A classy new method that exploits the Home windows Non-public Character Editor to bypass Person Account Management (UAC) and obtain privilege escalation with out person intervention, elevating important issues for system directors worldwide.
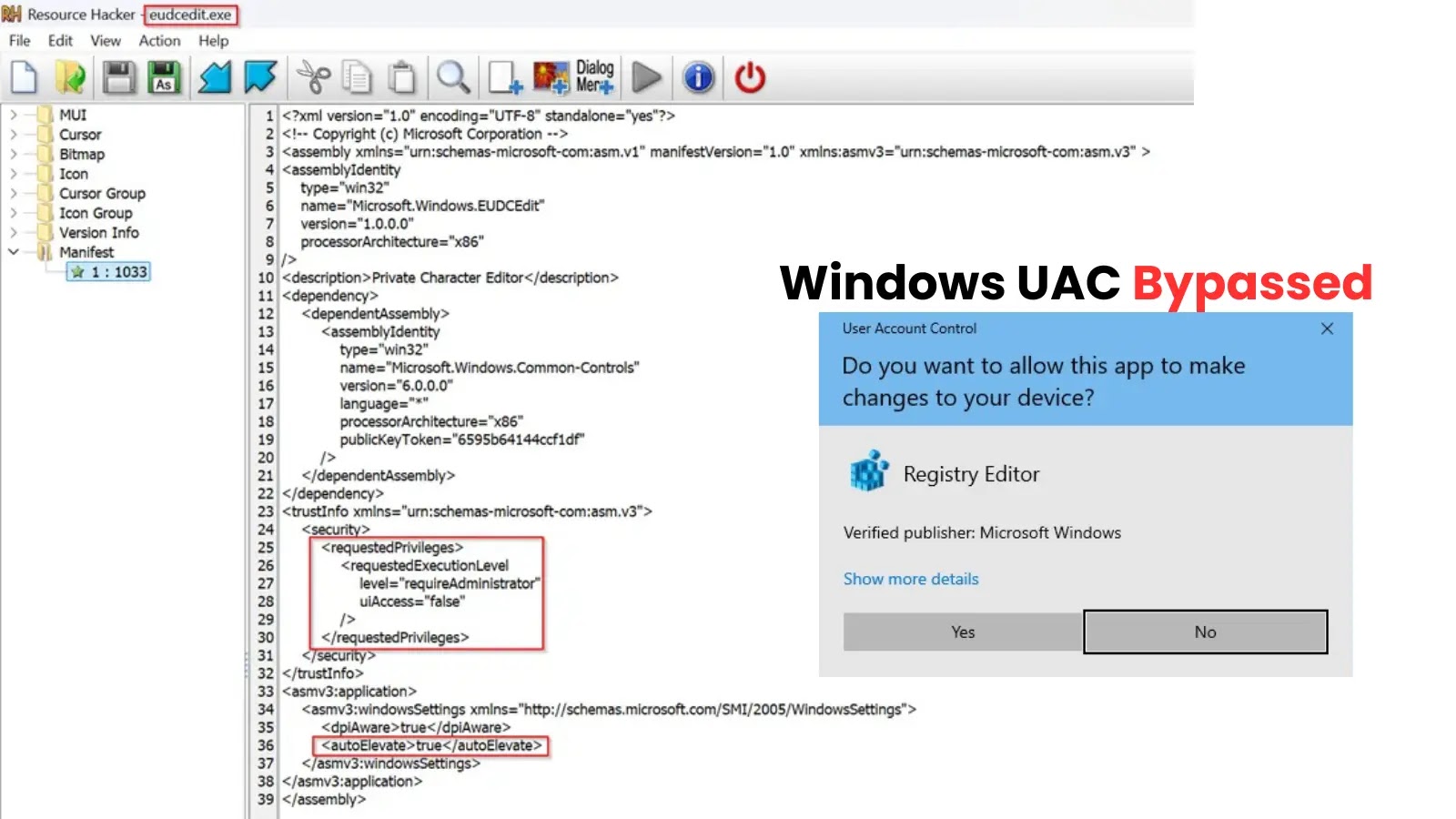
The assault disclosed by Matan Bahar leverages eudcedit.exeMicrosoft’s built-in Non-public Character Editor, positioned in C:WindowsSystem32, which was initially designed to create and edit Finish-Person Outlined Characters (EUDC).
These customized characters permit customers to create personalised glyphs mapped to Unicode code factors to be used in paperwork and functions. Nevertheless, safety researchers have found that this seemingly benign utility will be weaponized to bypass Home windows’ major safety gatekeeper.
App File
Home windows Person Account Management Bypassed
The vulnerability stems from vital configurations embedded inside eudcedit.exe’s utility manifest. Two particular metadata tags create the safety loophole:
– Instructs Home windows to run the binary with full administrative privileges
true – Permits automated elevation with out UAC prompts for trusted binaries when executed by customers within the Directors group.
This mixture proves notably harmful. When UAC is configured with permissive settings similar to “Elevate with out prompting,” Home windows robotically elevates eudcedit.exe from Medium to Excessive integrity with out displaying any safety warnings, Bahar stated.
The assault unfolds by way of a rigorously crafted sequence that exploits the applying’s file dealing with mechanisms. Attackers start by launching the Non-public Character Editor, which robotically elevates to Excessive integrity.
They then navigate to the font linking performance inside the utility interface, sometimes accessed by way of the File menu.
The vital vulnerability manifests when customers choose font linking choices and are prompted to avoid wasting information. At this juncture, the elevated eudcedit.exe course of will be manipulated to execute arbitrary instructions.
By merely getting into “PowerShell” within the file dialog, attackers can spawn a high-privilege PowerShell session that inherits the elevated integrity degree of the mum or dad course of.
powershell display
Microsoft’s method to UAC bypasses stays in line with historic patterns. Since UAC is designed as a comfort characteristic moderately than a safety boundary, the corporate sometimes doesn’t concern patches for bypass methods.
The eudcedit.exe UAC bypass demonstrates how attackers can weaponize authentic system utilities to attain malicious targets. This method’s simplicity and effectiveness make it a big concern for enterprise safety groups.
Equip your SOC with full entry to the newest risk knowledge from ANY.RUN TI Lookup that may Enhance incident response -> Get 14-day Free Trial