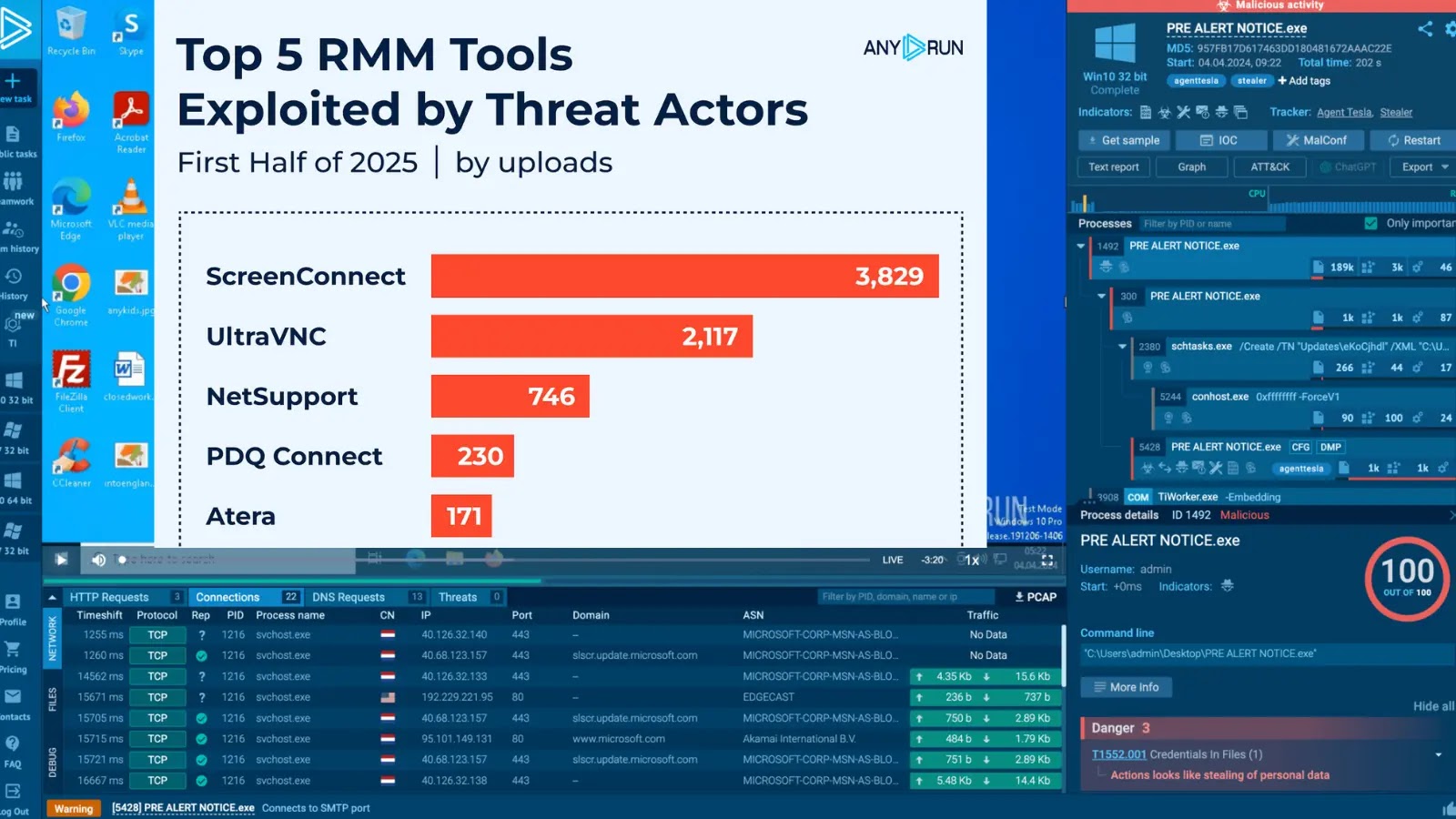
Distant monitoring and administration (RMM) instruments are a go-to for IT groups, however that very same energy makes them a favourite trick up attackers’ sleeves, too.
Within the first half of 2025, ANY.RUN analysts reviewed 1000’s of real-world malware detonations within the interactive sandbox and noticed a transparent development: 5 instruments have been concerned in most RMM-related intrusions.
Let’s take a more in-depth take a look at the 5 RMM instruments mostly exploited by attackers, and the way your group can spot this exercise sooner, earlier than it turns into one thing extra severe.
In the event you work in a SOC or deal with incident response, that is the form of sample value being attentive to.
Snapshot of the Knowledge
This breakdown displays the frequency of every RMM instrument noticed throughout suspicious and malicious sandbox classes within the first half of 2025.
The numbers are drawn from ANY.RUN’s inner tagging system, which tracks instrument utilization patterns in actual time.
It’s a fast technique to see which platforms stood out in attacker exercise and the way usually they appeared in precise malware investigations.
1. ScreenConnect: 3,829 Sandbox Periods
ScreenConnect (now branded as ConnectWise Management) is a reliable distant assist and desktop entry instrument utilized by IT groups and MSPs.
Sadly, its highly effective distant management options additionally make it a straightforward selection for menace actors seeking to silently entry and handle compromised machines.
Within the following sandbox session, we will clearly see how ScreenConnect is utilized in a phishing marketing campaign that mimics a Zoom assembly hyperlink:
View sandbox session
Evaluation session with the exploitation of ScreenConnect
The quickest technique to catch threats like that is by interactive sandboxes like ANY.RUN.
Within the top-right panel of the session, the platform instantly flags the exercise as Malicious, assigning clear behavioral tags corresponding to “screenconnect”, “rmm-tool”, and “distant”.
