Cybersecurity is about to hit a turning level in 2026. Attackers aren’t solely testing AI but in addition constructing campaigns round it. Their tooling is getting sooner, extra adaptive, and much better at mimicking consumer conduct, from reconnaissance to phishing to preliminary entry.
The Shift is Already Underway
With geopolitical stress rising and know-how accelerating, SOCs are getting into a interval the place each workload and complexity spike on the similar time. Groups are already drowning in alerts, roughly 11,000 per day on common, and the curve is trending up, not down.
Executives are feeling the affect too: disruptions, compliance dangers, and monetary losses tied to breaches have gotten extra frequent.
Listed below are the three traits shaping the SOC of 2026, and why the organizations that act now can have a transparent edge over everybody else.
Development #1: Actual-Time, Analyst-in-the-Loop Investigations Turn out to be the New Normal
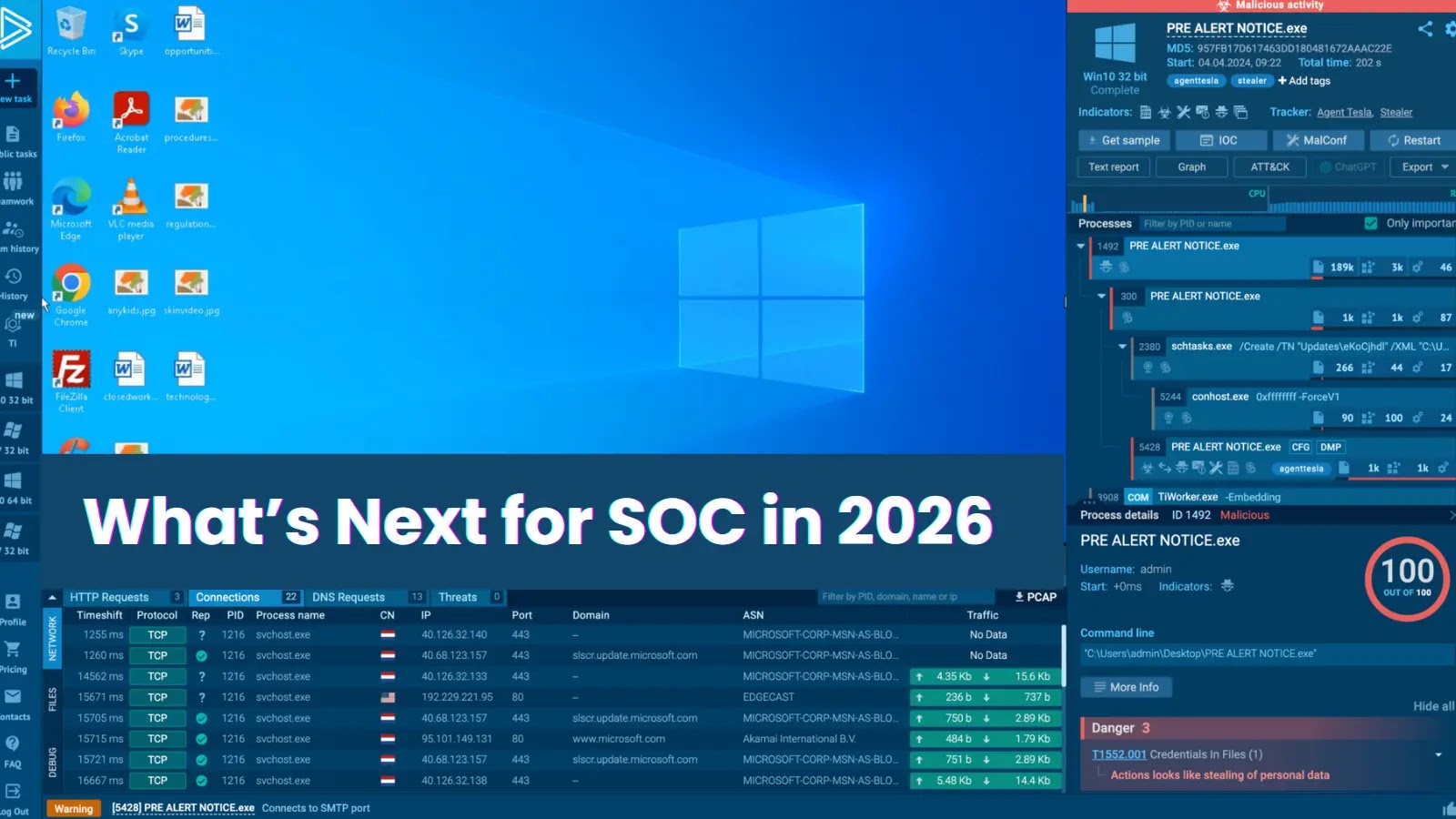
Ready for a verdict is rapidly turning into a luxurious SOCs can’t afford. In 2026, main groups are shifting towards reside, analyst-in-the-loop investigations, the place execution and investigation occur on the similar time contained in the sandbox.
