High quality risk intelligence has historically been the area of enterprise-level budgets and premium subscriptions.
The type of contemporary, actionable knowledge that transforms how SOCs function has remained frustratingly out of attain for a lot of organizations. Till now.
A Recreation-Altering Alternative For Your Safety Operations
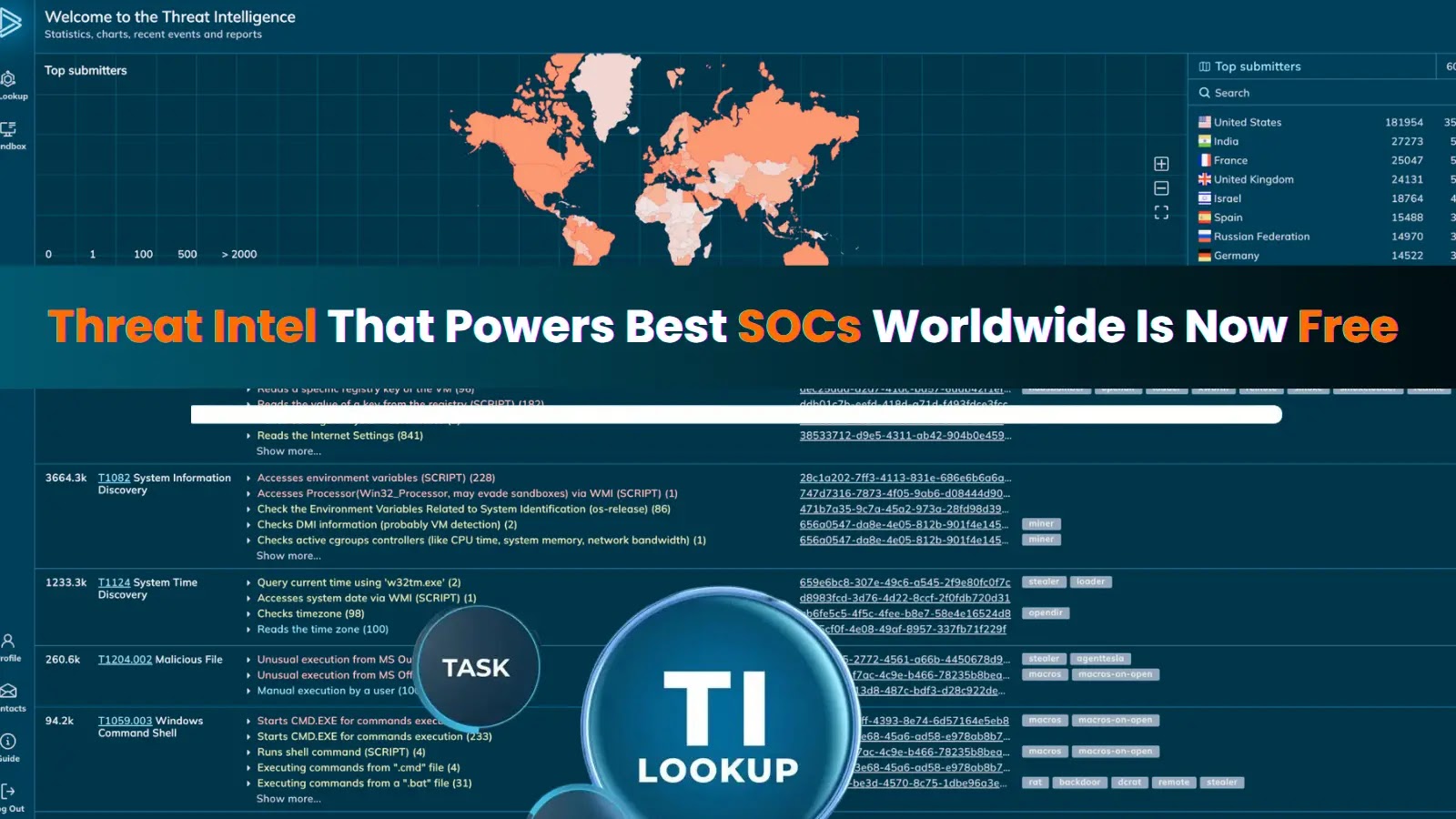
Menace Intelligence Lookup permits to seek for threats, IOCs, and extra
ANY.RUN has simply made an unprecedented transfer that may reshape how safety groups worldwide entry essential risk intelligence.
Their Menace Intelligence Lookup service now features a complete free plan that delivers the identical real-world assault knowledge investigated by over 15,000 firms globally.