Quick verdict of malicious exercise displayed inside ANY.RUN sandbox with related labels
The method tree highlights the malicious executable (ScreenConnect.WindowsClient.exe) and supplies wealthy context just like the command line, YARA detections, and extra, saving your time and guesswork.
Reduce investigation time, scale back alert fatigue, and catch hidden threats sooner with ANY.RUN’s interactive sandbox -> Strive ANY.RUN now
Relatively than digging by logs or counting on static detection, this real-time visibility helps groups spot abuse early, even when attackers use reliable instruments.
Particulars of malicious course of
2. UltraVNC: 2,117 Sandbox Periods
UltraVNC is an open-source distant desktop instrument usually utilized by IT assist groups to view and management one other pc over a community. It’s light-weight, free, and simple to configure.
Within the sandbox session under, UltraVNC is used as a part of an Agent Tesla marketing campaign.
View sandbox session
Use of UltraVNC in an assault with Agent Tesla
ANY.RUN’s interactive sandbox flags the conduct immediately, labeling the session as Malicious and tagging it with “ultravnc”, “rmm-tool”, and “stealer”.
The method tree reveals how RegAsm.exe launches with suspicious conduct and is tied to Agent Tesla exercise, together with credential theft.
With real-time detection, detailed indicators, and visualized execution stream, ANY.RUN helps analysts shortly join the dots, with out having to reverse engineer each step manually.
3. NetSupport: 746 Sandbox Periods
NetSupport Supervisor is a reliable distant entry instrument usually utilized in company and academic settings. However when deployed from uncommon places and with out consumer consent, it’s a crimson flag.
Attackers generally use it as a stealthy Distant Entry Trojan (RAT) because of its built-in capabilities for display screen viewing, file switch, and command execution.
Within the sandbox session under, the assault begins with a textual content file containing obfuscated PowerShell code, which triggers the execution of client32.exe; a NetSupport binary dropped into the consumer’s roaming profile:
View sandbox session
NetSupport exploitation detected inside ANY.RUN’s interactive sandbox
The method tree reveals client32.exe operating from: C:UsersadminAppDataRoamingbDabSkclient32.exe. This can be a typical location utilized by malware to keep away from detection.
Malicious course of with its particulars displayed inside ANY.RUN sandbox
Beneath, within the HTTP request part, we will see a connection to the suspicious area geo.netsupportsoftware.com, confirming the usage of NetSupport for command-and-control.
Mixed with POST visitors to a pretend C2 server, this conduct helps analysts join the dots shortly and confidently.
HTTP request part confirming the usage of NetSupport
4. PDQ Join: 230 Sandbox Periods
PDQ Join is a cloud-based system administration instrument that enables IT groups to deploy software program, run scripts, and handle endpoints remotely, while not having area entry.
It’s a goal for abuse in phishing and preliminary entry campaigns.
Within the sandbox session under, the assault begins with a pretend authorities verification web page; a phishing website trying to lure the sufferer into downloading a malicious payload:
View sandbox session
Phishing assault with the exploitation of PDQ Join
Shortly after the phishing web page masses, we see a suspicious connection from pdq-connect-agent.exe to a distant IP tackle (162.159.141.50) over port 443, as proven within the community stream.
The executable seems alongside a companion updater course of, pdq-connect-updater.exe, hinting at a stealthy set up and command channel.
Particulars of malicious connections analyzed inside ANY.RUN sandbox
This type of setup can simply fly below the radar in static or rule-based methods.
However ANY.RUN’s interactive sandbox reveals it in seconds, highlighting the precise course of that makes the outbound request and giving analysts the complete image of what’s taking place, from the pretend CAPTCHA to the stay community exercise.
5. Atera: 171 Sandbox Periods
Atera is a distant monitoring and administration (RMM) platform designed for IT professionals to remotely handle methods, automate upkeep, and monitor efficiency.
Like different reliable instruments, it may be quietly put in and misused by attackers for persistence and management, usually with out triggering alarms.
Within the sandbox session under, the file AteraAgent.exe runs from its default listing however triggers a number of warnings associated to system service execution, file overwrites, and suspicious course of conduct:
View sandbox session
ANY.RUN’s detection engine assigns a Malicious verdict.
The method drops or overwrites executable content material and begins SC.EXE to register itself as a Home windows service; frequent conduct in stealthy persistence setups.
Agent Atera course of with related TTPS
Beneath within the Risk Particulars tab, we additionally see an outbound connection to agent-api.atera.com, flagged as a Potential Company Privateness Violation.
This detection (by way of Suricata IDS) confirms that the Atera agent is actively speaking with distant infrastructure, whether or not the consumer is aware of it or not.
Communication with the distant entry software program
With this degree of visibility, groups can shortly spot when a trusted utility crosses the road into unauthorized use and take motion earlier than deeper compromise happens.
Detect Abuse Early And Reply With Confidence
RMM instruments aren’t going away however with the precise visibility your group doesn’t need to be caught off guard once they’re used in opposition to you.
ANY.RUN helps safety groups catch misuse sooner, examine smarter, and make higher choices with context-rich, real-time evaluation.
From prompt verdicts and detailed behavioral tags to community forensics and assault mapping, ANY.RUN provides analysts the options they should keep forward, with out digging by logs or relying solely on static detections.
Whether or not you’re working in a SOC, operating menace hunts, or investigating incidents, it’s constructed for pace, readability, collaboration, and belief.
Begin your 14-day trial of ANY.RUN right this moment and see how a lot sooner your group can catch threats hiding in plain sight.