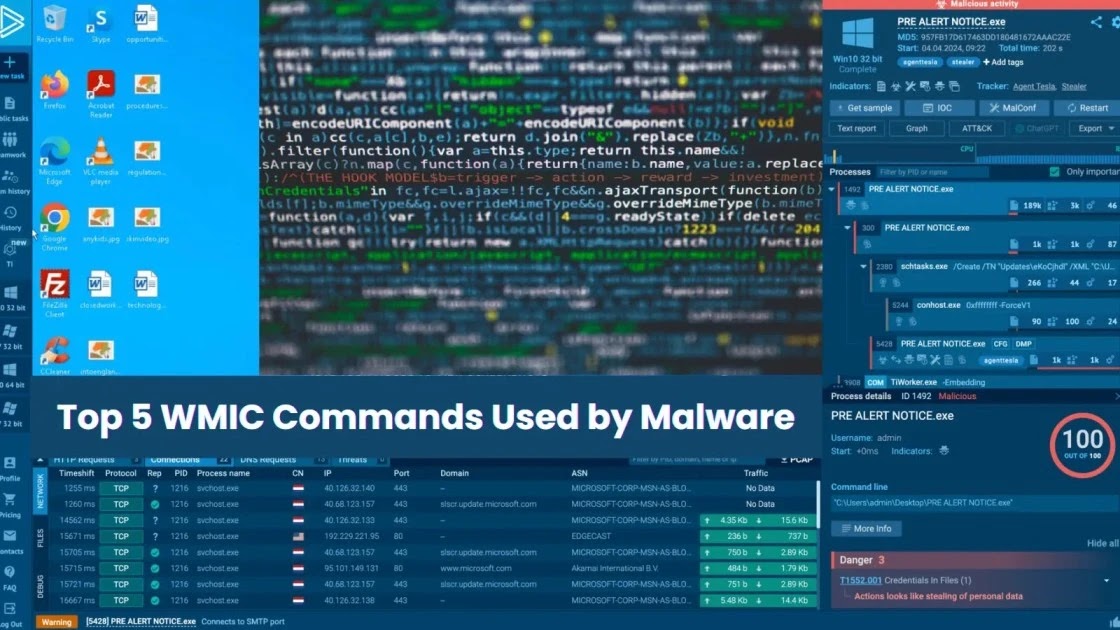
Malware doesn’t want fancy instruments to be harmful. Typically, all it takes is WMIC, a quiet, native utility that’s nonetheless doing harm.
Previously weeks, we’ve seen a constant sample in some ANY.RUN sandbox periods: malware retains reaching for WMIC to do its soiled work.
Let’s take a more in-depth take a look at 5 WMIC command classes that cybercriminals nonetheless depend on at the moment, and why they matter for defenders.
For those who’re monitoring threats, investigating suspicious conduct, or simply wish to perceive how malware operates from the within out, that is the place you begin.
What Is WMIC?
WMIC (Home windows Administration Instrumentation Command-line) is a built-in Home windows software that lets customers and attackers work together with system elements. It could question {hardware} data, modify settings, uninstall packages, and extra.
It was initially designed for directors, however attackers find it irresistible as a result of:
It’s pre-installed on most Home windows techniques
It doesn’t set off rapid alarms
It may be scripted simply in malware payloads
Let’s break down the WMIC instructions mostly seen in malware samples.
1. System Profiling: How Malware “Scans the Room” First
Earlier than malware makes its subsequent transfer, it often takes a second to grasp the place it’s landed. Is it working on an actual machine or a digital one? What’s the working system? What {hardware} is current?
This stage known as system profiling, and attackers use it to:
Keep away from detection (like sandboxes or evaluation instruments)
Tailor assaults primarily based on the system setup
Guarantee persistence solely on invaluable or exploitable machines
One of many best methods to collect this info is utilizing the WMIC command-line software constructed into Home windows.
Attackers run instructions like:
wmic os get locale: This tells them the system’s language and area settings (e.g., en-US, ru-RU, and so on.). Some malware avoids executing in sure areas to remain underneath the radar.
wmic csproduct get uuid: Grabs a novel {hardware} ID that helps detect if the malware is working in a digital machine (a typical evaluation setting).
wmic os get Caption: Returns the OS model (e.g., Home windows 10 Professional), which helps resolve if the system is a viable goal
These instructions may appear small, however they’re a serious clue throughout early an infection. In reality, in a current ANY.RUN sandbox session, we noticed the Trox malware use wmic csproduct get uuid proper after launch.
Check out the Trox session right here.
