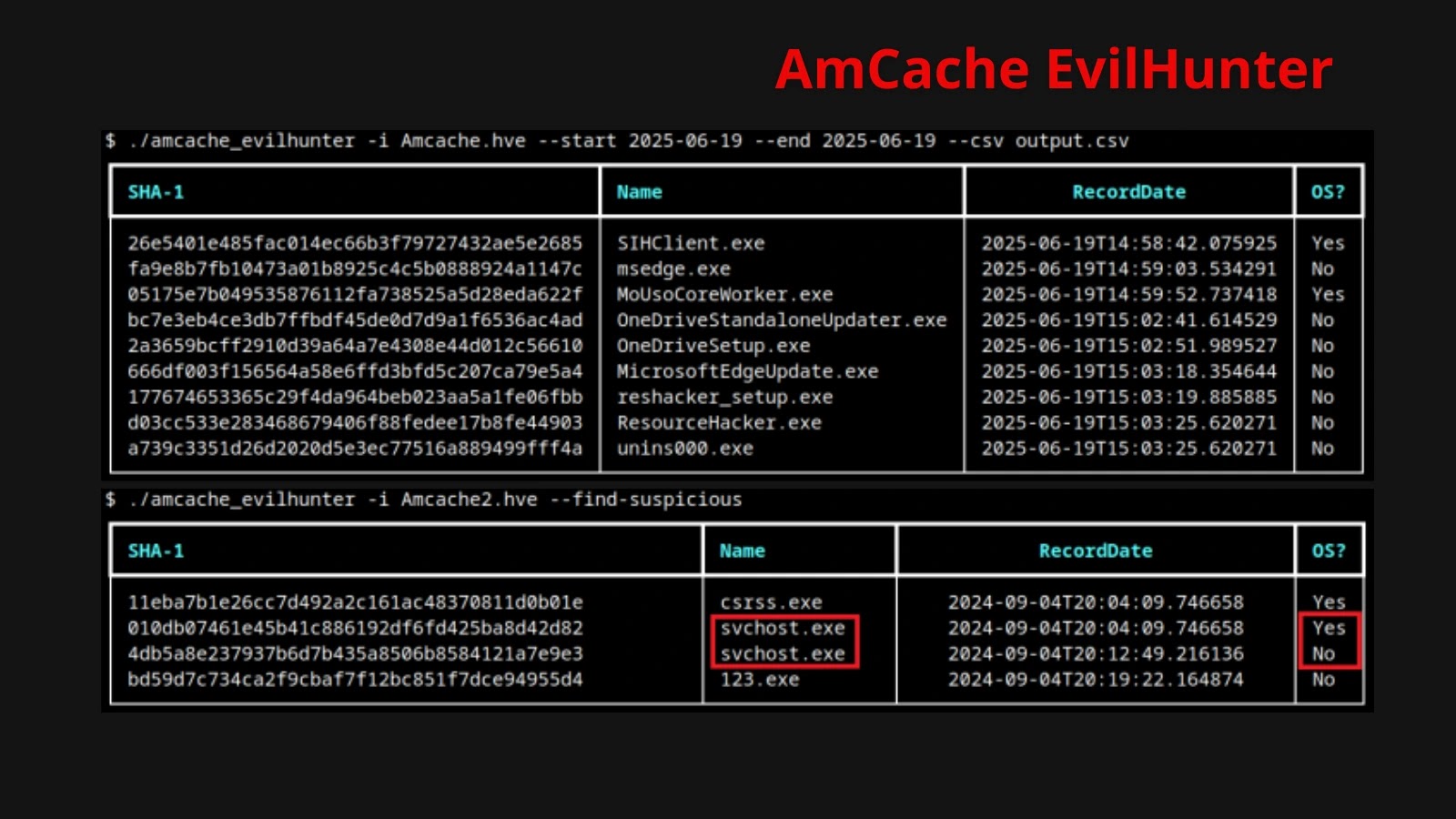
VMware has disclosed vital safety vulnerabilities in vCenter Server and NSX platforms that would permit attackers to enumerate legitimate usernames and manipulate system notifications.
