Dynamic malware evaluation instruments execute suspicious binaries in remoted sandboxes to seize runtime behaviors file modifications, community site visitors, registry modifications, and persistence mechanisms.
This high 10 checklist particulars every device’s options, strengths, and limitations to information your choice.
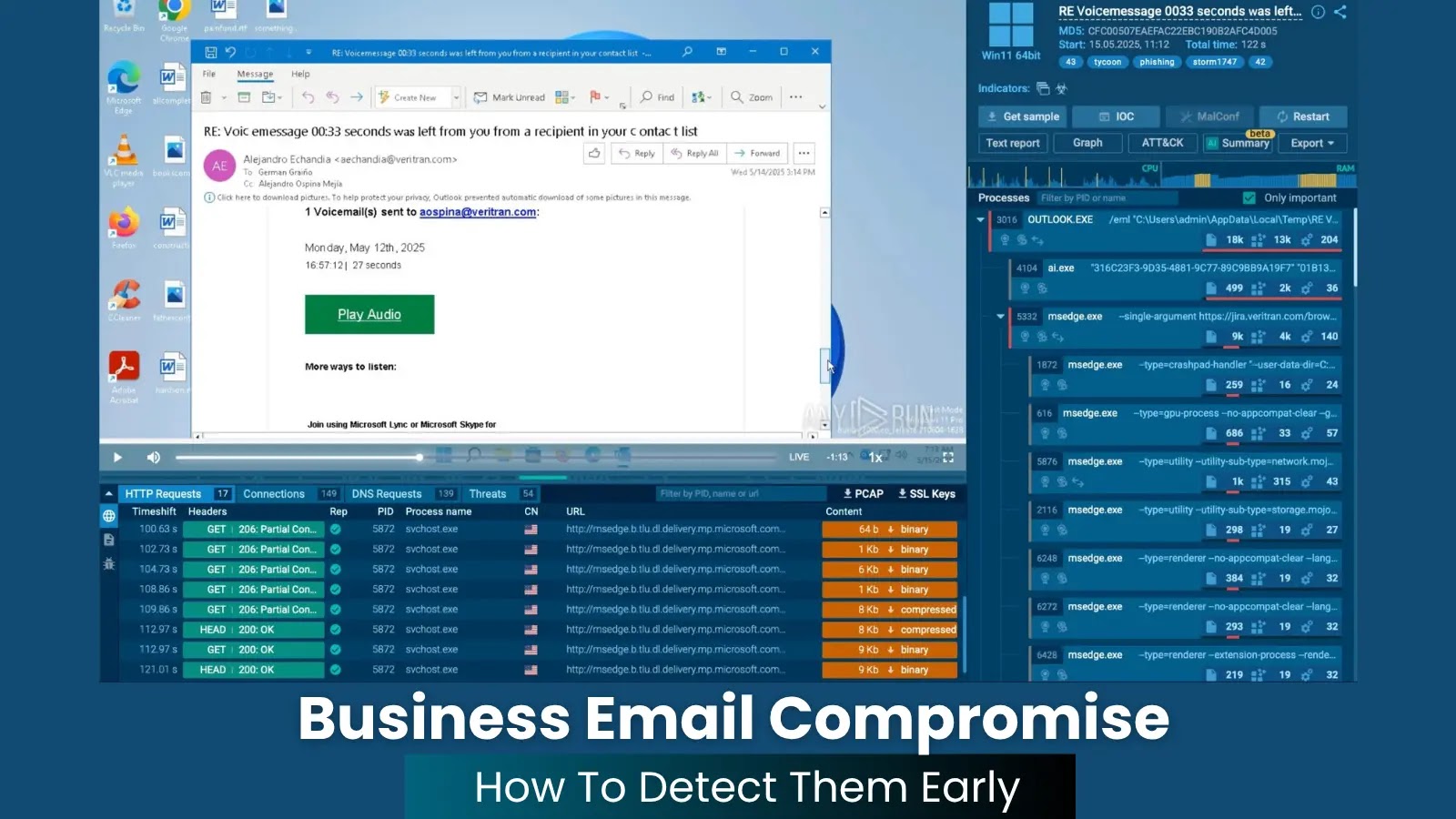
ANY.RUN’s Interactive Sandbox leads with real-time evaluation mapped to MITRE ATT&CK, empowering SOC groups and researchers to detect and mitigate threats effectively.