Join now and get free Menace Intelligence to reveal malware concentrating on your enterprise and deal with incidents quicker with wealthy risk context
This isn’t a restricted trial or a watered-down model. It’s a stable entry to stay risk intelligence derived from hundreds of thousands of malware evaluation periods, obtainable for free of charge to your group.
The Intelligence Engine Your SOC Has Been Ready For
Menace Intelligence Lookup represents a elementary shift in how safety groups can entry and make the most of risk knowledge.
The service allows you to navigate indicators of compromise (IOCs), assault patterns (IOAs), and behavioral signatures (IOBs) derived from actual incidents analyses inside hours after they really occurred.
The intelligence supply is uniquely highly effective: each knowledge level comes from precise malware evaluation periods carried out in ANY.RUN’s Interactive Sandbox.
This implies your analysts achieve entry to risk intelligence from stay assaults concentrating on firms throughout finance, manufacturing, transportation, authorities, and different essential sectors.
On your safety operations, this interprets to:
Proactive Protection Capabilities: Your workforce can determine and put together for rising threats earlier than they impression your infrastructure, shifting from reactive response to predictive safety.
Enhanced Investigation Pace: When incidents happen, your analysts can instantly entry behavioral context and assault patterns, dramatically lowering imply time to response (MTTR).
Intelligence-Pushed Resolution Making: Each safety determination turns into backed by real-world knowledge quite than assumptions, enhancing each accuracy and confidence in risk assessments.
What Your Group Good points With The Free Plan
The free tier delivers the capabilities that may instantly improve your safety operations:
Limitless fundamental searches querying file hashes, URLs, domains, IP addresses, MITRE ATT&CK strategies, Suricata IDs.
Entry to twenty latest sandbox periods per question, offering complete assault context.
Actual-time risk verification with immediate verdicts on suspicious indicators.
MITRE ATT&CK integration permitting your analysts to check precise ways, strategies, and procedures utilized in stay assaults
Direct sandbox entry for deeper investigation of recognized threats.
Your SOC analysts can instantly start enriching their investigations with knowledge from precise assaults, whereas risk hunters can proactively analysis rising campaigns concentrating on your trade or area.
Menace Intelligence Lookup’s Free Plan: Actual-World Use Instances
Not only for SOC analysts, but in addition for threats hunters or safety lovers, ANY.RUN’s options equip professionals to reply to threats quicker, smarter, and with larger confidence.
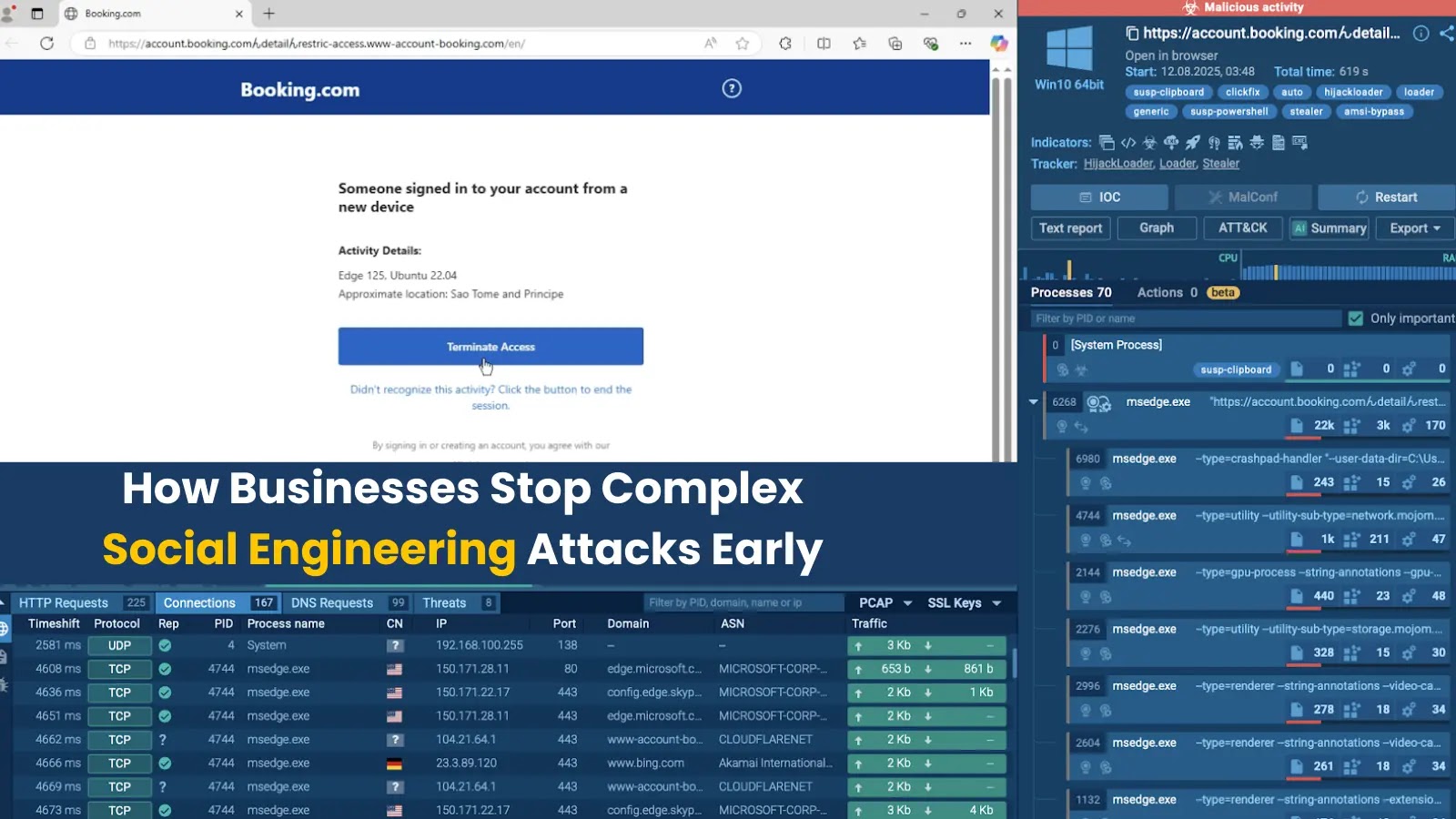
Quick Triage And Information-Fueled Response
When a suspicious area emerges in community connections, search it in TI Lookup to get an instantaneous actionable verdict:
domainName:”smtp.godforeu.com”
TI Lookup area search outcomes
