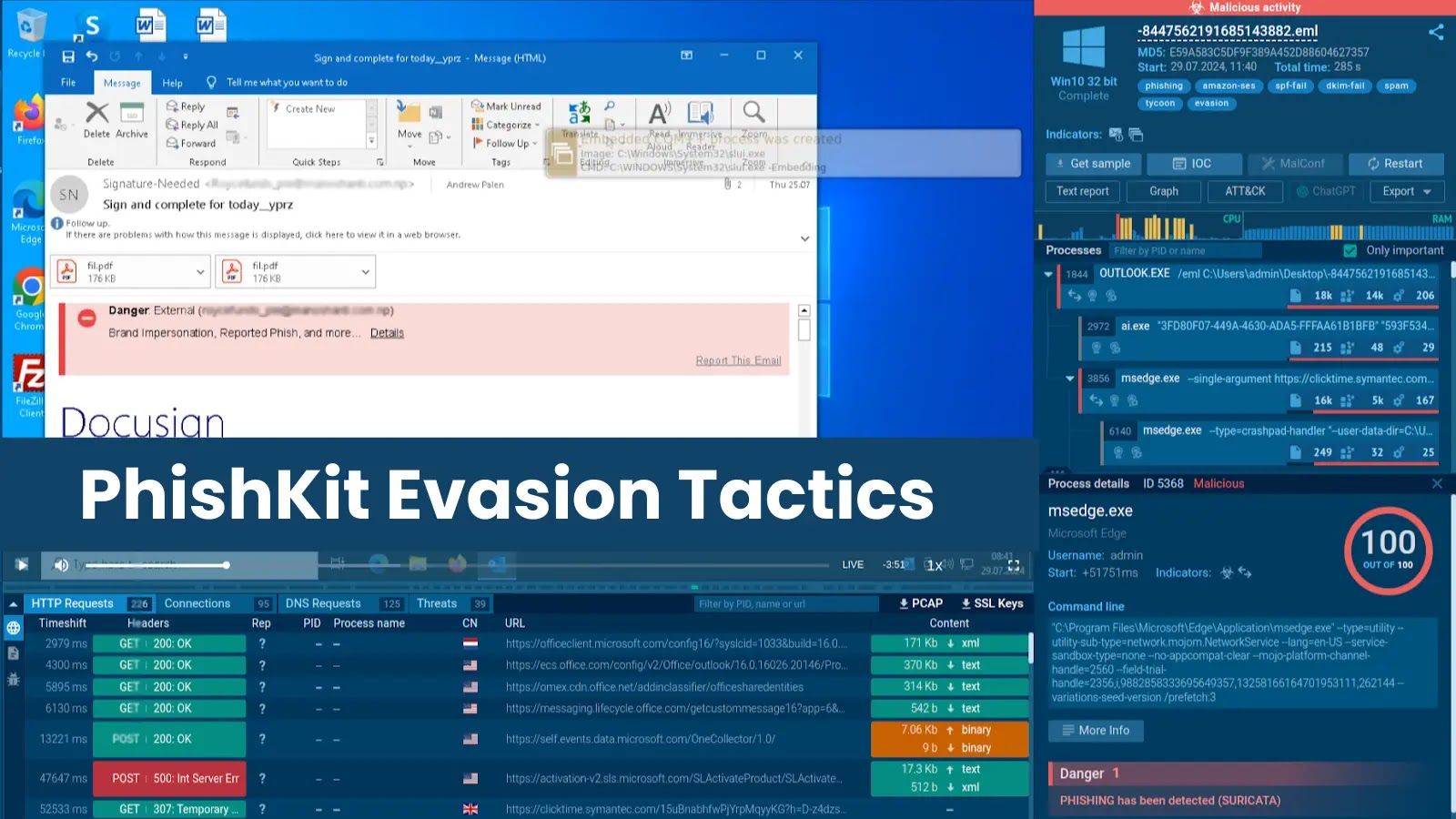
Cyber attackers always refine their evasion strategies. That’s what makes threats, together with phishing, more and more exhausting to detect and examine.
Kits like Tycoon 2FA commonly evolve with new tips added to their arsenal. They slip previous defenses and compromise firms, demonstrating nice adaptivity in fashionable cyber threats.
Let’s evaluation three key evasion methods of Tycoon 2FA utilizing ANY.RUN Interactive Sandbox.