What Is Dynamic Malware Evaluation?
Dynamic malware evaluation is the method of executing doubtlessly malicious software program in a managed atmosphere to look at its real-time habits.
Not like static evaluation, which examines the code with out operating it, dynamic evaluation entails interacting with the malware to know the way it alters the system and impacts a community throughout execution.
This method is especially helpful for analyzing subtle or obfuscated malware that hides its true habits by encryption or packing.
Malware evaluation entails monitoring varied system interactions to know its habits. This contains figuring out file system modifications by detecting created, modified, or deleted recordsdata.
Community actions are monitored to trace connections to Command-and-Management (C2) servers, particular IP addresses, or domains. Evasion strategies are additionally recognized, together with anti-analysis mechanisms like sandbox evasion, virtualization detection, or encryption.
System influence is examined by analyzing alterations to system parts such because the Home windows registry, processes, and companies. Moreover, course of habits is noticed by API calls, reminiscence injections, and subprocess creation.
Significance Of Dynamic Malware Evaluation
With the rising complexity of recent malware, dynamic malware evaluation has change into a core a part of cybersecurity methods. Some advantages embrace:
Detecting Superior Threats:Dynamic evaluation can establish behaviors hidden by obfuscation or encryption, comparable to ransomware payloads, banking trojans, and fileless malware.
Extracting Indicators of Compromise (IoCs):Analysts can establish hashes, malicious URLs, IP addresses, and registry keys used within the assault.
Actual-Time Insights:Dynamic evaluation gives real-time insights into an assault vector, enabling quicker incident response and mitigation.
Contextual Understanding of Assaults:Safety researchers can perceive the malware’s intent, figuring out whether or not it exfiltrates knowledge, propagates laterally, or installs different payloads.
Enhancing Menace Intelligence:Findings from dynamic evaluation contribute to menace intelligence by profiling malware households and menace actors.
How Dynamic Malware Evaluation Works
Dynamic malware evaluation entails executing malware in a managed, remoted atmosphere to simulate real-world assault eventualities.
The method begins with establishing a digital machine (VM) or sandbox configured to resemble an precise consumer atmosphere whereas making certain isolation to forestall exterior system compromise.
The malware is then executed utilizing instruments like ANY.RUN, Cuckoo Sandbox, or Joe Sandbox. Analysts observe and log its habits, monitoring modifications to recordsdata, processes, reminiscence, registry, and community exercise.
Key indicators of compromise (IoCs), comparable to file hashes, malicious IP addresses, and URLs, are extracted for additional evaluation.
Lastly, a complete report is generated, summarizing the malware’s habits, IoCs, and potential influence, which could be shared with incident response groups or built-in into safety programs.
Methods Used In Dynamic Malware Evaluation
Dynamic malware evaluation employs a mix of instruments and strategies to disclose malware habits:
Right here’s the knowledge structured in a desk format:
Evaluation TypeDescriptionExampleBehavioral AnalysisMonitors system modifications, community communications, and reminiscence utilization.Analyzing a trojan that connects to a distant server for knowledge exfiltration.API Name MonitoringTracks API calls made by malware to know system-level interactions.Monitoring calls to APIs like RegCreateKey or CreateFileW.Community Site visitors AnalysisIdentifies malicious actions comparable to DNS lookups, HTTP requests, or knowledge exfiltration.Utilizing instruments like Wireshark to research site visitors to a Command-and-Management server.Reminiscence AnalysisInvestigates malware that operates totally inside system reminiscence (fileless malware).Utilizing instruments like Volatility to extract and analyze reminiscence dumps.Consumer Interplay SimulationSome malware prompts solely after particular consumer actions, like enabling macros or clicking pop-ups.Interactive instruments like ANY.RUN permit analysts to simulate these actions.
Cyber Safety Information Prime Decide
Main the checklist is ANY.RUN, a extremely interactive, cloud-based sandbox that stands out for its real-time, hands-on method to analyzing malicious samples. Let’s discover the service intimately.
