ClickFix just isn’t a malware, however a really profitable social engineering method. It primarily depends on MFA verification fatigue and pretend CAPTCHA pages to silently set up malware.
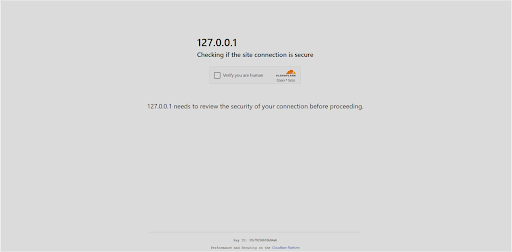
Researchers have found and analyzed a ClickFix assault that makes use of a pretend Cloudflare ‘humanness’ verify. The Cloudflare verify is named Turnstile and has changed the sooner Cloudflare CAPTCHA course of consistent with an industry-wide migration towards frictionless safety.
Cloudflare is a widely known and extensively used service designed to enhance the safety and efficiency of internet sites. Most web customers could have come throughout a Cloudflare Turnstile problem en path to a web site and won’t be shocked to see one. Turnstile operates by working non-intrusive JavaScript challenges to confirm human exercise.
On this instance, the pretend Turnstile web page is an correct clone of the real Cloudflare web page, a pixel-perfect copy, together with the Cloudflare emblem and the Ray ID footer (reminding the consumer that nothing is amiss since it is a legit safety verify).
However it isn’t legit. By accessing the pretend web page, a malicious however hidden background course of is launched. A PowerShell command is loaded into the consumer’s clipboard. Then, when the consumer checks the “Confirm you’re human” field, a pop-up requests extra consumer steps. Nothing is overtly malicious, and the extra steps are simply accepted as a part of the verification course of.
The consumer is instructed to sort Win+R adopted by CTRL+V adopted by Enter. The primary opens the Home windows ‘Run’ dialog field, the second copies the clipboard content material (preloaded with a PowerShell command), and the third runs the command.
The PowerShell command fetches malware from a distant server and sometimes executes it in reminiscence. Until extra controls are in place, antivirus and endpoint safety merchandise would in all probability not detect something doubtful in a Home windows command. “Due to their restricted visibility into browser conduct, AV merchandise and different endpoint safety options are inclined to miss these assaults,” explains Lionel Litty, chief safety architect at Menlo Safety.
The assault contains “a mix of social engineering and Residing off the Land Binaries (LoLBins) which makes it tough to defend towards – the consumer merely launches PowerShell instructions quite than a malicious binary that may be detected by an EDR resolution,” provides James Maude, subject CTO at BeyondTrust.
On this pattern, the one clue that it would probably be a rip-off might be seen within the pop-up field and the wording of “CloudFlare Problem”. Cloudflare doesn’t use an uppercase ‘F’ in its branding, however few customers would discover this of their haste to get by way of the verification course of. Verification fatigue is actual and applies in lots of areas of life. If people get too many warnings with out seeing any justification for the warnings, they begin to ignore them.
“Campaigns utilizing ClickFix have delivered a wide range of payloads on this method – from info-stealing malware like Lumma and Stealc to full distant entry trojans (RATs), which let attackers take management of a sufferer’s system like NetSupport Supervisor,” say the researchers.Commercial. Scroll to proceed studying.
The pretend Turnstile web page might be delivered, and focused, by a wide range of strategies. Malvertising or social media lures might be designed to draw particular teams – reminiscent of healthcare employees – to go to a phishing web site; whereas compromised however legit or utterly pretend web sites can merely anticipate guests utilizing a standard drive-by method.
“Cloudflare is without doubt one of the most impersonated providers in phishing assaults. That’s largely as a result of it presents a free tier that attackers exploit to obscure threats,” explains J Stephen Kowski, subject CTO at SlashNext E-mail Safety. “These screens are sometimes acquainted to customers – like Google CAPTCHA or Cloudflare’s human verification – in order that they decrease suspicion whereas the true malicious content material masses within the background or is sideloaded regionally.”
Simply as Turnstile delivers frictionless safety, so ClickFix delivers frictionless crime.
Associated: Russia-Linked APT Star Blizzard Makes use of ClickFix to Deploy New LostKeys Malware, Google Warns
Associated: Lazarus Makes use of ClickFix Ways in Pretend Cryptocurrency Job Assaults
Associated: ClickFix Extensively Adopted by Cybercriminals, APT Teams
Associated: Microsoft Warns of Hospitality Sector Assaults Involving ClickFix