Safety Operations Facilities (SOCs) exist below ever-increasing stress to detect and reply to threats earlier than they escalate.
Right now’s fast-moving adversaries exploit gaps in risk visibility with automation, focused ransomware, and zero-day exploits. The end result? Extreme operational disruptions, monetary losses, and reputational hurt.
Classes from Current Cyber Disruptions
These latest high-impact incidents present why SOCs want real-time risk intelligence and top-notch sources of risk information, not simply reactive steering.
Jaguar Land Rover (JLR)
A cyberattack this September halted manufacturing at Solihull and Merseyside vegetation and disrupted retail operations, forcing a worldwide methods shutdown throughout peak registration intervals. Though buyer information remained intact, the operational fallout was important
How real-time TI may assist: Early detection of attacker instruments (e.g. ransomware variants from teams like Scattered Spider) may allow speedy community segmentation, containment, and risk blocking—minimizing manufacturing facility downtime and retail influence.
Marks & Spencer (M&S)
In a classy cyberattack earlier this 12 months, M&S estimated a $400 million loss in working revenue. On-line orders had been suspended for as much as six weeks, meals availability plunged, waste elevated, and logistics prices soared .
Preventive potential of real-time TI: Speedy identification of attacker TTPs (e.g. contactless fee disruption strategies) may empower SOCs to isolate methods, implement guide overrides, and defend crucial supply-chain operations in actual time.
Co-op (UK)
A cyber-disruption pressured guide scanning, empty cabinets, and information publicity of 6.2 million clients. In response, Co-op launched a buyer “thank-you” marketing campaign to regain belief
