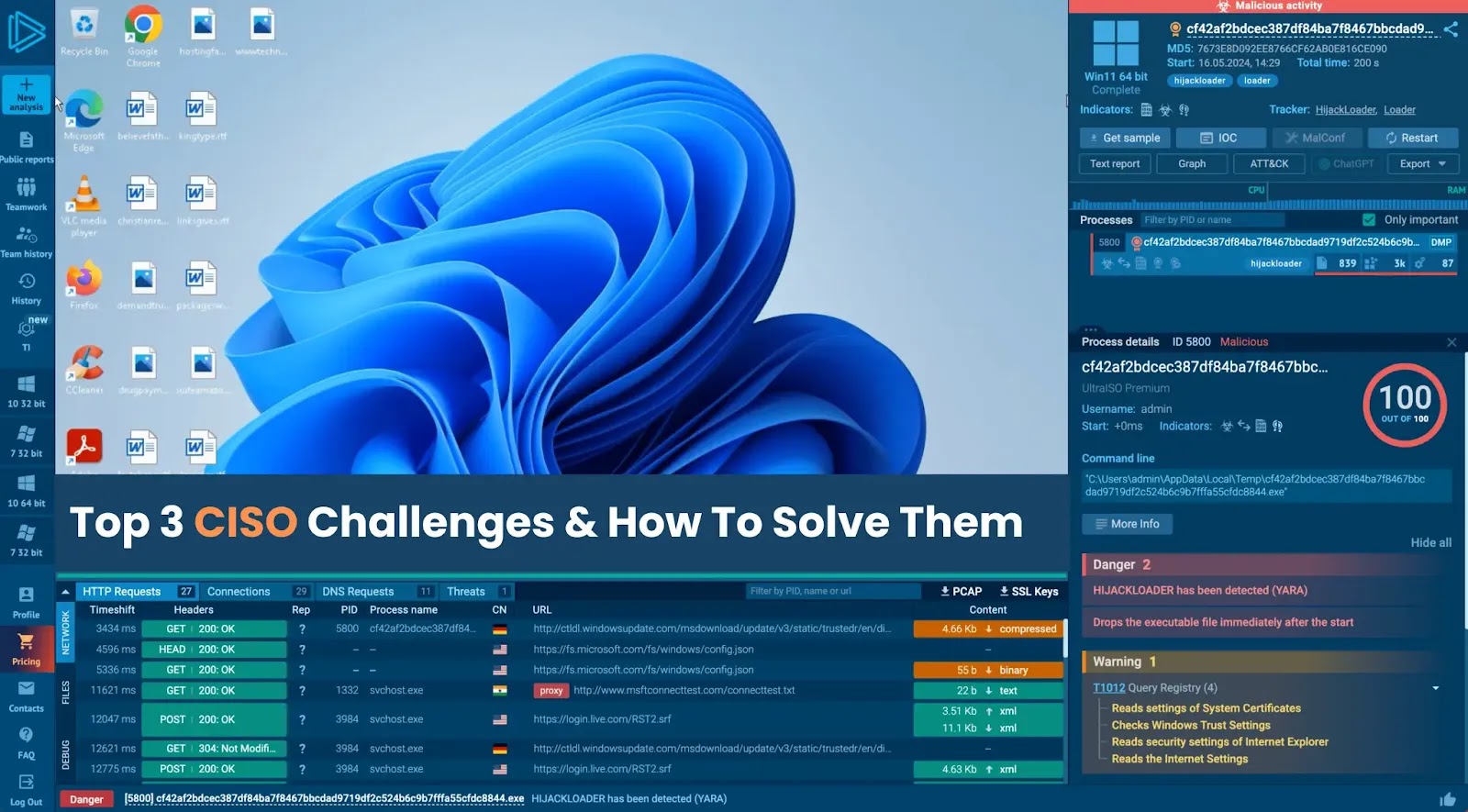
How do you lead a safety workforce when threats evolve sooner than your instruments? It’s a problem many CISOs face every day.
Detection gaps, fixed alert noise, and sluggish incident response make it tougher to guard the group and help the workforce.
The true difficulty usually comes all the way down to visibility. With out seeing how a menace truly behaves, it’s troublesome to prioritize, act rapidly, or reply with confidence.
An interactive sandbox adjustments that. It provides analysts the context they want, watching malware run in actual time, interacting with it, and amassing significant insights.
Listed here are three widespread issues safety leaders take care of and the way a sandbox helps resolve them.
1. Low Detection Fee
Threats don’t stand nonetheless. Attackers continually experiment with new methods, obfuscation strategies, and supply vectors, making it tougher for static or automated instruments to maintain up.
That’s why relying solely on signatures or primary sandboxing usually results in blind spots. To catch trendy threats, you must see how they behave in motion.
A totally interactive surroundings lets analysts step into the malware’s path; opening recordsdata, following redirects, and triggering actions identical to an actual person would.
That stage of engagement reveals conduct that static instruments merely miss.
With ANY.RUN, your workforce can safely detonate and work together with suspicious recordsdata throughout Home windows, Linux, and Android environments, giving them a a lot clearer image of what’s actually occurring.
Instance: Interactive Evaluation of a Phishing Assault
Let’s check out an actual phishing case uncovered utilizing ANY.RUN:
View evaluation session
Phishing e-mail with malicious attachment uncovered inside ANY.RUN sandbox
On this evaluation session, we begin with an e-mail that appears pretty routine; a closing package deal despatched by way of Outlook, containing an HTML attachment.