Method #1: Use of Completely different CAPTCHAs (reCAPTCHA, IconCaptcha, and many others.)
As an alternative of utilizing a single CAPTCHA system per risk, Tycoon 2FA cycles by way of totally different suppliers, akin to reCAPTCHA, IconCaptcha, and customized CAPTCHAs.
This rotation challenges signature-based detection methods and bot-driven evaluation instruments. They aren’t capable of persistently bypass this evasion method.
For instance, within the following evaluation session of Tycoon 2FA, beforehand used customized CAPTCHA was changed with reCAPTCHA:
View evaluation
reCAPTCHA utilized in Tycoon 2FA, as proven in ANY.RUN sandbox
Different suppliers, like IconCaptcha, have been detected earlier, too (e.g. in a submission dated April 7, 2025).
Velocity up and Simplify Detection with Proactive evaluation in ANY.RUN’s Interactive Sandbox -> Join at this time
Method #2: Browser Fingerprinting
Utilizing this system, Tycoon 2FA phishing equipment can distinguish actual customers from environments for evaluation.
Fingerprinting stands for amassing detailed information on person’s system, akin to display parameters, time zone, browser particulars, and many others.
Primarily based on this knowledge, the risk decides whether or not to go on with phishing content material or to redirect the person to a legit web page. This considerably reduces detection threat by disarming sandbox-based defenses.
Within the case under, opening the phishing hyperlink results in a web page that requests picture factor and executes Base64-encoded script in case of an error:
View evaluation
Suspicious onerror handler in picture factor
If we decode the script with CyberChef, it would reveal that it’s meant to gather:
Browser knowledge, akin to display parameters, browser/platform identify, URL, host, protocol, console properties, and doc physique.
Data on time zone, JavaScript runtime internals, iframe checks, and graphical interface properties.
Different technical info.
Code used to gather browser properties
Gathered knowledge in JSON is then inserted into an invisible type and despatched to the attacker’s server by way of a POST request.
The server analyzes the fingerprint knowledge and returns a response with a Location header. There are two potential outcomes primarily based on the specifics of acquired knowledge:
Redirection to a Reliable Web page: If gathered information signifies that one thing’s off, e.g., there indicators of a sandbox, the person is redirected to a legit website like Emirates, Tesla, or SpaceX web site.
Redirect to Phishing Web page: In any other case, if the setting appears real, the person is directed to the Tycoon 2FA Stage 1 phishing web page.
Method #3: Obfuscation by way of Encryption
Whereas earlier variations of Tycoon2FA relied on easier obfuscation like Base64 or XOR, newer samples make use of AES encryption for payload obfuscation. This complicates detection considerably.
Static evaluation turns into way more troublesome, particularly when hard-coded keys and initialization vectors (IVs) are embedded within the code.
On this pattern, we are able to observe that the Tycoon2FA makes use of AES encryption for payload obfuscation, not only for importing/downloading stolen and repair knowledge within the closing phases of execution:
View evaluation
Obfuscation by way of encryption in code
Regardless that in any other case the execution chain is much like beforehand recognized, AES-level obfuscation requires way more effort for reverse engineering and detection.
Stay Webinar on New Malware Techniques
Study extra concerning the newest, most related TTPs and learn the way to detect them effectively on the webinar by ANY.RUN.
Be part of us on Wednesday, September 17 at 3:00 PM GMT.
New Malware Techniques: Instances & Detection Ideas for SOCs : Register for webinar
Conclusion: Breaking Down Evasion Techniques With ANY.RUN
These evasion methods are only a small portion of all always evolving TTPs utilized by risk actors. Conventional options that rely an excessive amount of on automation and signature-based evaluation are confirmed to be inefficient towards them.
You possibly can see higher outcomes with in-depth behavioral, interactive, not automated, evaluation. That’s what ANY.RUN delivers with its sandbox:
Interactivity in Actual Time: Analyze malware from its very core by observing and investigating its habits in motion.
Quick Outcomes: See verdicts and establish malware households in underneath 40 seconds upon the launch to chop your evaluation time to mere minutes.
Detailed Habits Evaluation: Achieve clear visibility into fashionable risk techniques, methods, and procedures for thorough investigation.
Environment friendly Automation: Detonate threats hands-free with Automated Interactivity and lower your workload by automating time-consuming routine duties.
In-depth Analysis and Proactive protection for SOC groups : Strive ANY.RUN