In a regarding improvement for web customers, cybercriminals have devised a complicated new method to control Google search outcomes, successfully poisoning them to show fraudulent contact info.
In contrast to conventional phishing schemes that depend on faux web sites, this novel method leverages professional company web sites whereas subtly altering displayed cellphone numbers, creating a virtually undetectable rip-off vector for unsuspecting customers looking for assist from main manufacturers.
The rip-off begins when risk actors buy sponsored commercials on Google search outcomes, mimicking official listings from outstanding corporations.
When customers click on these sponsored hyperlinks, they’re directed to the precise professional web site of the corporate in query – not a fraudulent clone as usually seen in phishing assaults.
This significant distinction makes the scheme significantly insidious, as customers haven’t any visible indication that something is amiss.
What makes this assault vector particularly harmful is the proper phantasm of legitimacy it creates.
Customers observe the genuine URL of their browser’s deal with bar and work together with the real web site’s interface and content material.
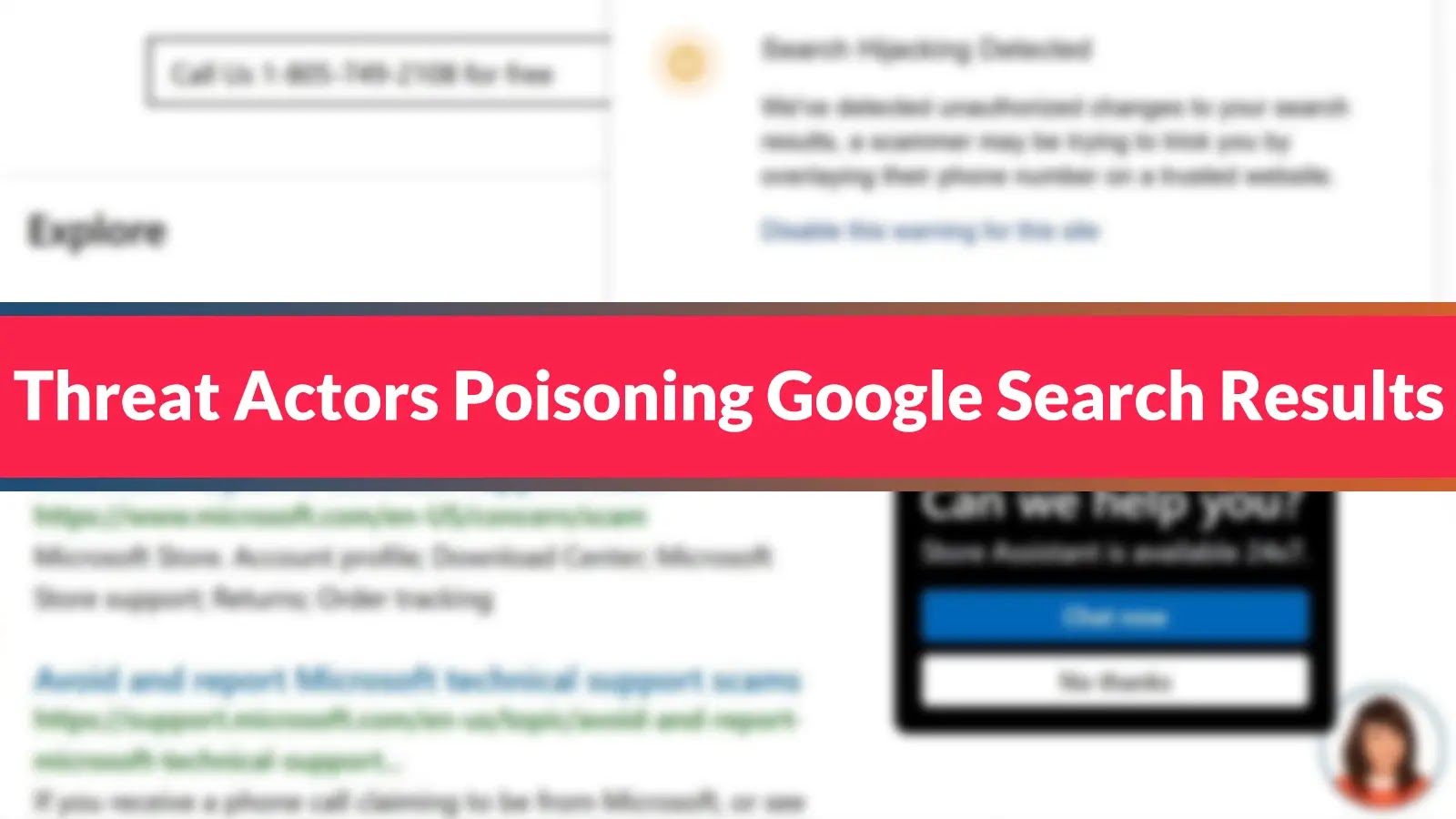
Nevertheless, unbeknownst to them, the search outcomes have been manipulated to show the scammer’s cellphone quantity rather than the corporate’s professional contact info.
Malwarebytes researchers recognized this rising risk earlier this week, noting that when victims name these fraudulent numbers, they unwittingly join with scammers posing as official buyer assist representatives.
“These ways are remarkably efficient due to the a number of layers of authenticity they current to potential victims,” defined Malwarebytes of their evaluation revealed on June 18, 2025.
The influence of this system extends past quick monetary fraud.
Cybercriminals steadily use advertisements directing to a malicious web site to make the most of our belief in sponsored search outcomes for common manufacturers. Of their newest rip-off, we discovered tech assist scammers hijacking the outcomes of professional websites.Here is the way it works. 🧵 pic.twitter.com/TgvQTjIFox— Malwarebytes (@Malwarebytes) June 18, 2025
By gaining a sufferer’s belief via the looks of legitimacy, scammers can extract delicate private info, fee particulars, and even persuade customers to grant distant entry to their gadgets – probably resulting in ransomware set up, knowledge theft, or persistent community compromise.
Technical Mechanism of Search End result Poisoning
The technical sophistication behind this assault reveals cautious planning by risk actors.
Reasonably than using conventional client-side browser manipulation or DNS hijacking, the scammers have recognized vulnerabilities in how sponsored search outcomes are rendered and exhibited to customers.
The assault chain begins with the creation of rigorously crafted Google Advertisements campaigns that seem an identical to professional model commercials.
When customers click on these sponsored hyperlinks, they’re certainly directed to the genuine web site via a collection of redirects that protect the professional area within the deal with bar.
Nevertheless, throughout this redirect course of, the scammers implement a delicate however efficient parameter manipulation that influences how contact info seems inside search end result snippets.
This system exploits the way in which search engines like google and yahoo cache and show structured knowledge, permitting the attackers to selectively override particular parts whereas sustaining the location’s general authenticity.
This method is especially efficient when focusing on high-value companies like Netflix, banking platforms, and technical assist companies the place customers generally seek for customer support numbers and could also be ready to share delicate info to resolve account points.
By understanding consumer conduct patterns and exploiting the implicit belief positioned in each Google’s search outcomes and legit company web sites, the scammers have created a remarkably efficient social engineering method that bypasses many conventional safety consciousness coaching protocols.
Are you from SOC/DFIR Groups! – Work together with malware within the sandbox and discover associated IOCs. – Request 14-day free trial