Actual-time benefit: Early intelligence on phishing or infostealer exercise may set off preventive alerts, defend backend methods, and avert each operational disruption and client belief erosion.
In February 2025, ransomware group Qilin encrypted recordsdata and exfiltrated 350 GB from 75 native newspapers, disrupting each print and digital workflows
Well timed TI worth: Actual-time insights on ransomware-associated IOC patterns may activate automated shutdowns or safe-mode transitions by minimizing downtime in crucial media supply operations.
Ahead-thinking organizations acknowledge that real-time risk intelligence transforms their SOC from a value heart right into a aggressive benefit.
Constructing SOC Capabilities That Scale
Probably the most environment friendly SOCs don’t simply eat risk intelligence: they combine it into automated response workflows. Actual-time feeds allow dynamic coverage updates, automated quarantine choices, and clever alert prioritization.
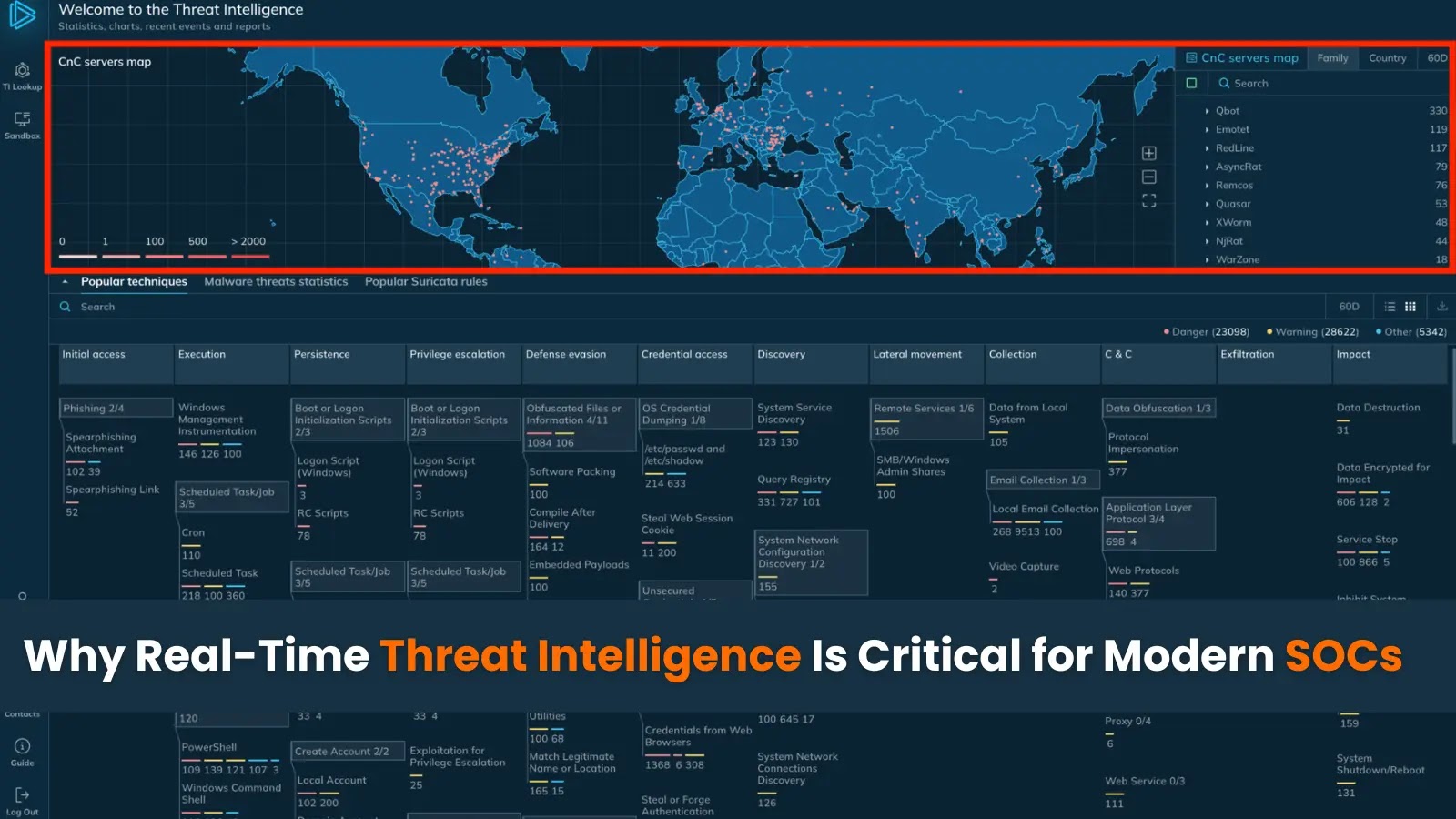
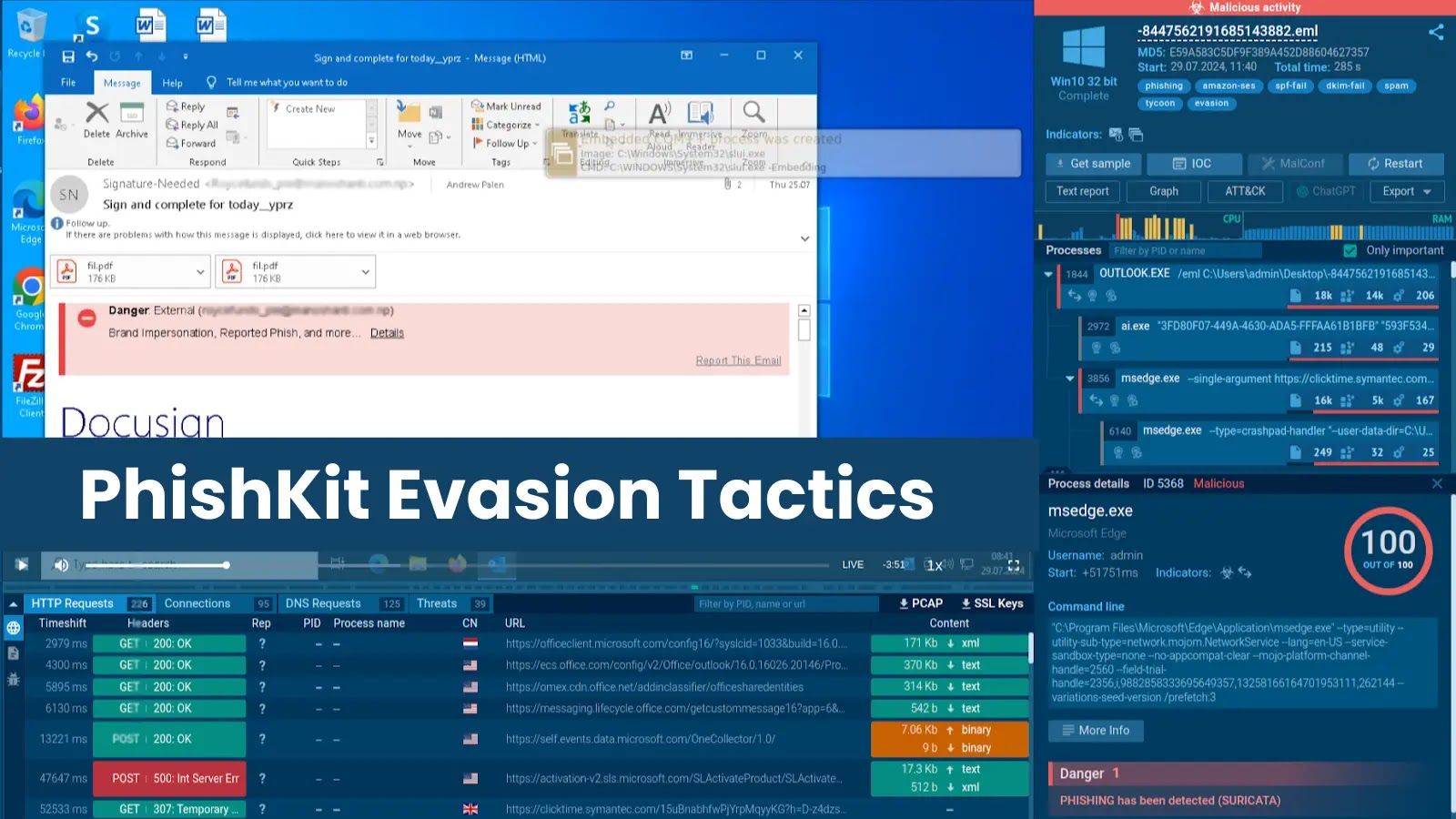
ANY.RUN’s Risk Intelligence Feeds exemplify this strategy by offering not simply indicators, however actionable intelligence with speedy context.
Lower MTTR, downtime, and breach losses with real-time risk intelligence : Contact ANY.RUN to get entry to actionable IOCs
They gasoline safety methods with malicious IPs, domains, URLs extracted from dwell sandbox analyses of the newest threats hitting 15,000+ organizations worldwide:
Key Enterprise Positive factors from Actual-Time Risk Intelligence
The influence isn’t theoretical — it’s transformational:
Minimized operational disruption: Act instantly on rising threats, containing them earlier than escalation.
Seen ROI: Decreased MTTR (Imply Time to Reply) and enterprise interruption defend income and fame.
Environment friendly useful resource use: Analysts focus efforts on validated actual threats as a substitute of sifting by way of stale or irrelevant alerts.
Resilience and belief: Strengthen enterprise continuity and stakeholder confidence, even below assault.
ANY.RUN’s TI Feeds Profit Enterprise Affect Actual-time detection Cut back downtime (avoiding multi-million disruptions) Sooner response Comprise threats earlier than escalation Useful resource effectivity Fewer alerts, extra focus Proactive safety Forestall repetitive breaches throughout sectors Enhanced KPI efficiency Higher MTTR, stronger SLAs, enterprise continuity
Conclusion: Turning Risk Information into Enterprise Resilience
The latest disruptions throughout industries show a easy reality: cyberattacks should not simply IT issues. They’re enterprise issues with a direct influence on income, operations, and fame.
For executives, the price of counting on delayed or incomplete intelligence is measured not solely in misplaced income, but in addition in eroded buyer belief and weakened aggressive benefit.
Actual-time risk intelligence transforms this equation. By arming SOCs with dwell, verified insights from world assault exercise, leaders can guarantee sooner detection, sharper response, and stronger resilience in opposition to even essentially the most superior threats.
With ANY.RUN’s Risk Intelligence Feeds, organizations and MSSPs transfer from reactive protection to proactive safety: minimizing danger, optimizing safety investments, and securing enterprise continuity in an unpredictable digital panorama.