Within the Course of Tree, you’ll discover WMIC.exe being executed. The precise command used right here is wmic csproduct get uuid:
wmic csproduct get uuid command detected by ANY.RUN sandbox
Contained in the sandbox, we additionally see the warnings triggered underneath two MITRE ATT&CK methods:
T1047 – Home windows Administration Instrumentation
T1082 – System Data Discovery
ANY.RUN flags these behaviors in actual time, letting analysts rapidly see that this pattern is probing the setting, usually an indication that malware is attempting to keep away from sandboxes or tailor its conduct.
See each command, perceive attacker conduct in actual time, and cease threats earlier than they unfold -> Attempt ANY.RUN now
System profiling is often the first step in an assault. For those who catch it early, you’ll be able to cease malware earlier than it begins exfiltrating information, encrypting information, or digging deeper into the community.
Instruments like WMIC may be previous, however they’re nonetheless extremely helpful for each sysadmins and risk actors. With ANY.RUN, recognizing these behaviors is straightforward and on the spot.
2. KMS Activation & System Information Assortment: When Malware Masquerades As Software program Installers
On this case, malware behaves like a software program activator. Consider instruments that activate Microsoft merchandise with out a legitimate license, these are sometimes abused by malware to both:
Seem respectable by mimicking regular activation conduct
Or, extra importantly, to question licensing and system data underneath the radar
This trick is usually seen in malware hidden inside third-party activators or cracked software program installers. They could really carry out activation-related features, however they usually do way more behind the scenes.
A typical command appears like:
wmic path SoftwareLicensingService name InstallProductKey
This installs a product key on the system, often a routine motion. However within the palms of malware, it might probably serve a number of stealthy functions:
Mix in with respectable software program: The exercise mimics what customers would possibly count on from a cracked program or a third-party activator.
Take a look at system privileges: Working this command reveals whether or not the malware has the permissions it wants (like admin rights).
Harvest licensing information: The response can assist fingerprint the system or determine if the machine has been contaminated earlier than.
You might also see:
wmic name RefreshLicenseStatus
This command triggers a license test on the system, one other conduct that may both reinforce the disguise or quietly acquire standing information.
In a current ANY.RUN sandbox session, we noticed a number of WMIC.exe processes tied to activation-related instructions, clearly not a part of any regular system workflow.
Check out this activity log:
A number of WMIC instructions being executed
On this sandbox evaluation session, you’ll discover:
Repeated use of the SoftwareLicensingProduct and SoftwareLicensingService paths
Calls to each InstallProductKey and RefreshLicenseStatus
A hardcoded ApplicationID, reused throughout a number of instructions, suggesting automation
Within the course of timeline, these instructions are scattered throughout brief intervals, pointing to a scripted or stealthy try and simulate activation conduct.
3. AV Evasion: Hiding In Plain Sight
Some malware doesn’t attempt to disable antivirus software program, it simply steps round it. One of many best methods to do this is including itself to the record of information that received’t be scanned.
This tactic is called AV evasion, and it’s surprisingly efficient. Malware doesn’t have to kill the antivirus course of or tamper with system information.
As an alternative, it quietly tells Home windows Defender to disregard sure folders or paths, permitting the malicious information to run freely.
Right here’s the WMIC command used for this conduct:
wmic /Namespace:rootMicrosoftWindowsDefender class MSFT_MpPreference name Add ExclusionPath=”C:”
This command tells Home windows Defender to exclude your complete C: drive from scans.
Sure, the entire system is now off-limits for real-time safety.
Attackers might goal particular folders too, like:
Add ExclusionPath=”C:UsersPublic”
This may make detection practically unimaginable until different defenses are in place.
On this sandbox session with AsyncRat, we noticed this precise command used early within the execution chain.
View sandbox session with AsyncRat
WMIC command detected by ANY.RUN sandbox
Right here’s what stands out within the ANY.RUN evaluation:
Command line uncovered by ANY.RUN sandbox
WMIC.exe is executed with a protracted namespace path to Microsoft Defender
The command provides C: as an exclusion path
No alerts are triggered by the system however ANY.RUN sandbox catches the conduct.
You too can see that the command is linked to MITRE approach T1012 – Question Registry, because it interacts with Defender’s settings underneath the hood.
Command line linked to T1012 – Question Registry
This tactic doesn’t contain malware rewriting system information or crashing antivirus, it merely asks Defender to not look, and Defender obeys.
It’s refined. It’s quiet. And with out behavioral evaluation, it’s straightforward to overlook. However in ANY.RUN’s sandbox, this transfer will get picked up immediately:
The command line exhibits the precise exclusion added
The method tree maps the place and when it occurred
You may tie it to recognized malware behaviors like AsyncRat and hyperlink it to the attacker’s broader intent
4. Shadow Copy Deletion: Burning The Restoration Bridge
As soon as malware has encrypted your information or taken management of your system, it doesn’t need you undoing the harm. That’s the place shadow copy deletion is used.
Shadow copies are computerized backups created by Home windows. They’re usually your final likelihood to revive information after a ransomware assault. So, naturally, attackers wipe them out first.
