WhatsApp 0-click distant code execution (RCE) vulnerability affecting Apple’s iOS, macOS, and iPadOS platforms, detailed with a proof of idea demonstration.
The assault chain exploits two distinct vulnerabilities, recognized as CVE-2025-55177 and CVE-2025-43300, to compromise a goal system with out requiring consumer interplay.
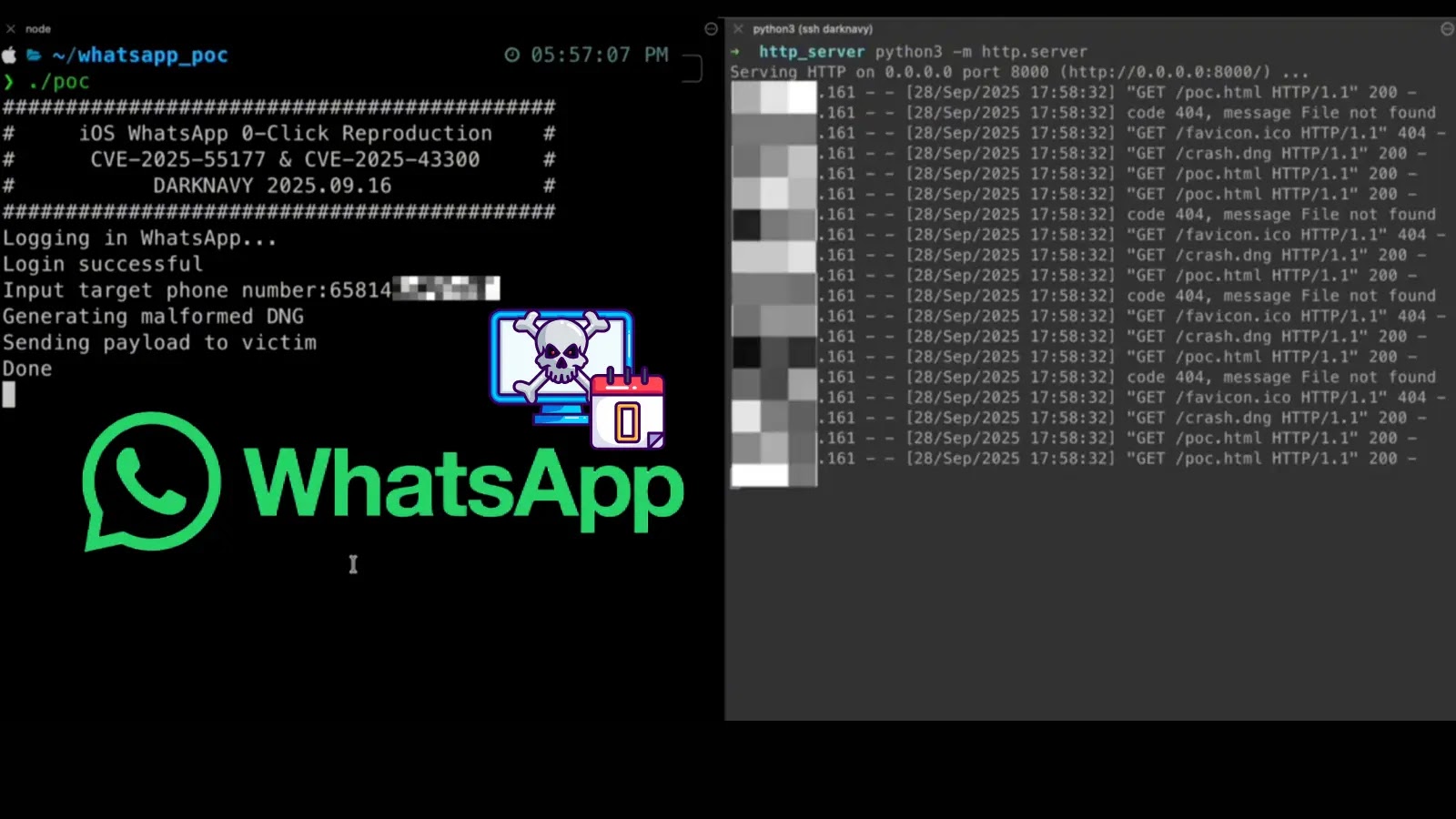
The exploit, demonstrated in a proof-of-concept (PoC) shared by the DarkNavyOrg researchers, is initiated by sending a specifically crafted malicious (DNG) picture file to a sufferer’s WhatsApp account.
As a “zero-click” assault, the vulnerability is triggered mechanically upon receipt of the malicious message, making it notably harmful as victims haven’t any alternative to stop the compromise.
0-click Assault PoC WhatsApp
WhatsApp 0-Click on Vulnerability Exploit Chain
The assault’s entry level is CVE-2025-55177, a vital logic flaw inside WhatsApp’s dealing with of messages.
Based on DarkNavyOrg, the vulnerability stems from a lacking validation examine to verify that an incoming message originates from a reputable linked system.
This oversight permits an attacker to ship a message that seems to be from a trusted supply, bypassing preliminary safety checks and delivering the malicious payload.
We triggered WhatsApp 0-click on iOS/macOS/iPadOS.CVE-2025-55177 arises from lacking validation that the [Redacted] message originates from a linked system, enabling specifically crafted DNG parsing that triggers CVE-2025-43300.Evaluation of Samsung CVE-2025-21043 can be ongoing. pic.twitter.com/idwZXqh5WK— DARKNAVY (@DarkNavyOrg) September 28, 2025
As soon as the message is delivered, the second vulnerability, CVE-2025-43300, is triggered. This flaw resides within the software’s DNG file parsing library.
The attacker crafts a malformed DNG picture that, when processed by WhatsApp, causes a reminiscence corruption error, resulting in distant code execution.
The proof-of-concept shared by the researchers reveals a script that automates the method: logging into WhatsApp, producing the malformed DNG, and sending the payload to a goal cellphone quantity. This mixture permits for a seamless and silent compromise of the focused system.
This zero-click RCE vulnerability poses a extreme risk to customers of WhatsApp on a number of Apple gadgets, together with iPhones, Mac computer systems, and iPads.
A profitable exploit may grant an attacker full management over a tool, enabling them to entry delicate information, monitor communications, and deploy additional malware. The stealthy nature of the assault means a tool may very well be compromised with none seen indicators.
The invention highlights the continuing safety challenges related to complicated file codecs and cross-platform messaging purposes. Flaws in file parsers have traditionally been a typical vector for RCE exploits, as they course of untrusted exterior information.
DarkNavyOrg has indicated that its evaluation is ongoing, together with a separate investigation right into a Samsung-related vulnerability (CVE-2025-21043).
For now, WhatsApp customers are suggested to make sure their purposes and working methods are all the time up to date to the newest variations to obtain safety patches as quickly as they change into obtainable. Each WhatsApp and Apple are anticipated to handle these vital vulnerabilities in upcoming safety updates.
Observe us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.