A vulnerability in Microsoft’s newly carried out Rust-based kernel element for the Graphics Gadget Interface (GDI) in Home windows.
This flaw, which may set off a system-wide crash by way of a Blue Display of Loss of life (BSOD), highlights the challenges of integrating memory-safe languages into important OS parts.
Though Microsoft categorised it as reasonable severity, the difficulty underscores potential dangers in enterprise environments the place attackers would possibly weaponize it for widespread disruption.
The vulnerability emerged throughout a focused fuzzing marketing campaign by Test Level, aimed toward probing Home windows’ graphics subsystem for weaknesses. Fuzzing, a method that bombards software program with malformed inputs to reveal bugs, proved instrumental right here.
Utilizing instruments like WinAFL and WinAFL Pet on a managed take a look at setup, researchers centered on the Enhanced Metafile Format (EMF) and EMF+ recordsdata’ compact constructions that instruct GDI on rendering 2D graphics.
These recordsdata, typically embedded in paperwork or photographs, have lengthy been a vector for exploits on account of their complexity.
Beginning with simply 16 seed recordsdata, the fuzzers shortly unearthed crashes starting from info leaks to code execution dangers in user-space parts.
However the true breakthrough got here unexpectedly: repeated system restarts after BugChecks pointed to a kernel-level difficulty. Dubbed a “Denial of Fuzzing” situation, it halted testing and compelled a pivot to kernel forensics.
Home windows Rust-based Kernel GDI Vulnerability
To isolate the offender, Test Level enhanced its setup with reminiscence dump evaluation utilizing MemProcFS and Volatility, extracting mutated recordsdata from RAM disks.
They refined the corpus iteratively, shrinking copy time from days to half-hour throughout 836 samples.
A intelligent harness modification streamed mutations to a distant server by way of a customized C perform and Python listener, capturing the exact 380,000th mutation that triggered the crash.
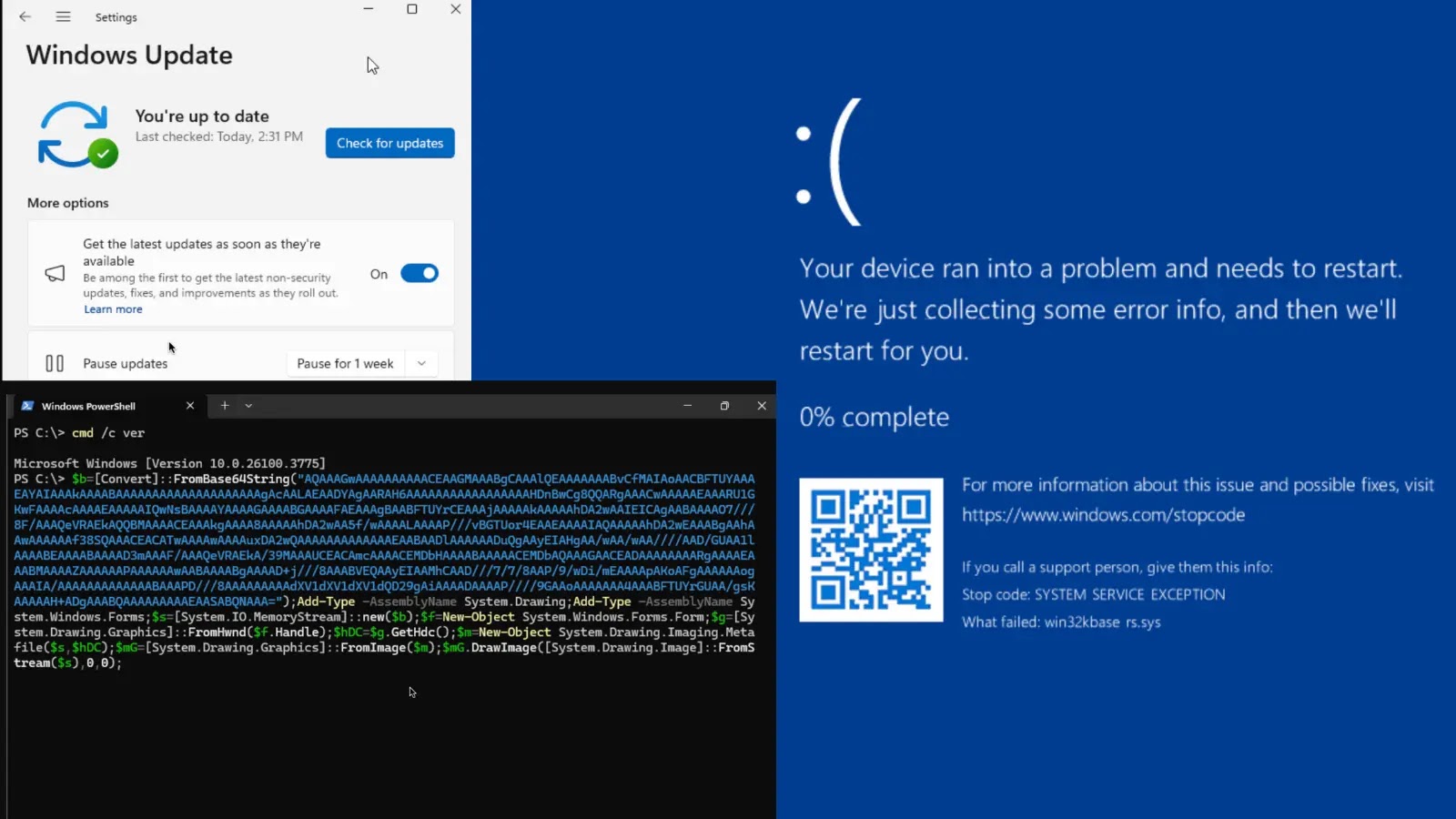