Some generally seen instructions for this function are:
wmic bcdedit /set {default} recoveryenabled no: This disables the Home windows restoration setting totally, stopping the system from launching restoration instruments throughout startup.
vssadmin delete shadows /all /quiet: Silently deletes all present shadow copies.
wmic shadowcopy delete: One other methodology to take away earlier restore factors that customers may use to roll again encrypted information.
By combining these, attackers be certain that the sufferer can’t get well information with out paying.
On this ANY.RUN sandbox session, the malware (recognized as Chaos) ran a the command wmic shadowcopy delete to dam restoration.
wmic shadowcopy delete command detected by ANY.RUN sandbox
Right here’s what you’ll see contained in the sandbox:
WMIC.exe executes the command to disable the restoration setting
The Course of Tree clearly exhibits the execution order
The conduct aligns with ransomware techniques, eradicating the consumer’s potential to get well information with out backups
By deleting shadow copies and disabling restoration instruments, attackers improve the strain on victims to pay the ransom.
These are harmful however refined modifications that don’t all the time set off alarms, particularly when carried out utilizing built-in instruments like WMIC.
5. Uninstall / Persistence Removing: Chopping Off The Traces
Not all malware desires to stay round ceaselessly. In some circumstances, attackers intentionally clear up after themselves, particularly when their purpose is a fast hit: run a payload, exfiltrate some information, and disappear with out a hint.
Different instances, they use WMIC to terminate rival processes, disable competing malware, or kill safety instruments. That is a part of what’s generally known as persistence elimination or post-exploitation cleanup.
Right here’s a few of the most simple WMIC instructions used for this:
wmic course of name terminate
This command makes an attempt to terminate a working course of, any course of it has permission to kill. Malware would possibly use this to:
Shut down safety monitoring instruments
Disable different malware or competing software program
Kill its personal processes after finishing a activity
Attackers usually pair this with a filter to focus on particular executables. For instance:
wmic course of the place “identify=’svchost.exe’” name terminate
As an example, on this sandbox session, malware used WMIC to situation a termination command concentrating on a suspicious file positioned within the Public listing.
Check out the detection: View evaluation session
Course of termination command in ANY.RUN sandbox
The method path consists of C:UsersPublicProgram Filessvchost.exe, which isn’t a respectable location for svchost.exe
The command was executed through WMIC.exe, utilizing a course of filter
ANY.RUN flagged this with a warning: “Probably accesses (executes) a file from the Public listing”
This can be a sturdy signal that the malware both launched a payload from an uncommon location and is now terminating it to cowl its tracks, or is concentrating on a competing course of or software working from that very same path.
Why Catching WMIC Exercise Early Can Save You from Greater Injury
If there’s one factor these 5 command classes reveal, it’s this: WMIC remains to be a go-to software for malware, and it’s usually used within the earliest phases of an assault.
From system profiling and antivirus evasion to deleting backups and terminating processes, these WMIC instructions might look small on their very own however collectively, they type a blueprint for a way attackers:
Keep hidden
Disable defenses
Lock down techniques
And make restoration practically unimaginable
That’s why real-time visibility into WMIC exercise is essential.
How ANY.RUN Helps You Keep Forward of WMIC-Primarily based Threats
ANY.RUN’s interactive sandbox makes it straightforward to detect and perceive how malware makes use of WMIC. Right here’s the way it works in your favor:
See each WMIC command executed: Full command-line visibility, together with arguments and execution time.
Catch stealthy behaviors immediately: From Defender exclusions to shadow copy deletions, ANY.RUN flags actions that AV instruments usually miss.
Visualize course of relationships: The method tree exhibits precisely when and the place WMIC known as and what it triggers subsequent.
Map to MITRE ATT&CK: Behaviors are robotically linked to ATT&CK methods like T1082 (System Information Discovery) and T1490 (Inhibit System Restoration).
Collaborate quicker: Share reside periods, generate reviews, and coordinate along with your staff in actual time.
Cut back investigation time: See conduct unfold reside as an alternative of digging via logs post-infection.
Whether or not you’re a part of a blue staff, risk intel group, or an incident response staff, ANY.RUN helps you progress from “What occurred?” to “Right here’s precisely what the malware did” in minutes, as an alternative of hours.
Don’t Let Silent Instructions Flip Into Full-Blown Incidents
Constructed-in instruments like WMIC may appear innocent however within the mistaken palms, they’re the quiet begin of one thing a lot worse.
With real-time visibility into command-line exercise, course of conduct, and post-exploitation techniques, you’ll be able to catch these threats earlier than they turn out to be ransomware occasions or full system compromises.
Begin your 14-day trial of ANY.RUN and see precisely how malicious processes unfold reside, in an interactive sandbox.