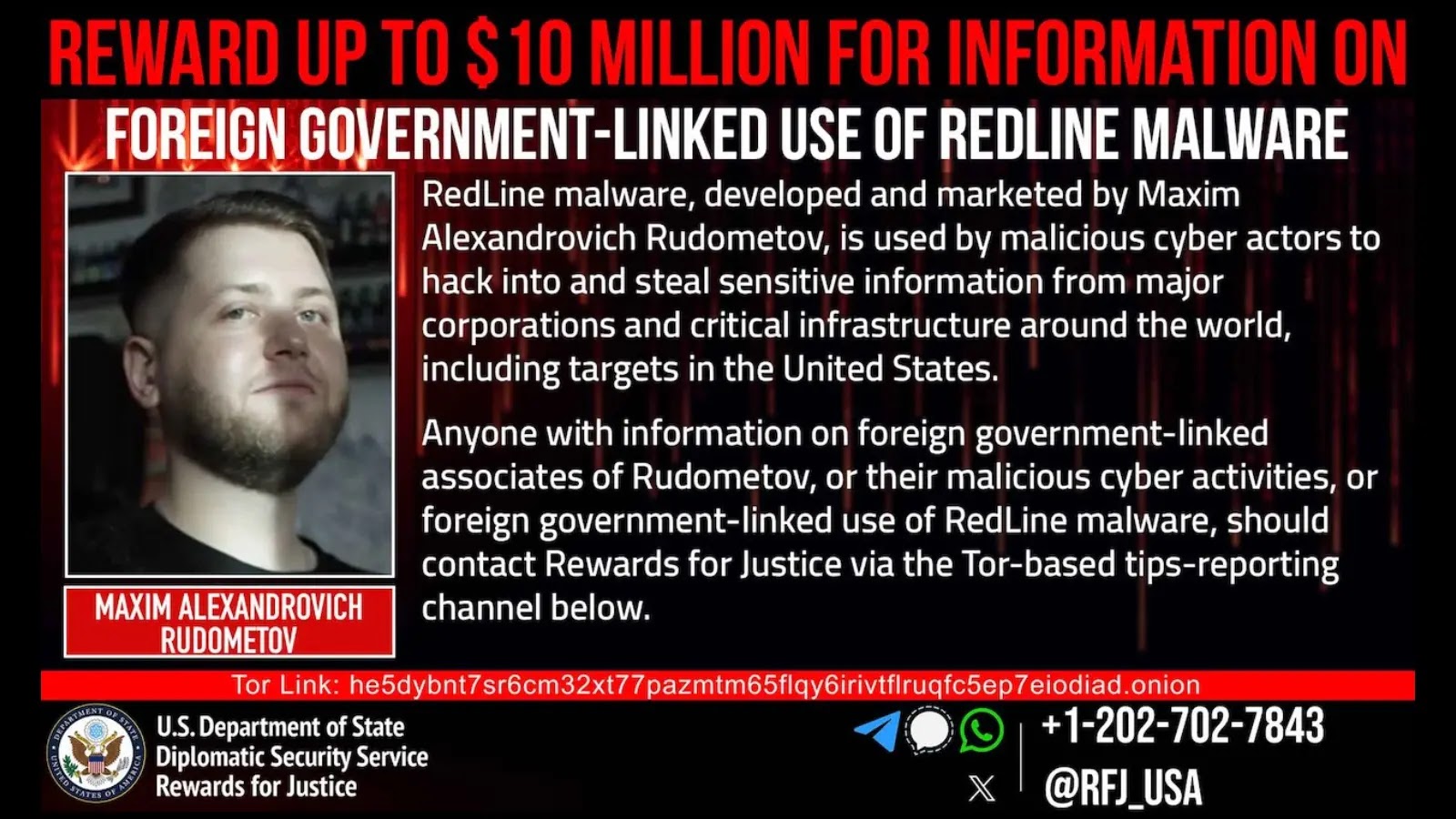
The USA Division of State’s Rewards for Justice program has introduced a considerable bounty of as much as $10 million for data resulting in the identification or location of people concerned in malicious cyber actions towards U.S. essential infrastructure.
The reward particularly targets these appearing below overseas authorities course who violate the Laptop Fraud and Abuse Act (CFAA), with explicit concentrate on Maxim Alexandrovich Rudometov, the developer behind the infamous RedLine data stealer malware.
Ukrainian Developer Behind International Cyber Menace
Maxim Alexandrovich Rudometov (Максим Александрович Рудомётов), born in 1999 in Ukraine’s Luhansk area, stands accused of growing and distributing the RedLine malware, one of many world’s most prevalent information-stealing applications.
Working below a number of on-line aliases together with “dendimirror,” “alinchok,” “ghackihg,” “makc1901,” “navi_ghacking,” and “bloodzz.fenix,” Rudometov has established himself as a key determine within the world cybercrime ecosystem.
The 26-year-old developer fled to Krasnodar, Russia, in February 2022 following Russia’s invasion of Ukraine.
U.S. authorities point out that Rudometov maintains energetic management over RedLine’s technical infrastructure and possesses cryptocurrency accounts used for receiving and laundering funds from malware operations.
His continued involvement in managing the malware’s backend programs demonstrates the continuing menace posed by his prison enterprise.
RedLine capabilities as a sophisticated infostealer designed to extract delicate information from compromised programs, together with usernames, passwords, monetary data, system configurations, browser cookies, and cryptocurrency pockets credentials.
The malware harvests this stolen information, collectively known as “logs,” that are subsequently offered on darkish internet cybercrime boards for fraudulent actions and extra cyberattacks.
The malware operates by a complicated Malware-as-a-Service (MaaS) enterprise mannequin, permitting cybercriminals to buy licenses and launch unbiased an infection campaigns.
This decentralized method has enabled RedLine to contaminate hundreds of thousands of computer systems worldwide, making it some of the profitable malware variants in circulation.
$10M Reward for Information on RedLine Malware
U.S. authorities are actively searching for details about Rudometov’s associates, notably these with connections to overseas governments concerned in malicious cyber actions.
The investigation additionally extends to monitoring using RedLine malware by overseas governments for state-sponsored cyberattacks towards American pursuits.
People with related data can securely contact the Rewards for Justice program by their Tor-based reporting channel at he5dybnt7sr6cm32xt77pazmtm65flqy6irivtflruqfc5ep7eiodiad.onion, which requires the Tor browser for nameless entry.
This encrypted communication technique ensures the protection and confidentiality of potential informants.
The substantial $10 million reward displays the intense menace posed by RedLine malware and the U.S. authorities’s dedication to disrupting cybercriminal operations that focus on American essential infrastructure.
As cyber threats proceed evolving, this case represents a major step in worldwide efforts to carry cybercriminals accountable for his or her actions towards essential programs and civilian targets.
Pace up and enrich menace investigations with Menace Intelligence Lookup! -> 50 trial search requests