ANY.RUN is an modern, cloud-based malware evaluation service that permits customers to work together with malware samples in real-time.
Not like conventional sandboxes, which run routinely, ANY.RUN gives analysts with the choice to work together with recordsdata manually, which is especially useful when analyzing malware that requires consumer enter to execute payloads.
Key Options of ANY.RUN:
Actual-Time Interplay:Customers can set off malware manually by simulating clicks, keystrokes, or different actions. This functionality is ideal for analyzing subtle malware like ransomware or droppers that rely on consumer interplay to finish their assault chain.
Dynamic Visualization:ANY.RUN presents an in depth and intuitive course of tree, showcasing occasions like file operations, registry modifications, and community actions in actual time.
Complete Community Monitoring:The service captures and visualizes all community site visitors, together with DNS queries, HTTP requests, and C2 communications. PCAP recordsdata could be downloaded for deeper evaluation with instruments comparable to Wireshark.
IoCs Extraction:Robotically generates an inventory of Indicators of Compromise (IoCs), comparable to IP addresses, domains, dropped file hashes, and malicious URLs.
Collaborative Atmosphere:Analysts can collaborate in actual time, making it a superb service for incident response groups.
Extensive File Help:Helps an intensive vary of malicious file codecs, together with executables, scripts, paperwork, and URLs.
10 Dynamic Malware Evaluation ToolsFeaturesStand-alone FeaturePricingFree Trial / Demo1. ANY.RUNReal-time interplay, dynamic visualizations, collaboration, community site visitors evaluation, and customizable environments.Interactive, real-time malware evaluation platformFree tier accessible.Yes2. Cuckoo SandboxOpen-source, API name monitoring, community site visitors monitoring, virtualized environments, multi-format file assist.Open-source automated malware evaluation toolOpen-source; free to make use of.Yes3. Joe SandboxCross-platform assist, deep reminiscence forensics, YARA rule integration, IoC extraction.Superior multi-platform malware evaluation enginePro cloud tiers begin at $4,999/12 months.Yes4. Hybrid AnalysisCloud-based, computerized IoC era, static and dynamic evaluation mixture, severity scoring.Cloud-based malware intelligence and sandboxFree to make use of. Yes5. Intezer AnalyzeCode reuse detection by binary DNA expertise, quick evaluation, advanced malware household classification.Code reuse evaluation for malware classificationFree tier accessible; contact for premium pricing.Yes6. FireEye Malware AnalysisEnterprise-grade resolution, zero-day detection, integration with menace intelligence, reminiscence forensics.Enterprise-grade malware detection and forensicsPricing particulars not publicly accessible; contact for quote.Yes7. Detux (Linux-Centered)Open-source, Linux-specific malware evaluation, modular structure, real-time monitoring.Linux-specific malware evaluation sandboxOpen-source; free to make use of.Yes8. Cape SandboxPayload extraction, assist for packed malware, detailed reporting, prolonged Cuckoo Sandbox capabilities.Cuckoo-based sandbox with course of injectionOpen-source; free to make use of.Yes9. MalwareBazaar SandboxFree, scalable cloud sandbox, detailed malware habits reporting, concentrate on IoC era.Malware pattern sharing and evaluation platformFree to make use of.Yes10. RemnuxLinux-based toolkit, community site visitors evaluation, reverse engineering capabilities, vast device integration.Linux toolkit for malware reverse engineeringFree to make use of.Sure
1. ANY.RUN (Finest Total)
ANY.RUN is a extremely interactive cloud-based sandbox designed for real-time malware evaluation. Not like conventional sandboxes, it permits analysts to manually work together with malicious recordsdata to simulate consumer actions (e.g., clicking, typing), which might reveal hidden behaviors.
This makes ANY.RUN is right for analyzing ransomware, droppers, and malware that require consumer enter to operate totally. It additionally helps collaborative workflows, making it a superb selection for Safety Operations Facilities (SOCs).
With stay collaboration options, a number of analysts can work on the identical session, making certain quicker incident responses.
Its highly effective suite of options, together with TI Lookup, YARA Search, and Feeds, allows customers to research threats, monitor malicious exercise, and collaborate successfully.