The vulnerabilities, tracked as CVE-2025-41250, CVE-2025-41251, and CVE-2025-41252, have an effect on a number of VMware merchandise, together with Cloud Basis, vSphere Basis, NSX, NSX-T, and Telco Cloud platforms.
Broadcom, which acquired VMware, launched a safety advisory on September 29, 2025, ranking the vulnerabilities with CVSS base scores starting from 7.5 to eight.5, classifying them as “Essential” severity.
The Nationwide Safety Company (NSA) reported two of the three vulnerabilities, highlighting their potential nationwide safety implications.
The primary vulnerability, CVE-2025-41250, is an SMTP header injection flaw in VMware vCenter Server with a CVSS rating of 8.5.
This vulnerability allows malicious actors with non-administrative privileges who’ve permission to create scheduled duties to control notification emails despatched for these duties.
The assault vector requires authenticated entry to vCenter with activity creation permissions. By exploiting SMTP header injection methods, attackers can modify electronic mail headers, doubtlessly redirecting notifications, inserting malicious content material, or bypassing electronic mail safety filters.
This might result in social engineering assaults, credential harvesting, or unauthorized disclosure of knowledge by means of manipulated electronic mail communications.
Affected merchandise embrace vCenter Server variations 7.0, 8.0, and 9.x throughout varied VMware Cloud Basis and vSphere Basis deployments.
The vulnerability impacts VMware Telco Cloud Platform variations 2.x by means of 5.x and Telco Cloud Infrastructure variations 2.x and three.x.
Per von Zweigbergk receives acknowledgment for responsibly disclosing this vulnerability to Broadcom. No workarounds can be found, requiring organizations to use the offered safety patches instantly.
NSX Username Enumeration Vulnerabilities
Two separate username enumeration vulnerabilities have an effect on NSX platforms, creating pathways for reconnaissance assaults.
CVE-2025-41251, with a CVSS rating of 8.1, represents a weak password restoration mechanism vulnerability permitting unauthenticated attackers to enumerate legitimate usernames by means of password restoration processes.
CVE-2025-41252, scoring 7.5 on the CVSS scale, is a direct username enumeration vulnerability that allows unauthenticated malicious actors to determine legitimate usernames with out requiring authentication.
Each vulnerabilities can function reconnaissance instruments for subsequent brute-force assaults or focused credential stuffing campaigns.
Username enumeration assaults sometimes exploit variations in utility responses when processing legitimate versus invalid usernames.
Attackers can analyze response occasions, error messages, HTTP standing codes, or different behavioral patterns to find out which usernames exist within the system.
This info turns into useful for password spraying assaults, social engineering campaigns, or focused phishing makes an attempt.
The NSX vulnerabilities have an effect on VMware NSX variations 4.0.x by means of 4.2.x, NSX-T model 3.x, and NSX elements inside Cloud Basis and Telco Cloud platforms.
Organizations operating these platforms face instant publicity to reconnaissance assaults that would facilitate broader compromise makes an attempt.
Safety patches can be found by means of varied fastened variations, together with NSX 4.2.2.2, 4.2.3.1, 4.1.2.7, and NSX-T 3.2.4.3.
CVETitleCVSS 3.1 ScoreSeverityCVE-2025-41250vCenter SMTP Header Injection Vulnerability8.5ImportantCVE-2025-41251NSX Weak Password Restoration Mechanism Vulnerability8.1ImportantCVE-2025-41252NSX Username Enumeration Vulnerability7.5Important
VMware Cloud Basis customers ought to implement asynchronous patching procedures documented in KB88287. In the meantime, Telco Cloud Platform and Infrastructure customers ought to check with KB411518 for replace steering.
The NSA’s involvement in reporting these vulnerabilities underscores their significance for enterprise and authorities environments the place VMware infrastructure offers vital virtualization and networking providers.
Broadcom has already launched patches that organizations ought to prioritize to deal with these vulnerabilities, as username enumeration might allow extra subtle assault campaigns concentrating on virtualized infrastructure.
Observe us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to function your tales.