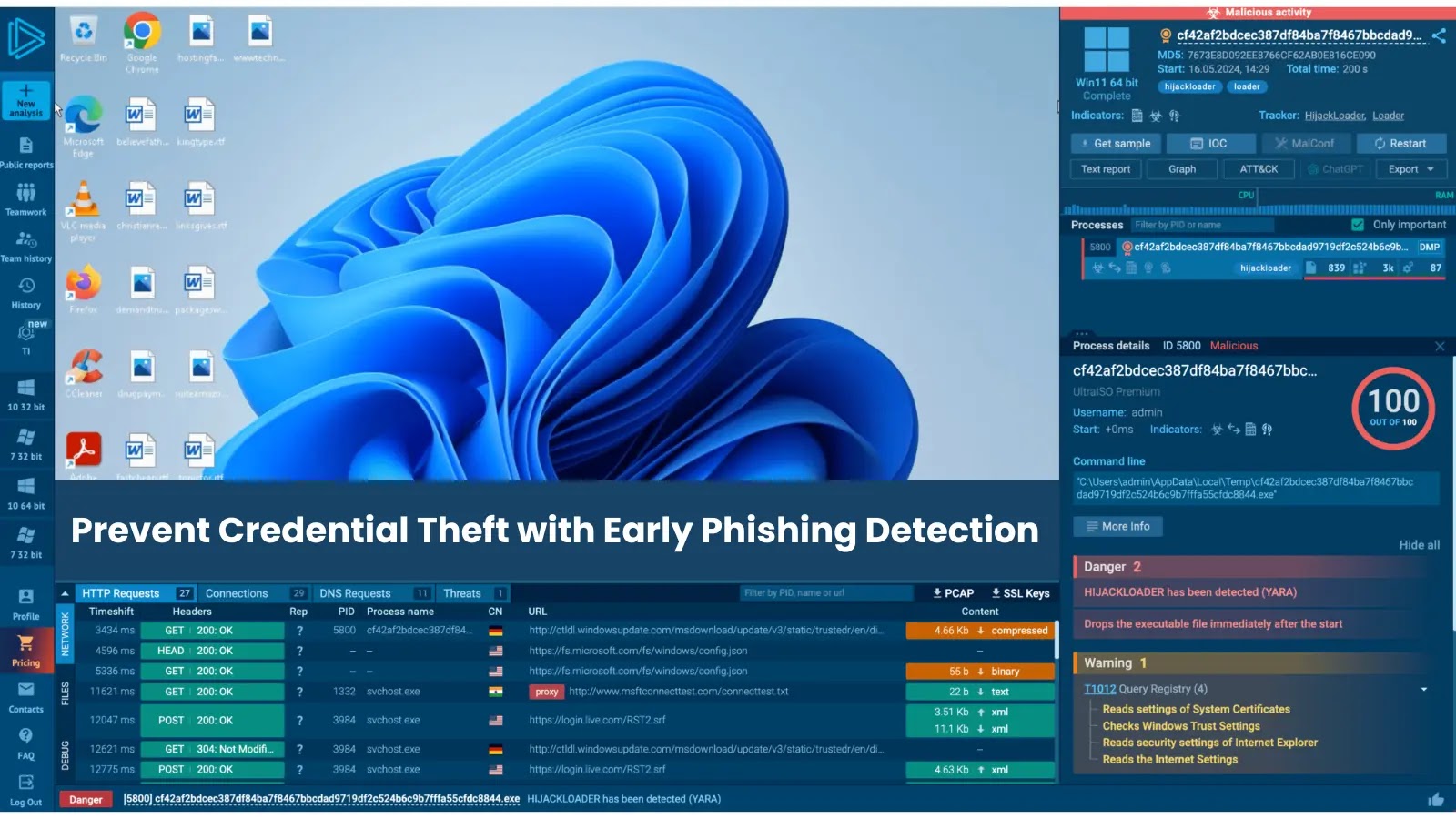
The risk actors deploy a number of distant monitoring and administration instruments together with ScreenConnect, SimpleHelp, PDQ Join, and N-able, often utilizing a number of RMM options together to ascertain persistent entry and conduct thorough system reconnaissance.
An infection mechanism
The an infection mechanism primarily depends on social engineering techniques that exploit the inherent belief and urgency current in freight business communications.
Attackers compromise load board accounts—on-line marketplaces facilitating cargo cargo bookings—then put up fraudulent listings and deploy malicious URLs when carriers specific curiosity.
Assault move (Supply – Proofpoint)
Upon execution, the embedded executables grant adversaries full system management, permitting them to reap credentials by way of instruments like WebBrowserPassView and deepen their foothold inside goal networks.
What distinguishes this marketing campaign is the seamless integration of official RMM instruments into prison infrastructure.
Not like conventional distant entry trojans, these generally used software program packages usually bypass safety detection mechanisms as a consequence of signed installer packages and bonafide popularity.
Risk actors subsequently leverage compromised entry to delete present freight bookings, manipulate dispatcher notifications, and coordinate the theft immediately utilizing the sufferer’s personal infrastructure.
Based on the Nationwide Insurance coverage Crime Bureau, cargo theft causes roughly $34 billion in annual losses, with projections indicating a 22 % enhance in 2025.
Proofpoint has documented almost two dozen campaigns inside simply two months, suggesting this exploitation pattern will proceed accelerating as criminals acknowledge the effectiveness and profitability of cyber-enabled cargo theft operations.
Comply with us on Google Information, LinkedIn, and X to Get Extra Immediate Updates, Set CSN as a Most popular Supply in Google.