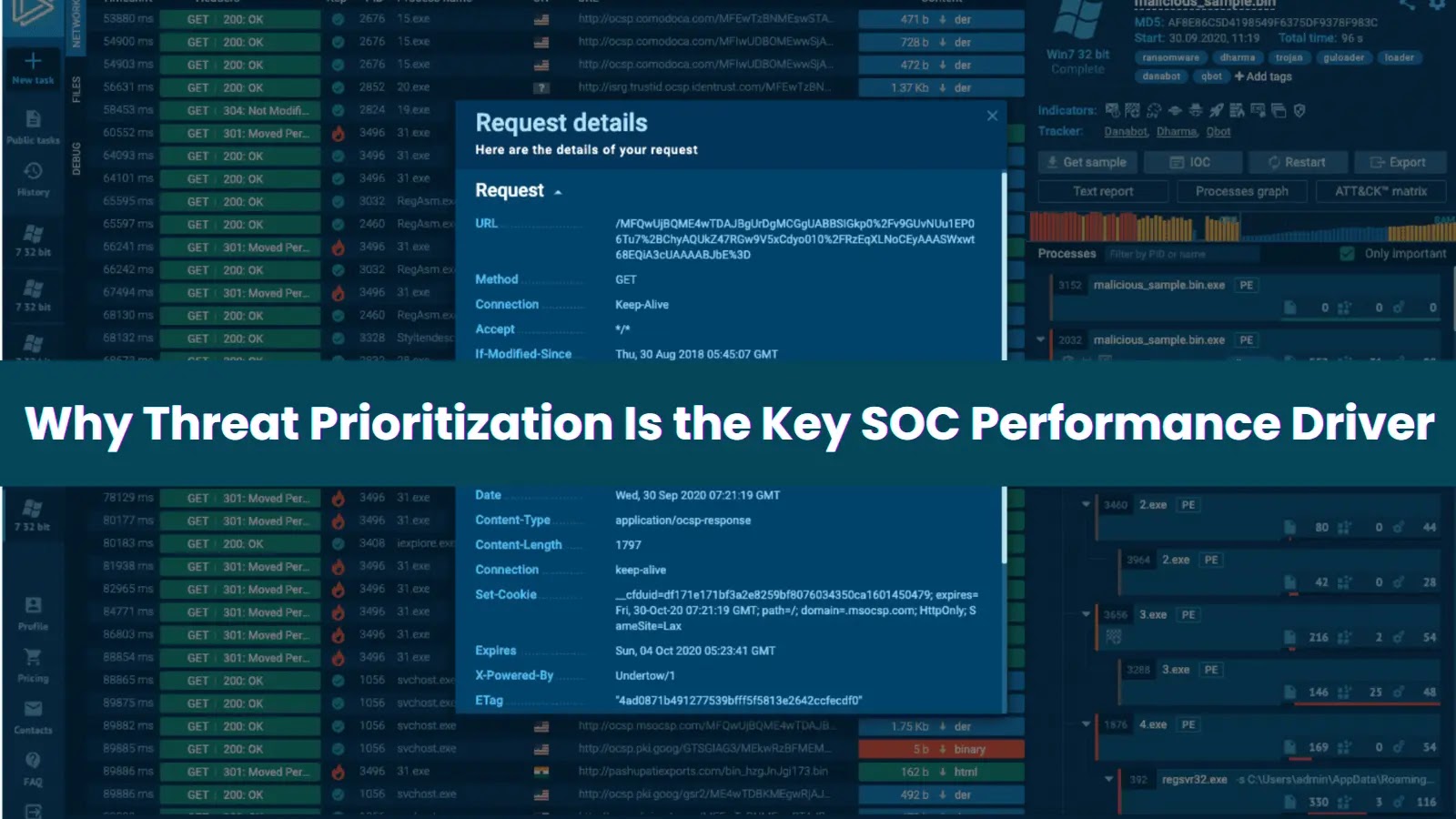
CISOs face a paradox of their SOCs every single day: extra information and detections than ever earlier than, but restricted capability to behave on them successfully.
Tons of of alerts stream in every day, however with out clear prioritization, the group’s focus is scattered.
Essential incidents danger being buried amongst lower-value occasions, slowing response and rising enterprise publicity.
The Value of Dropping Focus
From a enterprise perspective, the implications of poor alert administration are extreme:
Escalating operational prices as analysts spend time on irrelevant indicators.
Slower decision-making, leaving essential incidents unresolved for longer.
Broader danger floor, as real threats can progress unchecked.
In the end, a SOC’s effectiveness isn’t measured by the variety of alerts processed, however by how shortly it might determine and neutralize those who pose the best danger to the group.
Why Prioritization Is Important
The true driver of SOC efficiency is the flexibility to separate sign from noise.
Prioritization ensures that assets, individuals, instruments, and time, are allotted the place they matter most. This requires greater than detection; it requires context.
Risk context solutions elementary enterprise questions:
Is that this alert tied to an energetic marketing campaign in our business?
Does it signify a risk able to monetary or reputational hurt?
How pressing is the chance in comparison with others within the queue?
With out this context, the SOC can not align operational focus with enterprise danger. The Energy of Collective Intelligence
That is the place options like ANY.RUN’s Risk Intelligence Lookup essentially change the equation.
TI Lookup: discover threats and indicators with 40+ search parameters
By aggregating risk information from over 15,000 SOCs globally, the platform creates a real-time intelligence ecosystem offering full context about an alert: severity, related campaigns, noticed behaviors, recent IOCs.
Entry to real-time intelligence from a worldwide SOC community means your group sees rising threats as they develop.
As a substitute of spending half-hour researching an indicator throughout a number of sources, analysts get consolidated intelligence immediately.
With clear risk prioritization, your group can confidently deprioritize low-risk alerts and focus on real threats. For CISOs, this implies:
Quicker triage: Analysts spend seconds, not hours, validating alerts.
Threat-based focus: Essential incidents are escalated first, lowering dwell time.
Strategic effectivity: The SOC operates with better ROI, making certain investments in individuals and expertise translate immediately into stronger resilience.
Velocity up detection and response to depart each attackers and competitors behind Contact ANY.RUN for 50 trial searches in Risk Intelligence Lookup
A easy instance: a suspicious IP tackle noticed in system logs could be checked in seconds:
destinationIP:”172.67.150.243″
TI Lookup IP search: on the spot verdict, context, and IOCs
An analyst sees that the area has been tagged as malicious and related to ongoing phishing campaigns powered by the infamous EvilProxy phishkit.
They’ll additionally browse sandbox evaluation classes, analyze TTPs and tendencies, and collect IOCs for detection and response.
From Reactive to Proactive
Efficient risk prioritization doesn’t simply make your SOC sooner: it essentially transforms how safety operations operate. Groups shift from reactive alert processing to proactive risk looking.
Analysts spend much less time on false positives and extra time creating defensive methods. MTTR for essential incidents drops dramatically.
For CISOs, this operational transformation delivers measurable enterprise worth: lowered danger publicity, extra environment friendly safety spending, and a group that’s engaged fairly than exhausted.
The Backside Line
In at present’s risk panorama, success isn’t about processing extra alerts — it’s about processing the fitting alerts with the suitable urgency.
Risk intelligence-driven prioritization supplies the context that transforms safety operations from overwhelmed to optimized.
The organizations profitable the safety battle aren’t essentially these with the most important budgets or probably the most instruments.
They’re those which have mastered the artwork of clever prioritization, leveraging options like Risk Intelligence Lookup to chop via noise and give attention to threats that truly matter.
Begin your TI Lookup trial, make your SOC proactive, targeted, and environment friendly