As an alternative of working a pattern, ready for a report, and solely then deciding what to check subsequent, analysts now step into the session whereas the menace continues to be working. They work together with information, set off actions, comply with suspicious paths, and validate assumptions immediately.
This removes the standard two-cycle workflow: run → wait → overview → rerun.
Now, investigation and validation occur in one steady circulate. The total assault path turns into seen throughout execution, not after. That alone cuts minutes out of each case and sharply reduces repeat detonations.
Reside interactivity turns into a bonus
ANY.RUN’s sandbox is constructed for real-time analyst engagement. Whereas the pattern executes, investigation occurs in parallel, permitting hypotheses to be examined instantly and edge instances to be uncovered with out stopping the run.
See phishing assault uncovered in 60 seconds utilizing interactive sandbox
Pretend Google Careers web page displayed inside ANY.RUN sandbox
As an alternative of ready for a static report:
Conduct turns into seen because it unfolds
Execution might be pushed ahead the second it stalls
Intent is confirmed earlier than any escalation occurs
IOCs floor naturally as the total chain is uncovered
Minimize investigation time, cut back analyst overload, and enter 2026 with a SOC constructed for velocity and readability. Discuss to ANY.RUN Specialists
For management, this interprets into shorter investigation cycles, fewer re-runs, and sooner selections. The sandbox stops being a separate step within the course of and turns into a reside investigation floor the place execution and evaluation occur collectively.
Development #2: Assaults Now Count on Human Participation
Assault methods are not constructed to run on their very own. A lot of at this time’s most profitable campaigns rely upon human interplay to maneuver ahead. Workers are prompted to stick PowerShell instructions manually.
Constructed-in system instruments are quietly abused to mix into regular exercise. Phishing chains now conceal behind QR codes, CAPTCHAs, layered redirects, and pretend installers that look innocent at first look.
That is the place conventional sandboxes nonetheless fall quick. If a detonation can’t click on a button, resolve a problem, or comply with a user-triggered step, the assault merely by no means reveals itself. The result’s predictable: the fastest-growing menace methods are sometimes the toughest to look at.
Clear up it with interactive evaluation
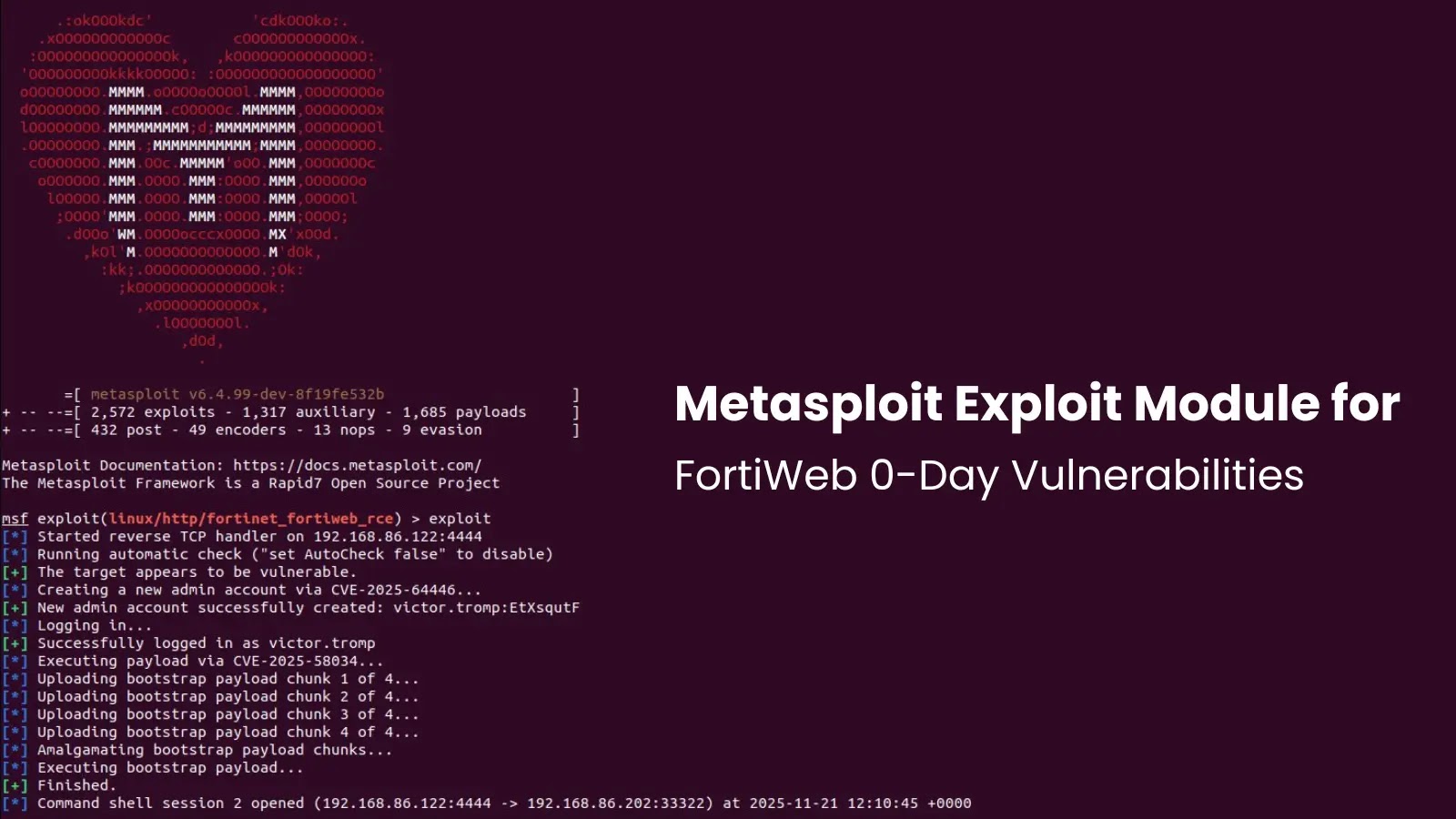
ANY.RUN addresses this shift with Automated Interactivity constructed straight into its sandbox. As an alternative of passively observing execution, the atmosphere actively pushes the assault ahead, performing the identical actions an actual consumer would, however persistently and at scale.
ANY.RUN’s sandbox mechanically runs a PowerShell command in a ClickFix assault
Throughout evaluation, the sandbox mechanically:
Extracts hyperlinks embedded inside QR codes
Removes monitoring and safety rewrites from URLs
Navigates multi-step redirect chains
Processes attachments and nested archives
Executes payloads hidden a number of layers deep
Every stage is uncovered and executed as a part of a single, steady chain.