With ANY.RUN, safety groups can:
Detect malware in seconds
Work together with samples in actual time
Save money and time on sandbox setup and upkeep
Report and analyze all facets of malware habits
Scale their operations as wanted
Key Options:
Actual-Time Interplay: Analysts can simulate consumer actions to set off malware behaviors.
Dynamic Visualizations: Offers detailed course of bushes, file manipulations, and community graphs in actual time.
IoC Extraction: Robotically generates lists of indicators of compromise (IoCs) comparable to file hashes, malicious IPs, and domains.
Collaboration: Permits a number of analysts to collaborate on the identical evaluation session.
Customizable Environments: Analysts can configure digital machines (e.g., Home windows 10) with particular setups to emulate real-world eventualities.
What’s Good?What May Be Higher?Newbie-friendly interface.Cloud dependency might not swimsuit organizations with strict insurance policies.Best for malware requiring consumer interplay.Superior options can be found solely in paid variations.Glorious collaborative options for crew evaluation.Actual-time execution with detailed visualizations.
2. Cuckoo Sandbox
Overview:Cuckoo Sandbox is likely one of the most acknowledged open-source options for malware evaluation. It gives a versatile and extensible atmosphere to execute and monitor malicious recordsdata throughout varied codecs, together with paperwork, scripts, and executables.
Its modular design permits for intensive customization, enabling analysts to increase its performance with plugins or combine it with instruments like YARA guidelines, Suricata for intrusion detection, or Volatility for reminiscence forensics.
Key Options:
Screens API calls, file manipulations, and community site visitors.
Helps virtualized, bodily, or cloud environments.
Generates detailed JSON or HTML stories for additional investigation.
What’s Good?What May Be Higher?Free to make use of and extremely customizable.Requires technical experience for setup and upkeep.Helps varied file varieties and working environments.Time-consuming configuration for new customers.Versatile integration with instruments like YARA and Suricata.
3. Joe Sandbox
Overview:Joe Sandbox is a industrial device that stands out for its depth of study throughout a number of platforms, together with Home windows, Linux, macOS, Android, and iOS.
It helps a variety of file codecs and goes past primary dynamic evaluation by simulating consumer interactions, enabling analysts to uncover hidden behaviors in malware.
With its deep reminiscence forensics capabilities, Joe Sandbox is particularly suited to investigating superior threats like APTs or state-sponsored assaults.
Key Options:
Multi-platform assist for analyzing cross-OS threats.
Detailed reminiscence evaluation and course of simulation.
YARA rule integration for customized menace detection.
What’s Good?What May Be Higher?Multi-platform assist for cross-OS evaluation.Excessive licensing prices, limiting its accessibility for smaller organizations.Glorious for understanding superior threats.Could really feel overwhelming for newcomers as a result of its characteristic set.Superior reminiscence forensics and course of simulation.
4. Hybrid Evaluation (CrowdStrike Falcon Sandbox)
Overview:Hybrid Evaluation, now a part of CrowdStrike, is a well-liked cloud-based sandbox device that automates malware evaluation by combining static and dynamic strategies.
It additionally incorporates a crowd-sourced malware intelligence database, permitting analysts to check their outcomes with others and acquire insights into ongoing malware campaigns.
Its automated classification system gives severity scores for samples, making it a superb selection for fast triaging of malicious recordsdata.
Key Options:
Combines behavioral and signature-based evaluation.
Severity scoring for samples primarily based on suspicious actions.
Cloud-based with minimal setup required.
What’s Good?What May Be Higher?Free tier accessible for primary utilization.Restricted customization choices in comparison with different instruments.Glorious for speedy menace triaging.Depends on third-party instruments for superior configurations.Crowd-sourced menace database enhances evaluation.
5. Intezer Analyze
Overview:Intezer Analyze focuses on code reuse evaluation, mapping new malware samples to identified households utilizing binary DNA expertise. By figuring out similarities in reused code, it gives actionable insights into the malware’s ancestry and potential hyperlinks to identified menace teams.
This method makes it notably priceless for uncovering connections between new threats and present assault campaigns.
Key Options:
Identifies code similarities throughout malware households.
Binary DNA expertise for malware classification.
What’s Good?What May Be Higher?Maps malware to identified households utilizing distinctive DNA expertise.Restricted capabilities for real-time behavioral evaluation.Nice for connecting new malware to present campaigns.Quick and environment friendly for polymorphic malware.
