Safety researchers have confirmed lively exploitation of a crucial vulnerability in Wing FTP Server, simply in the future after technical particulars have been publicly disclosed.
The flaw, tracked as CVE-2025-47812, has acquired the utmost CVSS rating of 10.0 and allows unauthenticated distant code execution with root or SYSTEM privileges.
The vulnerability was first disclosed by safety researcher Julien Ahrens on June 30, 2025, following a accountable disclosure to Wing FTP that resulted in model 7.4.4 being launched on Might 14, 2025.
Nevertheless, exploitation makes an attempt started instantly after the technical write-up grew to become public, with Huntress safety researchers observing the primary assaults on July 1, 2025.
CVE-2025-47812 stems from improper dealing with of null bytes in Wing FTP Server’s internet interface, particularly within the loginok.html endpoint that processes authentication requests.
The vulnerability combines a null byte injection flaw with Lua code injection, permitting attackers to bypass authentication checks and inject arbitrary instructions into server session recordsdata.
The assault begins with a malformed HTTP POST request to loginok.html containing a specifically crafted username parameter. By inserting a null byte (%00) adopted by Lua code, attackers can manipulate the server’s session creation course of.
When the server processes these corrupted session recordsdata, the injected Lua code executes with elevated privileges, granting attackers full management over the system.
Safety researchers at Huntress created a proof-of-concept exploit demonstrating how the vulnerability may be leveraged to attain arbitrary code execution as root on Linux techniques or SYSTEM on Home windows.
The assault is especially harmful as a result of it may be executed through nameless FTP accounts, that are disabled by default however could also be enabled in some configurations.
Widespread Web Publicity
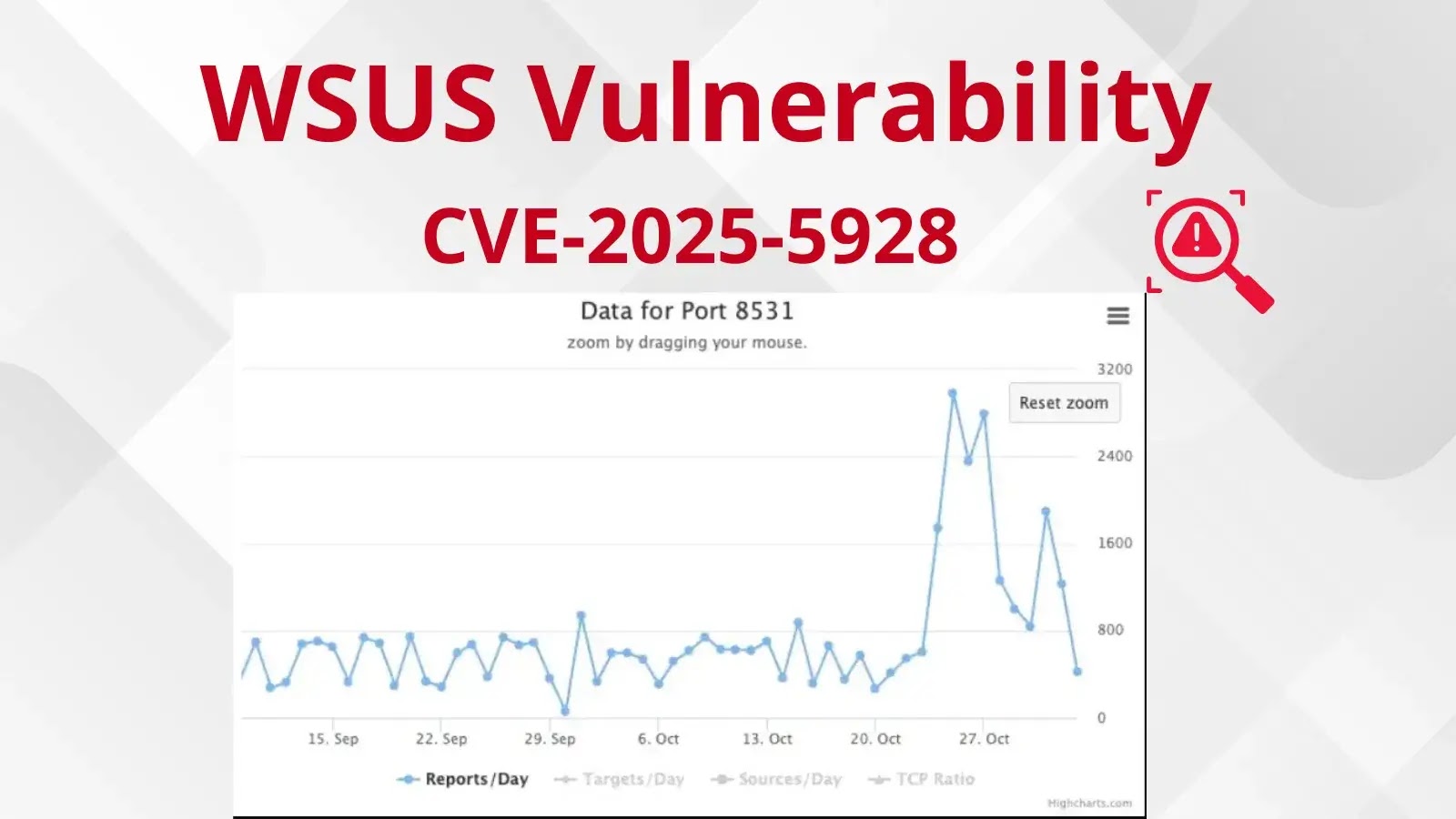
In accordance with information from Censys, roughly 8,103 publicly accessible gadgets are working Wing FTP Server worldwide, with 5,004 of those techniques exposing their internet interfaces to the web.
The Shadowserver Basis has recognized round 2,000 IPs working uncovered Wing FTP Server situations, although particular vulnerability checks haven’t been carried out on all recognized techniques.
shadowserver basis outcomes
The geographic distribution reveals the very best concentrations of doubtless susceptible techniques in the US, China, Germany, the UK, and India.