The affect for the enterprise is fast and tangible. SOC groups don’t simply see the place an assault begins; they see the place it leads. Full execution paths seem in actual time. IOCs floor earlier.
Detection logic evolves sooner. What as soon as required repeated guide testing throughout a number of instruments now turns into a single, managed course of with far fewer blind spots.
Development #3: Visible Proof and Clear Reporting Turn out to be a Core SOC Requirement
By 2026, detection alone will not be sufficient. SOCs are underneath rising strain to clarify what occurred, the way it labored, and why it issues not simply to incident responders, however to executives, compliance groups, auditors, and clients.
Logs and uncooked alerts don’t reply these questions properly. They’re laborious to interpret outdoors the SOC, they usually hardly ever present the total story of an assault. As assaults turn into extra layered and evasive, the hole between technical detection and enterprise understanding retains widening.
That’s why visible menace demonstration and structured reporting have gotten a core SOC functionality, not only a “good to have.”
Turning reside execution into business-ready proof
ANY.RUN addresses this shift by turning reside sandbox execution into clear, visible proof that may be shared throughout groups. As an alternative of summary indicators, stakeholders see the actual assault unfold step-by-step.
Textual content report with related IOCs, conduct evaluation, screenshots, and many others. Generated by ANY.RUN
Robotically generated sandbox stories make it doable to indicate:
How the preliminary entry occurred
Which processes have been launched and why
What community connections have been tried
The place persistence was created
How knowledge motion or payload supply unfolded
Every IOC is tied on to noticed conduct, eradicating guesswork and making investigations simpler to defend throughout audits, incident evaluations, and post-breach evaluation.
For SOC leaders, this visibility modifications the dialog with the enterprise. Safety stops sounding like chance and begins trying like documented threat discount.
In 2026, the SOCs that earn belief quickest would be the ones that may present precisely what a menace did, not simply label it. Clear visible reporting is turning into the bridge between technical execution and enterprise confidence.
Constructing the SOC That’s Prepared for 2026
The shift is already underway. At this time, greater than 15,000 organizations and 500,000+ safety analysts world wide depend on ANY.RUN to research actual threats, validate selections, and keep forward of fast-moving assault chains. This displays the tangible outcomes groups are seeing in fast-paced, real-world SOC environments.
50% minimize in MTTR by shifting from delayed verdicts to reside, interactive investigations
3× increase in SOC effectivity by combining analyst-driven evaluation with automated execution paths
30% discount in Tier 1 → Tier 2 escalations due to early full-chain visibility and stronger first-pass verdicts
That is what readiness appears like going into 2026: sooner solutions, fewer blind spots, and a SOC that scales with out breaking.
Discuss to ANY.RUN consultants to see how these traits translate into actual outcomes on your SOC.
The publish What’s Subsequent for SOC in 2026: Get the Early-Adopter Benefit appeared first on Cyber Safety Information.