6. FireEye Malware Evaluation
Overview:FireEye’s malware evaluation platform is designed for enterprise environments, providing superior capabilities to detect zero-day threats, fileless malware, and superior persistent threats (APTs).
With its integration into the FireEye Menace Intelligence community, organizations can obtain attribution knowledge for assaults, establish menace actors, and monitor assault campaigns.
This makes it a go-to selection for giant organizations that prioritize cybersecurity resilience.
Key Options:
Behavioral and reminiscence evaluation of malware.
Integration with FireEye Menace Intelligence for assault attribution.
Helps in-depth fileless malware evaluation.
What’s Good?What May Be Higher?Tailor-made for giant organizations with superior wants.Costly, making it inaccessible for smaller companies.Glorious at detecting fileless and memory-resident malware.Integrates seamlessly with FireEye’s menace intelligence.
7. Detux (Linux-Centered)
Overview:Detux is an open-source sandbox particularly tailor-made for analyzing Linux-based malware, making it invaluable for organizations targeted on cloud, IoT, or server safety.
As Linux turns into more and more focused by cybercriminals, Detux presents a much-needed resolution for analyzing cryptojackers, rootkits, and different Linux-focused threats in actual time.
Key Options:
Captures file, community, and system-level actions.
Helps Linux ELF binary evaluation.
Modular design for extensibility.
What’s Good?What May Be Higher?Designed particularly for Linux ELF binaries.Restricted to Linux malware evaluation—no cross-platform assist.Light-weight and simple to combine into workflows.Requires experience to arrange and customise successfully.Free and open-source.
8. Cape Sandbox
Overview:Constructed on Cuckoo Sandbox, Cape makes a speciality of capturing, unpacking, and analyzing obfuscated or packed malware, making it a core device for researchers who want to research superior malware like Emotet or TrickBot.
By specializing in payload extraction and de-obfuscation, Cape helps analysts establish the true intent of packed or encrypted malware.
Key Options:
Payload extraction and decryption.
Fileless malware detection.
What’s Good?What May Be Higher?Distinctive for unpacking closely obfuscated malware.Much less intuitive than GUI-based options like ANY.RUN.Helps fileless malware and complicated assault chains.Requires a studying curve for brand spanking new customers.Permits integration with Cuckoo plugins.
9. MalwareBazaar Sandbox
Overview:A part of Abuse.ch’s ecosystem, MalwareBazaar Sandbox is a free cloud-based device designed for analyzing malware submitted to the general public MalwareBazaar platform.
It’s notably helpful for monitoring and understanding the evolution of malware households, making it a favourite amongst menace researchers who wish to sustain with the newest developments in malicious campaigns.
Key Options:
IoC era for brand spanking new malware samples.
Scalable cloud-based infrastructure.
What’s Good?What May Be Higher?Free and user-friendly for researchers.Restricted to analyzing public malware samples.Glorious for monitoring malware campaigns.Much less superior than paid options for in-depth evaluation.Scalable cloud infrastructure.
10. Remnux
Overview:Remnux is a Linux-based toolkit preloaded with a big selection of instruments for malware evaluation and reverse engineering.
It’s extremely efficient for analyzing network-centric threats, comparable to botnets and DDoS malware, and comes with pre-installed instruments like Wireshark for packet evaluation, Radare2 for debugging, and Binwalk for firmware evaluation.
Key Options:
Pre-installed instruments for debugging, reverse engineering, and community forensics.
Light-weight Linux distribution.
What’s Good?What May Be Higher?Free and user-friendly for researchers.Restricted to analyzing public malware samples.Glorious for monitoring malware campaigns.Much less superior than paid options for in-depth evaluation.Scalable cloud infrastructure.
Conclusion
Dynamic malware evaluation instruments empower cybersecurity groups to detect and neutralize superior threats. ANY.RUN leads with interactive, real-time sandboxing best for SOCs and unbiased researchers.
Choices span open-source Cuckoo Sandbox for complete evaluation to Detux for Linux-specific threats. Choose the precise device to strengthen your group’s malware reverse engineering and menace searching capabilities.