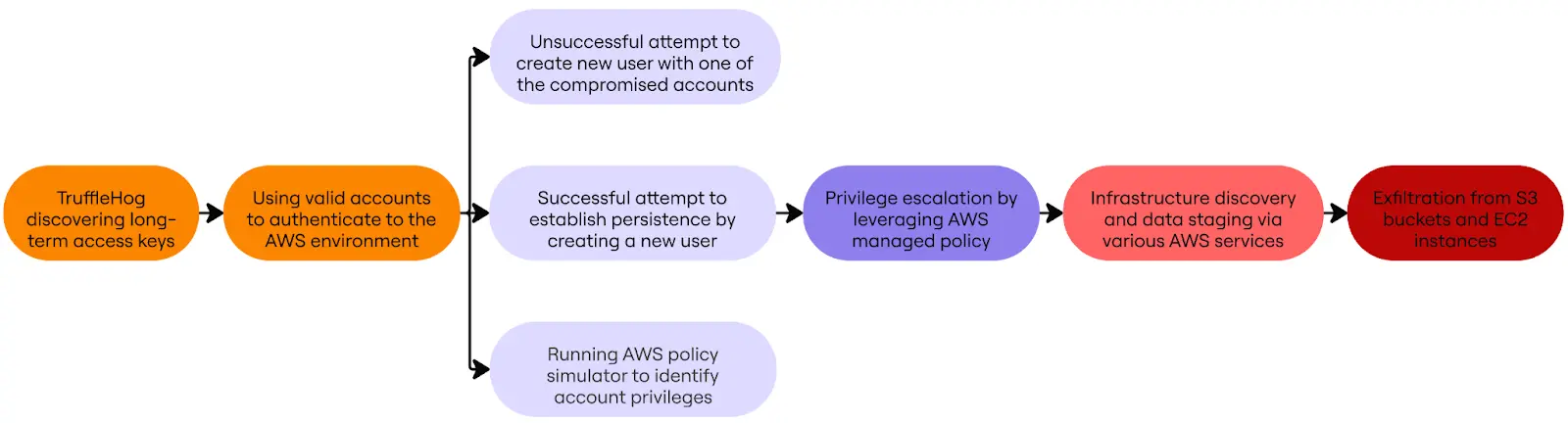
A crucial zero-day distant code execution (RCE) vulnerability, recognized as CVE-2025-9961, has been found in TP-Hyperlink routers.
Safety analysis agency ByteRay has launched a proof-of-concept (PoC) exploit, demonstrating how attackers can bypass Tackle House Format Randomization (ASLR) protections to realize full management over affected units.
The vulnerability resides within the router’s Buyer Premises Gear (CPE) WAN Administration Protocol (CWMP) binary, a element of the TR-069 protocol utilized by service suppliers for distant machine administration.
Technical Breakdown of the Exploit
The core of the vulnerability is a stack-based buffer overflow throughout the cwmp course of. Researchers at ByteRay discovered that by sending a malicious request, they might overwrite this system counter (PC) and seize management of the execution circulate.
Nonetheless, the presence of ASLR, a safety characteristic that randomizes the reminiscence addresses of key information areas, offered a major hurdle.
Because the exploit didn’t contain an info leak to reveal reminiscence layouts, the researchers devised a brute-force technique. They repeatedly guessed the bottom deal with of the usual C library (libc) to find the system() operate.
Assault Situation
An incorrect guess would crash the cwmp service, however the researchers famous that an attacker with entry to the TP-Hyperlink net panel may merely restart the service, making the brute-force assault sensible.
The assault workflow requires the router to be configured to simply accept the attacker’s customized Auto Configuration Server (ACS). The exploit is delivered by a SetParameterValues request containing the payload.
The ultimate payload makes use of a return-to-libc (ret2libc) approach to name the system() operate with a command argument.
This command instructs the router to obtain and execute a malicious binary (e.g., a reverse shell) from an attacker-controlled server, granting the attacker full distant entry.
Discovery and PoC Launch
The ByteRay analysis workforce made the invention. Throughout their evaluation, they encountered an issue the place the usual GenieACS platform corrupted the binary payload, stopping profitable exploitation. This pressured them to develop a customized ACS emulator able to faithfully transmitting the exploit code.
The workforce has printed an in depth technical write-up and the complete exploit code on GitHub. They state the discharge is meant for instructional functions and safety analysis, permitting directors to check their very own units. Unauthorized use of different methods is against the law.
PoC Exploit
This vulnerability is crucial, as profitable exploitation permits for full distant code execution on the router. This might allow an attacker to intercept visitors, launch additional assaults on the native community, or enlist the machine in a botnet.
The analysis underscores the safety dangers related to network-facing administration protocols like TR-069, the place even minor parsing errors can escalate into extreme threats.
The exploit highlights that safety mitigations like ASLR can generally be bypassed with inventive assault methods.
Customers of TP-Hyperlink routers are suggested to watch for firmware updates from the seller and apply them as quickly as they turn out to be obtainable to patch this vulnerability.
Discover this Story Attention-grabbing! Observe us on Google Information, LinkedIn, and X to Get Extra Instantaneous Updates.