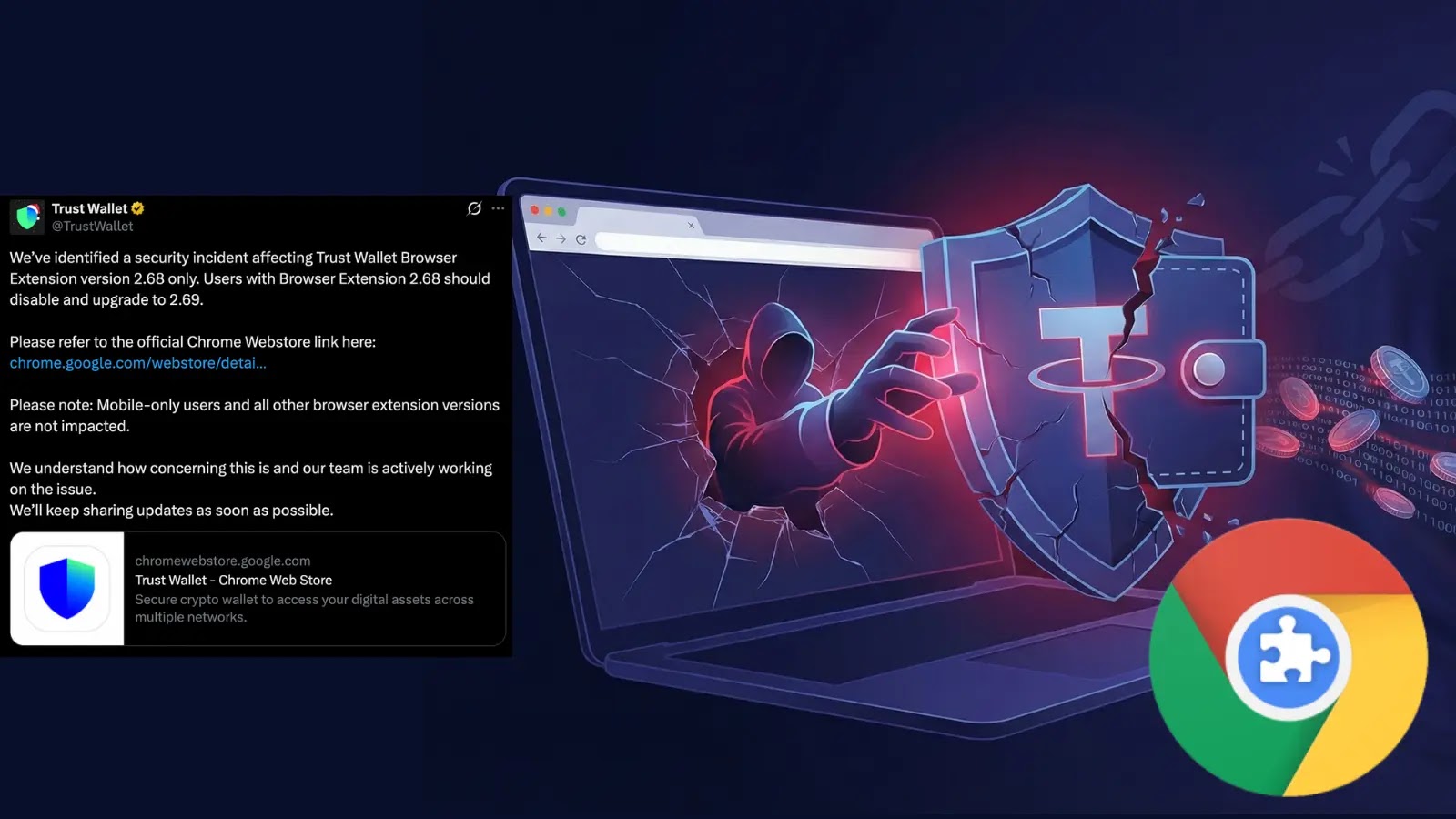
Many Belief Pockets customers noticed their wallets drained of over $7 million after a safety breach within the Chrome browser extension model 2.68.0, launched on December 24, 2025.
Blockchain investigator ZachXBT first flagged the incident on X, noting a surge in unauthorized outflows from affected addresses shortly after customers interacted with the extension.
Studies emerged on Christmas Eve, with victims sharing screenshots of emptied portfolios, together with vital holdings in ETH, BTC, SOL, and BNB.
One person claimed a $300,000 loss in minutes after easy authorization, with transactions funneled to a number of attacker-controlled addresses. PeckShield estimated preliminary losses at $6 million; Belief Pockets later confirmed roughly $7 million throughout a whole lot of wallets.
The assault coincided with the Chrome Net Retailer extension replace, affecting desktop customers however sparing the cell app. Safety agency SlowMist issued an alert, describing a possible supply-chain compromise during which malicious code was injected upstream.
Malicious Code Uncovered
Researchers examined a compromised bundle and located a JavaScript file named 4482.js that was masquerading as PostHog analytics. The obfuscated script activated on seed phrase import, silently exfiltrating delicate pockets knowledge, together with restoration phrases, to api.metrics-trustwallet.com, a website registered days earlier and mimicking official branding.
So right here’s what’s taking place :Within the Belief Pockets browser extension code 4482.jsa latest replace added hidden code that silently sends pockets knowledge outsideIt pretends to be analytics, nevertheless it tracks pockets exercise and triggers when a seed phrase is importedThe knowledge was despatched to… pic.twitter.com/8kkMUkDYql— Akinator | Testnet Arc (@0xakinator) December 25, 2025
Public WHOIS information confirmed its novelty, with no ties to reliable Belief Pockets infrastructure.
Attacker sophistication prolonged to parallel phishing: domains like fix-trustwallet.com lured panicked customers with faux “vulnerability fixes,” prompting seed phrase entry for fast drains. The shared registrar throughout phishing websites suggests coordinated operations.
Belief Pockets acknowledged the breach on December 25 through X, remoted it to model 2.68.0, and urged speedy disablement. Customers should navigate to chrome://extensions/?id=egjidjbpglichdcondbcbdnbeeppgdph, toggle off, allow developer mode, and replace to v2.69, the only real protected iteration.
We’ve recognized a safety incident affecting Belief Pockets Browser Extension model 2.68 solely. Customers with Browser Extension 2.68 ought to disable and improve to 2.69.Please confer with the official Chrome Webstore hyperlink right here: observe: Cellular-only customers…— Belief Pockets (@TrustWallet) December 25, 2025
The crew pledged full refunds to affected customers, prioritized assist outreach, and warned towards unofficial DMs. Binance co-founder Changpeng Zhao hinted at doable insider involvement, amplifying scrutiny on the acquisition-owned pockets.
This breach underscores supply-chain perils in crypto extensions, the place auto-updates bypass person scrutiny. Affected chains span EVM, Bitcoin, and Solana, with stolen funds laundered through mixers.
Cybersecurity specialists suggest utilizing new wallets for probably uncovered seeds and verifying updates vigilantly. As investigations proceed, Belief Pockets’s refund course of will take a look at person belief amid 2025’s $3 billion in hacking losses.
Observe us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to characteristic your tales.