Apart from the fast “Malicious” verdict sufficient to escalate the incident, the lookup outcomes sign an analyst that the area belongs to the infamous Agent Tesla stealer and that it has been noticed in the latest assault investigations thus figuring out an precise risk.
Menace Looking For Proactive Protection
Proactive discovery of the indicators of community compromise may also be taken to the subsequent degree with TI Lookup.
As an illustration, to see if a sure malware targets a selected area, use a compound question combining the risk title and the nation identifier:
threatName:”tycoon” AND submissionCountry:”de”
Contemporary Tycoon phishing assaults on firms in Germany
The search outcomes comprise hyperlinks to Interactive Sandbox public analyses of Tycoon 2FA phishing package samples submitted by customers from Germany.
Every evaluation session could be considered to check the malware habits and accumulate indicators.
Premium Capabilities For Superior Safety Operations
When you’re prepared for a level-up, the Premium plan transforms TI Lookup right into a complete safety intelligence platform:
Superior Search Operations: Over 40 search parameters with complicated operators (AND, OR, NOT) allow exact risk looking and investigation workflows.
Full Assault Visibility: Entry to all obtainable evaluation periods quite than simply the 20 most up-to-date, offering complete historic context.
Personal Intelligence: Conduct confidential searches and investigations with out visibility to different customers, defending delicate safety operations.
Steady Monitoring: Search Updates function offers automated alerts when new threats match your specified standards, making certain your workforce stays forward of rising campaigns.
Skilled Evaluation: TI Experiences from ANY.RUN’s analyst workforce ship strategic insights on assault developments and risk actor actions throughout industries.
These premium capabilities don’t simply improve your safety operations. They essentially remodel how your SOC approaches risk detection, investigation, and response.
Request trial entry to TI Lookup Premium
Reduce MTTR, cease incidents early, and scale back enterprise dangers
Implementing Intelligence-Pushed Safety At present
Integration begins instantly upon free account registration. Your analysts can begin enriching their present investigations inside minutes, utilizing the service’s intuitive interface to correlate present alerts with real-world assault knowledge.
For automated integration, the Premium plan’s API permits direct connection along with your safety infrastructure.
Whether or not you’re working a SIEM, risk intelligence platform, or safety orchestration system, Menace Intelligence Lookup can start feeding actionable intelligence into your present workflows.
The time to behave is now. Over 500,000 cybersecurity professionals already depend on ANY.RUN’s intelligence to guard their organizations.
Your safety workforce deserves entry to the identical caliber of risk intelligence that powers the world’s simplest SOCs. Direct your safety groups to discover this chance as we speak.
They’ll thanks for offering them with intelligence that transforms their capability to guard your group: and your enterprise will profit from the improved safety posture that follows.