Open the file, and it launches a webpage with a CAPTCHA immediate.
CAPTCHA immediate with suspicious web site hyperlink displayed inside ANY.RUN
As soon as verified, the sufferer is silently redirected to a pretend Microsoft login web page designed to steal credentials.
Faux Microsoft web page with random URL hyperlink designed to steal credentials
As ANY.RUN runs in a totally interactive surroundings, we are able to comply with your complete chain, from the preliminary e-mail to the credential harvesting web site, in actual time.
The sandbox flags the conduct as malicious, highlights the phishing indicators, and gives full visibility into processes, connections, and URLs concerned.
It’s the sort of assault that would simply slip previous static instruments. However right here, it’s uncovered in a matter of seconds.
Enhance detection, scale back alert fatigue, and speed up response; all with an interactive sandbox constructed for safety groups -> Attempt ANY.RUN Now
2. Alert Fatigue
Safety groups are overwhelmed not as a result of they lack alerts, however as a result of they get too many.
Sifting by way of infinite notifications to seek out the actual threats slows everybody down and will increase the possibility of lacking one thing vital.
ANY.RUN helps scale back alert fatigue by exhibiting outcomes as they occur.
Analysts don’t have to attend for the session to finish; the sandbox highlights malicious exercise in actual time, flags vital behaviors, and provides visible cues that make evaluation sooner and simpler, even for junior workforce members.
On prime of that, Automated Interactivity supplied by ANY.RUN takes it additional. It simulates person conduct contained in the sandbox, mechanically clicking by way of prompts and launching recordsdata, which implies sooner verdicts and fewer guide work.
Instance: Automated Detection of Remcos by way of ANY.RUN Sandbox
Let’s check out how ANY.RUN helps lower by way of alert fatigue by surfacing ends in actual time, with none guide steps:
View evaluation session
Remcos payload hidden in a pretend archive mechanically unpacked and detonated
On this case, we’re coping with a suspicious RAR archive named po-292893928.PDF.rar. Inside is a JavaScript file that launches as soon as the archive is extracted.
ANY.RUN’s Automated Interactivity takes over, simulating person conduct and triggering the execution path mechanically.
Automated Detection of Remcos RAT in 30 seconds inside ANY.RUN sandbox
Because the file runs, the sandbox detects Remcos RAT exercise nearly immediately. It extracts the configuration file and divulges the command-and-control (C2) IPs, all inside simply 30 seconds of beginning the session.
Malware configurations and C2 extracted inside interactive sandbox
Because of the real-time evaluation and automatic interplay, the session highlights each malicious step clearly, lowering time to verdict and serving to cybersecurity professionals keep away from drowning in noise.
It’s a sensible option to scale back alert fatigue and provides even junior analysts the readability they should act with confidence.
3. Sluggish Response
When your workforce doesn’t have the complete image, even small incidents can flip into larger issues.
Delays in understanding what a menace is doing, the place it’s connecting, or the way it entered the system decelerate containment and go away room for injury.
Speeding a response with out realizing what you’re coping with can result in incomplete remediation, missed persistence mechanisms, and even reinfection.
ANY.RUN helps safety groups scale back investigation time and reply with higher confidence by reworking uncooked conduct into clear, actionable perception.
Instance: Full Breakdown of a Formbook An infection
Let’s see how ANY.RUN helps safety groups go from preliminary alert to full understanding in just some clicks.
View evaluation session
Formbook stealer an infection uncovered with full behavioral chain and mapped methods
On this session, a suspicious executable is launched.
The sandbox exhibits your complete execution tree; a transparent, visible course of graph that helps analysts hint how the malware strikes by way of the system, spawns processes, and maintains persistence.
Course of graph reveals execution path and persistence mechanisms
Subsequent, the assault is mapped to the MITRE ATT&CK framework, exhibiting the precise TTPs used, together with scheduled duties for persistence, credential entry, and evasion methods.
This helps groups perceive not simply what occurred, however how the attacker operated.
Mapped TTPs supply deeper perception into attacker conduct and methods
Lastly, all IOCs, together with domains, IPs, file hashes, and URLs, are mechanically extracted and introduced in a single place. No want to change tabs, search logs, or dig for knowledge; it’s all able to export and share.
IOC panel makes menace sharing and triage sooner and extra organized
In a brief period of time, your workforce will get the whole lot wanted for deeper evaluation, reporting, and a assured response, with out losing time leaping between instruments.
Why An Interactive Sandbox Ought to Be Half Of Each CISO’s Technique
Fashionable threats demand greater than passive detection and guesswork. To remain forward, safety groups want instruments that supply readability, context, and pace, with out including extra noise.
That’s precisely what an interactive sandbox brings to the desk.
With ANY.RUN, you’re enabling your workforce to behave on it with precision.
Right here’s how ANY.RUN helps CISOs overcome their prime challenges:
Enhance detection by revealing conduct missed by static or automated instruments
Minimize by way of noise with real-time evaluation and visible menace indicators
Speed up response with full course of graphs, TTPs, and IOC extraction
Empower junior analysts with intuitive workflows and automatic interactivity
Cut back threat by enabling sooner, extra correct decision-making throughout the SOC
Whether or not you’re constructing detection guidelines, updating playbooks, or investigating vital incidents, the sandbox provides you the visibility you must lead with confidence.
Attempt ANY.RUN for 14 days and see the way it transforms your workforce’s detection and response.