Deep evaluation revealed the bug in win32kbase_rs.sys, Microsoft’s Rust-rewritten driver for GDI areas.
Throughout path-to-region conversion in NtGdiSelectClipPath, an out-of-bounds array entry in region_from_path_mut() invoked Rust’s panic_bounds_check(), inflicting a SYSTEM_SERVICE_EXCEPTION.
Service Exception
The set off? A malformed EmfPlusDrawBeziers report with mismatched level counts (17 factors declared as 4) and anomalous coordinates, mixed with a wide-stroke pen from an EmfPlusObject.
This malformed geometry pressured edge block dealing with, bypassing bounds within the singly linked checklist illustration.
A easy PowerShell proof-of-concept demonstrated the exploit’s accessibility: embedding the crafted metafile in a Graphics object by way of System.Drawing led to an instantaneous BSOD, even from low-privilege periods on x86/x64 Home windows 11 24H2.
Whereas not enabling distant code execution immediately, it posed a potent denial-of-service risk think about an insider scripting crashes throughout an enterprise on a Friday night.
Microsoft patched the flaw in OS Construct 26100.4202 by way of the KB5058499 preview on Might 28, 2025, increasing the driving force by 16KB with hardened logic.
Key adjustments included twin edge-handling routines add_edge_original() and a bounds-checked add_edge_new(), gated by a function flag. Full rollout adopted in June, although preliminary testing confirmed the flag disabled.
Test Level reported the difficulty promptly, however Microsoft’s MSRC deemed it a non-critical DoS, arguing Rust’s panic mechanism behaved as designed.
This marks one of many first public Rust kernel bugs post-integration, as touted at BlueHat IL 2023 for enhancing safety. Whereas Rust mitigates overflows, it doesn’t eradicate design flaws or incomplete testing.
As Home windows leans into reminiscence security, such incidents remind builders: language alone isn’t a panacea. Thorough fuzzing and validation stay very important to forestall “alarm methods that blow up the home.”
Comply with us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to function your tales.