Organizations utilizing Wing FTP Server for file switch operations embody main firms similar to Airbus, Reuters, and the U.S. Air Power, indicating the potential for important affect throughout crucial infrastructure sectors.
Noticed Assault Exercise
Huntress researchers documented lively exploitation starting July 1, 2025, with menace actors focusing on a buyer’s Wing FTP Server set up.
The assault concerned 5 distinct IP addresses making an attempt to compromise the identical system inside a brief timeframe, suggesting coordinated scanning and exploitation efforts.
The noticed assault sequence included:
Preliminary reconnaissance utilizing instructions like ipconfig, arp -a, and nslookup
System enumeration by way of whoami, internet consumer, and PowerShell scripts
Creation of recent consumer accounts for persistence
Makes an attempt to obtain and execute distant malware utilizing certutil and curl
Efforts to put in distant entry instruments, together with ScreenConnect
Whereas the particular assault failed, seemingly as a result of intervention by Microsoft Defender or attacker inexperience, the incident demonstrates the vulnerability’s lively exploitation within the wild.
Wing FTP Server model 7.4.4, launched on Might 14, 2025, addresses CVE-2025-47812 together with two different safety vulnerabilities (CVE-2025-47813 and a path disclosure problem). The seller has reportedly contacted prospects through e-mail with improve steering following the disclosure of lively exploitation.
For organizations unable to instantly improve, safety researchers advocate implementing interim protecting measures together with:
Disabling or limiting HTTP/HTTPS entry to the Wing FTP internet portal
Disabling nameless login performance
Monitoring session directories for suspicious .lua recordsdata
Implementing community segmentation to restrict publicity
The vulnerability impacts all main working techniques supported by Wing FTP Server, together with Home windows, Linux, and macOS. Given the software program’s widespread deployment in enterprise environments for safe file switch operations, the safety neighborhood has issued pressing suggestions for instant patching.
Organizations working Wing FTP Server installations ought to prioritize upgrading to model 7.4.4 or later, conduct thorough safety assessments of their file switch infrastructure, and implement further monitoring to detect potential compromise indicators.
The mix of most severity ranking, lively exploitation, and widespread web publicity makes this vulnerability a big menace to organizational safety posture.
Examine stay malware habits, hint each step of an assault, and make sooner, smarter safety selections -> Attempt ANY.RUN now