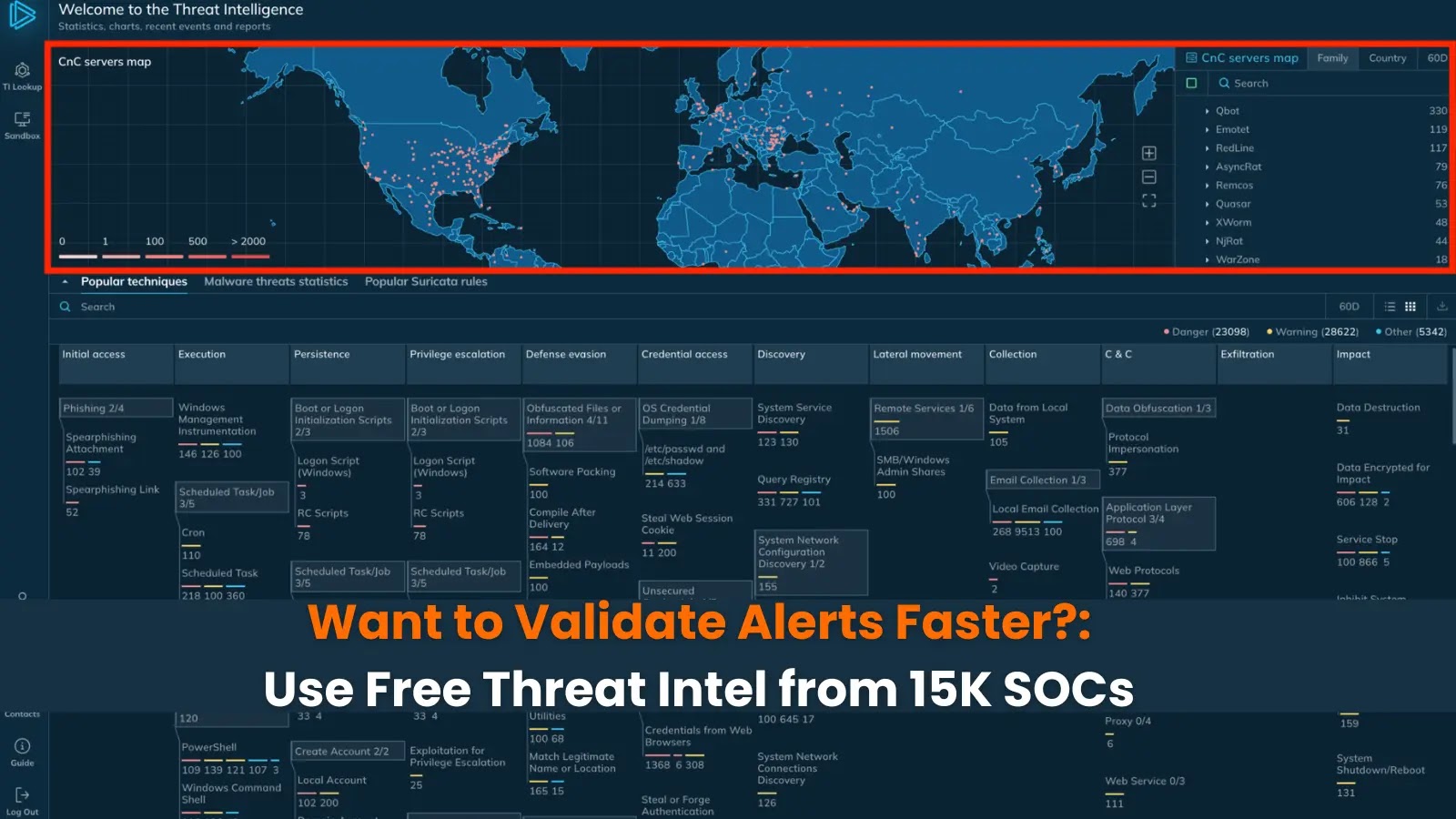
Alex sighed at his third vitality drink of the night time shift, watching one other batch of safety alerts flood his SIEM dashboard.
As a Degree 2 risk analyst at a mid-sized monetary agency, he was drowning in false positives and spending valuable hours manually investigating every suspicious hash, IP tackle, and area. Then every part modified throughout one notably brutal 3 AM investigation. Whereas researching a suspicious executable that had triggered a number of endpoint alerts, Alex stumbled upon a risk intelligence lookup service that related him to insights from hundreds of different safety operations facilities.
Inside seconds, the decision was clear: refined banking trojan, a number of C2 communications, credential harvesting capabilities.
What would have taken Alex two hours of painstaking evaluation was resolved in beneath 5 minutes. Extra importantly, he had the boldness and proof wanted to escalate instantly to the incident response crew. By morning, a possible breach had been contained.
