Over the previous yr, safety groups have noticed an uptick in adversaries leveraging native Home windows Scheduled Duties to take care of footholds in compromised environments.
Not like elaborate rootkits or zero-day exploits, these strategies exploit built-in system performance, enabling menace actors to persist with out deploying further binaries or complicated toolchains.
By integrating malicious instructions instantly into Activity Scheduler jobs—triggered on boot, logon, or at timed intervals—attackers obtain stealthy, resilient entry that usually eludes standard detection mechanisms.
Preliminary infections sometimes start with phishing emails or exploit kits delivering light-weight loaders that pivot shortly to persistence.
As soon as they obtain execution on the endpoint, attackers invoke both the schtasks.exe binary or PowerShell cmdlets to register new duties or modify current ones. These jobs might execute underneath the SYSTEM account, additional complicating detection.
Early samples focused monetary establishments, whereas more moderen campaigns have expanded into essential infrastructure sectors, highlighting the broad applicability and low operational price of Scheduled Duties abuse.
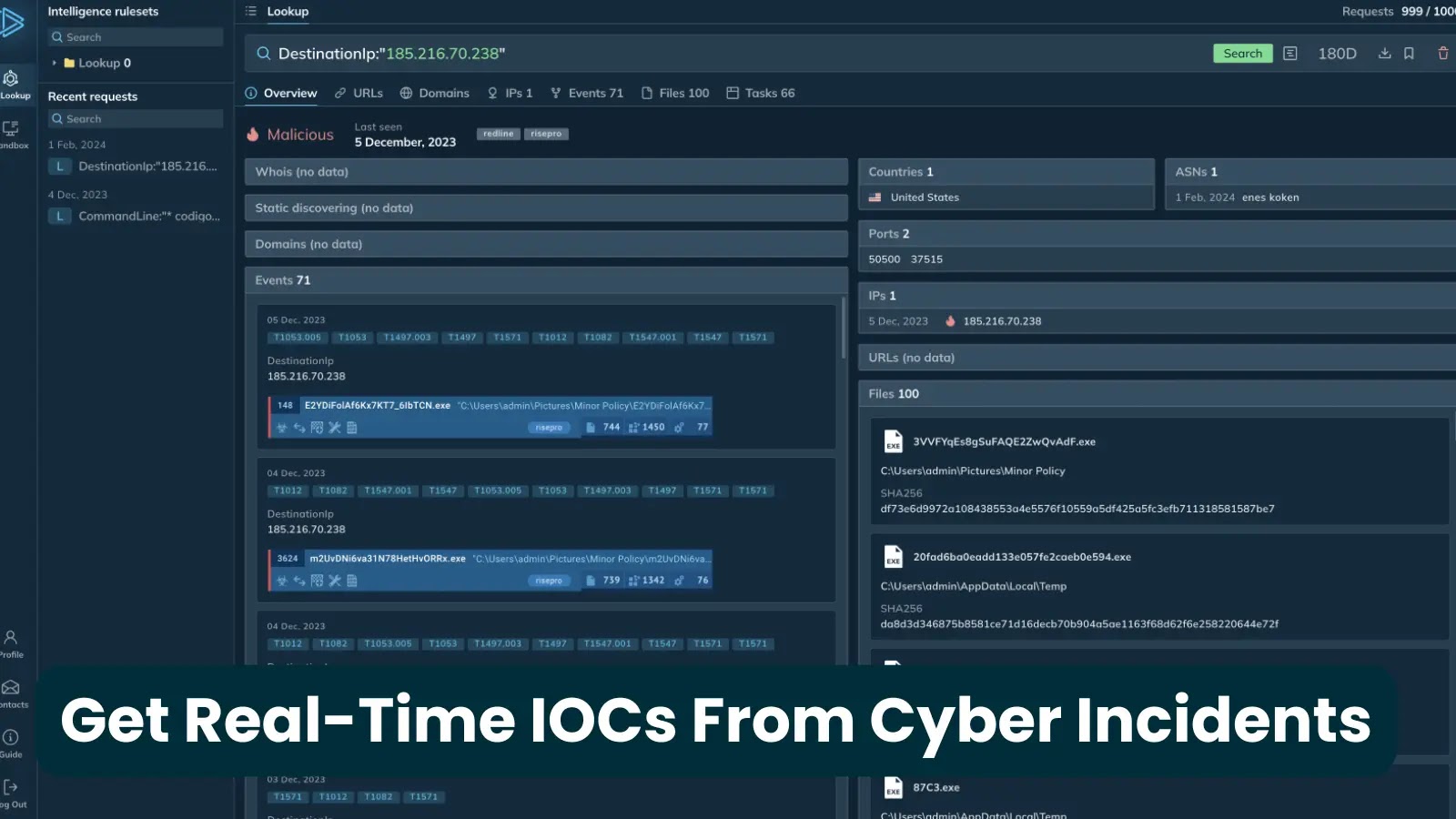
The DFIR Spot analysts famous the malware’s reliance on triggers equivalent to LogonTrigger and TimeTrigger, configured to execute each 5 minutes or upon every person logon.
In a number of engagements, Incident Response groups found duties named to imitate reliable Home windows companies—equivalent to “TelemetryUpdater” or “HealthCheck”—however pointing to executables saved in unconventional directories underneath C:ProgramDataSystem.
This strategy permits the malicious elements to mix into routine system exercise, delaying evaluation and remediation.
Subsequent payloads delivered by way of these duties vary from coin-mining binaries to distant administration instruments.
As soon as registered, duties typically self-update by invoking PowerShell scripts that pull further modules or change command-line arguments.
As a result of Activity Scheduler logs could be cleared or disabled by attackers, many organizations have struggled to reconstruct timelines with out enriched EDR telemetry.
Persistence Techniques: Malicious Activity Registration and Execution
A core persistence mechanism entails the command-line invocation:-
schtasks /create /sc minute /mo 5 /tn “MicrosoftWindowsUpdateTelemetryUpdater”
/tr “C:ProgramDataSystemsvchost32.exe –url=stratum+tcp://miner.fakepool.native:3333 –user visitor”
/ru SYSTEM
Scheduled Activity Creation Command (Supply – The DFIR Spot)
On this snippet, the /sc minute /mo 5 parameters dictate a five-minute interval, whereas the duty title and listing buildings mimic genuine Home windows updates. Attackers incessantly select TimeTrigger parts within the XML activity file to specify each begin boundaries and indefinite repetition, as in:
2025-08-17T00:00:00
PT5M
false
Malicious Activity XML Configuration (Supply – The DFIR Spot)
After creation, the job executes with SYSTEM privileges, launching a loader that contacts a distant C2 or payload repository.
By embedding the executable in nonstandard paths and abusing native scheduling options, menace actors obtain persistence with out requiring further exploitation frameworks.
Detection methods should embrace rigorous baselining of reliable scheduled duties, monitoring TaskScheduler/Operational logs for Occasion ID 106 (activity registered), and imposing superior audit insurance policies to seize Occasion ID 4698 entries.
Combining these logs with EDR-driven course of lineage evaluation can reveal anomalous activity creation patterns that diverge from regular administrative operations.
Increase your SOC and assist your crew defend your corporation with free top-notch menace intelligence: Request TI Lookup Premium Trial.