Why Velocity is the Key: How Quicker Alert Administration Transforms Analyst’s World
Within the high-stakes area of cybersecurity, velocity isn’t a luxurious. It’s survival. Menace actors evolve in hours, not days, and each delayed response dangers escalation. However mastering alerts and artifacts at lightning velocity doesn’t simply fend off assaults; it supercharges your effectivity, effectiveness, KPIs, and profession trajectory whereas safeguarding the enterprise and nailing SOC/MSSP objectives:
1. Boosts Private Effectivity: Fast triage means dealing with 2-3x extra alerts per shift with out the psychological fog of countless rabbit holes. Options that ship immediate context, like Menace Intelligence Lookup, unencumber brainpower for inventive searching, not rote googling. See the way it works: a site search returns an immediate “Malicious” verdict, a last-seen date to guage a risk’s relevance, an inventory of further IOCs, and a collection of sandbox analyses of malware samples that includes the area.
domainName:”randomuser.me”
Area lookup outcomes with contextual information
Attempt TI Lookup to make fast actionable selections on attainable threats. Simply signal as much as begin
2. Enhances Effectiveness in Menace Searching: Fast IOC validation uncovers hidden patterns throughout incidents, turning remoted pings into proactive takedowns. You’ll spot campaigns early, disrupting attackers earlier than they burrow deep.
3. Skyrockets KPIs Like MTTR and Decision Charges: Shave minutes off every investigation and watch metrics soar. MTTR drops by as much as 10x, decision charges climb, and alert fatigue plummets. With ANY.RUN’s TI Lookup 88% of threats are detected inside 60 seconds of research. Joyful metrics imply rave efficiency critiques.
4. Accelerates Profession Development: Analysts who resolve threats sooner stand out. Quicker validations result in high-impact contributions, mentorship alternatives, and that senior position you’ve eyed. Velocity builds popularity because the go-to professional.
5. Fortifies Enterprise Safety: Swift artifact checks reduce dwell time, lowering breach prices. Early detection prevents information leaks, downtime, and regulatory fines, protecting the C-suite smiling.
See the way it works: a fast lookup exhibits a powerful correlation of an IP with Lumma, one of the harmful malware households.
destinationIP:”195.82.147.188″
IP search outcomes: now we all know that it’s a symptom of Lumma stealer within the system
6. Drives SOC Group Morale and Retention: When alerts aren’t a Sisyphean slog, burnout fades. Groups collaborate higher on validated intel, fostering a tradition of wins over exhaustion since that is the important thing for retaining high expertise in a discipline determined for expert palms.
7. Achieves SOC/MSSP KPIs with Ease: Hit SLAs on response instances, exceed consumer expectations, and scale companies with out ballooning headcount. Quicker ops imply extra billable hours and glowing testimonials, fueling enterprise progress. 90% firms report increased risk detection charges after integrating TI Lookup.
See the way it works: in case your logs comprise a suspicious PowerShell command, simply submit it to LI Lookup. imagePath:”powershell” AND commandLine:”$codigo”
Malware samples with steganography, with sandbox analyses displaying assault chains
This search outcomes expose malware that makes use of steganography: the apply of hiding malicious code within the supply code of pictures or different benign objects to keep away from detection.
Upgraded to the Premium plan, Menace Intelligence Lookup helps over 40 search parameters, further search operators, and an assortment of wildcards. Complete queries for deeper analysis develop into accessible.
Uncover TI Lookup full potential for fast risk detection, escalation, and mitigation: select you intend.
Velocity isn’t about speeding — it’s about precision. When velocity meets accuracy, each the analyst and the enterprise win.
ANY.RUN’s Menace Intelligence Lookup: Your Window into 15,000 SOCs
The breakthrough Alex skilled wasn’t luck, it was the facility of community-driven risk intelligence. ANY.RUN’s Menace Intelligence Lookup supplies immediate entry to evaluation outcomes from over 15,000 safety operations facilities worldwide who use ANY.RUN’s Interactive Sandbox for malware evaluation.
Day-after-day, safety professionals throughout the globe add suspicious recordsdata, URLs, and different artifacts to ANY.RUN’s Interactive Sandbox for evaluation. These investigations occur in real-time, making a always up to date database of risk intelligence from precise safety incidents and investigations.
While you question an IOC by way of the Menace Intelligence Lookup, you’re not simply getting static popularity information. You might be accessing recent insights from current sandbox periods the place different analysts investigated the identical indicators you’re seeing in your setting. When a hash exhibits up in your alerts, you possibly can immediately see:
Whether or not different SOCs have lately analyzed this file
What behaviors have been noticed throughout sandbox evaluation
Community communications and C2 infrastructure
File system modifications and persistence mechanisms
Screenshots and course of timber from precise execution
IOCs related to the identical marketing campaign or risk actor
Interactive sandbox periods seize the whole assault chain, serving to you perceive not simply what you’re coping with, however the way it operates and what further IOCs to hunt for in your setting.
Conclusion
Validating alerts not needs to be a gradual, painful course of. With risk intelligence from a worldwide group of SOC analysts, you possibly can flip alert overload into actionable safety insights. For risk analysts striving to excel in an ever-evolving cyber panorama, ANY.RUN’s Menace Intelligence Lookup affords an unparalleled alternative to remodel investigative effectivity and affect. By integrating it into your workflow, you possibly can considerably cut back imply time to reply (MTTR), improve detection accuracy, and obtain KPIs with better consistency, straight bolstering your skilled popularity and profession trajectory.